Thwarting GandCrab in the New Era of Agile Computer-Jackers

New Bitdefender decryptor can be deployed across the network to automate recovery
In January of last year, a new family of ransomware started spiking on the global threat map. Spreading through e-mail attachments and exploit kits, the new contender in the ransomware underworld managed to take more than 50,000 computers and servers hostage, demanding varying sums of money for the decryption key.
Ransom demands varied widely and infection mechanisms often differed, steering observers to a grim conclusion: GandCrab was offered as a service, with disperse affiliates handling the proliferation, pricing and alliances with other criminal teams.
Bitdefender released the first decryptor a year ago - on February 28th 2018 - to help more than 50,000 victims get their data back for free. Just five days later, GandCrab operators were rolling out new samples to affiliates, demonstrating the dangerous agility of managed ransomware-as-a-service.
Throughout the year, GandCrab operators adopted agile development techniques to cope with their ever-growing pool of victims, as well as to counter the decryptors released by Bitdefender.
But the rapid succession of new versions was not the only change in the GandCrab business model.
As of late 2018 and early 2019, GandCrab has radically updated its spreading mechanisms and affiliation opportunities, and improved its resilience against most cyber-security solutions, leading to massive epidemics that have made it one of the largest players in the ransomware space with a market share of nearly 50%.
For instance, some GandCrab affiliates started attacking organizations via exposed Remote Desktop Protocol instances or by directly logging in with stolen domain credentials. After authenticating on a compromised PC, attackers manually run the ransomware and instruct it to spread across an entire network. Once the network is infected, the attackers erase their traces and contact the victim with a demand.
But probably the most spectacular development in the way affiliates target victims is the targeting of managed service providers to use their reach inside companies to automate the deployment of ransomware. Once they have infected the network, they wipe logs and traces of their presence and ask for ransoms of approximately $10,000 per company computer:
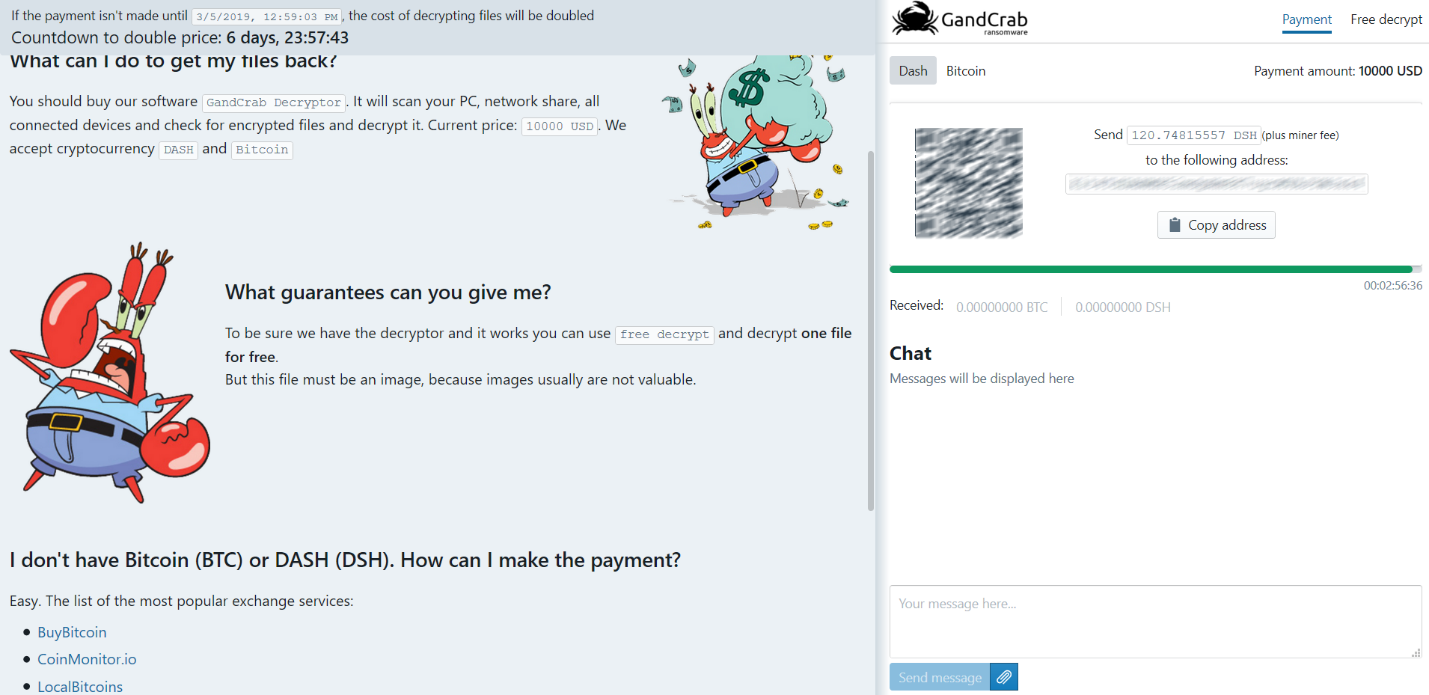
Since we released the free utility, we have helped system administrators and home users decrypt more than 20,000 servers and home computers and avoid paying at least 24 million dollars in ransom. The tool, available for free on Bitdefender Labs, supports network-based deployment via the most popular deployment technologies in the MSP space.
If you have already suffered an infection with ransomware, Bitdefender and its partner law enforcement agencies advise victims to not give in to the demands of ransomware operators. Instead, they should back up the encrypted information and notify police immediately. Ransomware decryptors, such as those released by Bitdefender and other contributors to the No More Ransom project, could get you your data back without paying attackers significant amounts of money in return.
If your organization has not been hit by ransomware, consider this an opportunity to take action before it’s too late. To prevent ransomware infections, users should implement a security solution with layered anti-ransomware defenses, regularly back up their data and avoid opening attachments delivered with unsolicited messages.
{{cta('6af19fed-7a54-4847-a8e1-d9470e6118b6','justifycenter')}}
tags
Author
Bogdan Botezatu has spent the past 12 years as Director of Threat Research at Bitdefender. His areas of expertise include malware deobfuscation, detection, removal and prevention. Bogdan is the author of A History of Malware and Botnets 101. Before joining Bitdefender, he worked at one of Romania's largest and oldest universities as network administrator in charge of SecOps and policies.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks