Top 10 Security Risks: Vulnerabilities, Misconfigurations, and User Behavior to Avoid

Today, cybercriminals are more sophisticated than ever and tend to exploit the weakest point of organizations to gain unauthorized access to their systems. Any vulnerabilities or misconfigurations provide an easy entry point for attackers. As a result, the security posture of any organization is only as strong as its weakest link.
According to the latest ENISA (European Union Agency for Cybersecurity) Threat Landscape (ETL) report, the yearly growth of exploitation of vulnerabilities was the most common cause of security incidents at 33%. Vulnerabilities are crucial in national cybersecurity strategies, and global leaders are just starting to recognize how important addressing software vulnerabilities is. Governments in both the European Union (NIS2 Directive) and the United States (the US National Cybersecurity Strategy) are working to address the problem of software vulnerabilities. Although the extent of incentivization (carrot) and penalization (stick) is uncertain, it is evident that both regulations strive to promote greater responsibility and security resilience.
Learning about misconfigurations, user behavior risks, and vulnerabilities is crucial for maintaining the security and integrity of the data and systems at any organization. Understanding these factors helps organizations and individuals mitigate risk and helps fulfill requirements imposed by compliance and regulatory frameworks.
Anatomy of risks
Attackers today use various techniques to discover vulnerabilities that put public applications or victim networks in jeopardy. One common way used by hackers is to run one of the many automatic scanners available on the market.
Using a fully featured application, attackers scan the target network and receive data in graphical form with all the necessary information. The application presents detailed information about IP addresses, operating systems, application versions, discovered vulnerabilities, and a detailed view of available exploitation techniques. Within seconds, cyber criminals can decide which available technique to launch to compromise the targeted system.
Another approach is to start with an exploitable vulnerability, then opportunistically locate vulnerable systems accessible from the Internet. We have seen an increase in attacks using this formula, targeting popular software like Microsoft Exchange, VMware ESXi, or ManageEngine. Initial compromise can be just the start of a complex operation, as these opportunistic attacks often lead to a supply chain compromise.
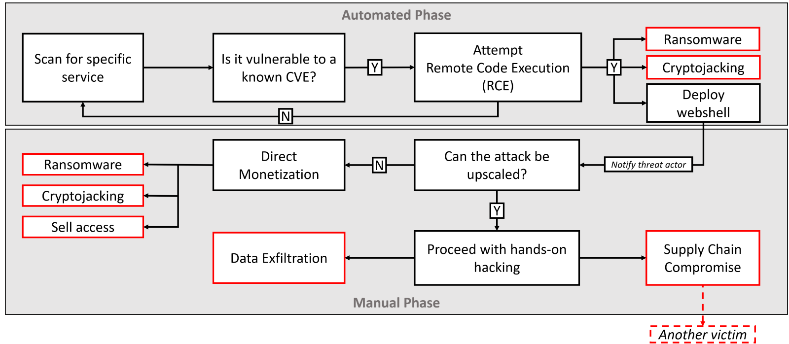
One of our previous blogs describes the “new” winning formula for threat actors
The rise in automated tools suggests that numerous cybercriminals exploit Common Vulnerabilities and Exposures (CVEs). CVE Details page includes a list of CVEs with information about applications affected, scoring (how serious the risk is), and remediation steps. However, not all businesses patch quickly, which leave threat actors with thousands of well-known vulnerabilities. We are still finding Exchange servers exposed to the internet with the CVE-2021-34473 and CVE-2021-26855 flaws (Remote Code Execution), for which patches were available in March and April 2021.
Enhancing protection
All of this leads to the conclusion that IT specialists must understand the assets they have, the possible risks, and minimize the attack vector. To build strong cybersecurity resilience, we should define diverse types of vulnerabilities:
- Network vulnerabilities: Weaknesses in hardware and operating systems (OS) that can expose the network to attackers. One of the common risks is using unpatched firewalls or unprotected Wi-Fi networks.
- Operating system and application vulnerabilities: These can cause damage, for example, by running additional code, and letting attackers take control of the system.
- Process and human vulnerabilities: These are created by an administrator or user's risky behavior related to misconfiguration or weak password policies.
Installing a patch or upgrading software to a newer version without vulnerabilities are the only forms of risk response that can eliminate vulnerabilities without removing functionality (NIST). Cybersecurity and Infrastructure Security Agency (CISA) and National Security Agency (NSA) released Enduring Security Framework (ESF) guidance documents on Identity and Access Management recommending software patches and vulnerability scanning as best practices for network hardening and security assessment.
To know what must be patched, security specialists need visibility and must know what is commonly exploited and where they made a mistake during the configuration.
Bitdefender Labs observation
For this report, we have used data from the Bitdefender Labs telemetry on potential vector attacks. We divided this report into three categories: misconfiguration, user behavior, and vulnerabilities.
Misconfiguration top risks
Print Spooler Service Exploitable – Print Spooler service is responsible for print jobs sent from the computer to the printer or print server. Microsoft has acknowledged a vulnerability in the service (CVE-2021-34527 also known as a PrintNightmare) which can open a door for attackers. On any Windows installation running vulnerable print spooler service, rogue users can execute code with SYSTEM privileges. An attacker can install any program, modify, or delete the data and create new accounts with full user rights. It is recommended to verify if the servers and endpoints are fully updated. This service should be disabled when its functionality is not required (for example server workloads).
Internet Explorer: Java permissions (Local Machine Zone) - This policy setting allows the management of permissions for Java applets. Java applications may contain malicious code that could deliver a payload to the victim. The Java Applet Attack is one of the most successful and popular methods used in social engineering techniques. Hackers and rogue users can easily find applications and dozens of video tutorials on cloning a web portal, weaponizing Java applets, and establishing a Command & Control (C&C) tunnel to the victim's computer. Having access to the computer, attackers can execute any command, install an application, or execute ransomware. To improve the cybersecurity posture, administrators should disable this functionality on all computers in the corporate network.
WinRM Service – Windows Remote Management is the name of the Windows service and protocol. It may be called by winrm command and allows for local and remote administration of Windows computers sending management commands over HTTP or HTTPS. The administrators can use scripts to automate the management of the servers and obtain data for management applications. The adversaries also may use WinRM to execute a payload on a remote host, for example using the Cobalt Strike tool. Service should be disabled unless it is necessary and used by the administrators, then should be separated with dedicated accounts and permissions. Administrators should use HTTPS instead of HTTP when connecting to WinRM and restrict access to the service from dedicated IP addresses. Also, a strong password should be used to avoid brute-force attacks in the system. When administrators do not use the service for remote management service should be disabled.
Internet Explorer: Logon options (Restricted Sites Zone) - Legacy Internet Explorer had five different Security Zones to simplify the configuration for administrators. A restricted Zone could contain all the sites that the administrator does not trust. The Logon option allows managing settings for logon like anonymous login, prompt for username and password, automatic logon only in Intranet zone and automatic logon with current username and password. For the restricted zones, users accidentally can submit their credentials to applications operated by threat actors trying to impersonate legitimate servers. Crooks using the phishing campaign could convince the user to open a page from an enclosed link in the message. The secure recommendation is to configure the use of an Anonymous login. Legacy Internet Explorer had five different Security Zones to simplify the configuration for administrators. A restricted Zone could contain all the sites an administrator does not trust. The Logon option allows managing settings like anonymous login, prompt for username and password, automatic logon only in Intranet zone, and automatic logon with current username and password. For the restricted zones, users can accidentally submit their credentials to applications operated by threat actors trying to impersonate legitimate servers. Crooks using the phishing campaign could convince the user to open a page from an enclosed link in the message. The secure recommendation is to configure the use of an Anonymous login.
Internet Explorer: Initialize and script ActiveX controls not marked as safe (Trusted Sites Zone) - Active Scripting know as ActiveX controls can load and run any parameters and script without checking if they are safe or untrusted. The script is executed in the memory, does not make any changes on the disk, and can try to bypass detection capabilities on the endpoint security products. Script written in one of the popular languages like VBA, Perl can execute malicious code to provide initial access to the victim’s computer to initiate backdoor communication, collect information, and encrypt files. All ActiveX controls not marked as safe should not be executed.
Internet Explorer: Allow drag and drop or copy and paste files (Restricted Sites Zone) - For each zone, the administrator can control how users can drag and drop or copy and paste the files. This misconfiguration could make it possible to put weaponized files on the user's computer when visiting malicious websites. When the administrator disables this policy, it prevents users from downloading untrusted files, or through the prompt settings notify users to choose the action. Content hosted on Restricted Sites Zones should be blocked.
Internet Explorer: Include local path when user is uploading files to a server (Restricted Sites Zone) - When the user uploads files via HTML form he can also send information about the local directory path where the file is located. Depending on the file location some information like username may be unintentionally revealed. Option should be disabled for all the users in the corporate network.
Internet Explorer: Allow scripting of Internet Explorer WebBrowser controls (Restricted Sites Zone) - The WebBrowser control has several properties, methods, and events, that can be used to implement controls in Internet Explorer via script. The script may include unmanaged code which cannot be prevented from running. The WebBrowser was designed to work in full trust only. It is a similar misconfiguration as described above in Internet Explorer: Java permissions. To improve cybersecurity posture, administrators should disable this functionality.
Internet Explorer: Java permissions (Internet Zone) - It is a similar misconfiguration as described above in the Internet Explorer: Java permissions section. Java applications may contain malicious code. Low Safety configuration enables applets to perform all operations. To improve cybersecurity posture, administrators should disable this functionality.
Internet Explorer: Allow scriptlets (Restricted Sites Zone) - Scriptlet is a reusable Component Object Model which includes a piece of code e.g., Java embedded in HTML which means it can be used for any action on a Web page. The scriptlets located in Restricted Sites may contain malicious code. To improve cybersecurity posture, administrators should disable this functionality.
User behavior top risks
Old User Password – Verification if the user has not changed the password for the local or domain account for more than 90 days. Keep in mind that mandatory password changes can do more harm than good, and require careful balancing. Users forced to change passwords frequently can keep them on a piece of paper or finally make it less complicated and easier to brute force. NIST in the Digital Identity Guidelines recommends password changes only on user request or evidence of authentication compromise. Microsoft also does not recommend mandatory periodic password resets for user accounts. We recommend using strong password policies and multi-factor authentication.
Password does not expire – Verification of the “Password does not expire” attribute. As mentioned above, Microsoft and NIST do not recommend mandatory periodic password resets for user accounts. We recommend using strong password policies and multi-factor authentication.
Low password complexity policy – Based on Microsoft recommendations, passwords should keep a minimum of 14 characters containing upper and lowercase characters and non-alphanumeric characters. Users should not use common or obvious passwords. In one of our previous blogs, we shared the list of common credentials which were used on dictionary attacks in IoT (Internet of Things) infrastructure.
Password not required – This parameter can cause a security gap inside the organization. User accounts with blank passwords can be easy for attackers to compromise. Blank passwords without strong visibility in the organization could be extremely difficult to find. Administrators should create accounts with strong passwords only.
High Detection Count – Identifies users who frequently encounter security threats and generate alerts. By using this method, administrators can pinpoint individuals within the organization who may have inadequate knowledge regarding security and provide them with security awareness training.
Brute Force RDP (Remote Desk Protocol) Source - An alert is generated when the number of failed RDP connection attempts is noticed in a short period. It can indicate that a brute force attack was initiated from the user account.
Samba PlainText/LM/NTLM authentication – Plain text passwords sent over the network can be retrieved from the TCP packets using packet sniffers or basic tools like Wireshark. NTLM and NTLMv2 authentication are vulnerable to various malicious attacks, including SMB replay, man-in-the-middle attacks, and brute force attacks. Reducing and eliminating NTLM authentication from your environment forces the Windows operating system to use more secure protocols, such as the Kerberos version 5 protocol, or different authentication mechanisms, such as smart cards (Microsoft).
Shared HTTP Password External – This mechanism checks if the users apply the same password between internal and external applications. Unique passwords should be utilized for each application to minimize the risk in case one of the servers was compromised and credentials were stored. According to the 2022 Verizon Data Breach Investigation Report, 80% of web application attacks were using stolen credentials. When the user has the same credentials on several applications, in case one of the servers suffers a data breach the attackers can use those data to gain access to another application. Hackers may use stolen passwords to authenticate several applications using dictionary attacks (a type of brute force attack).
Browsing Infection – Verification of user behavior and access to any malicious URL. Like with High Detection Count, this can help administrators to identify employees contributing to cybersecurity risks inside the organization.
Public Wi-Fi connection – This alert is generated when the user connects to unprotected Wi-Fi with no security on the access point. On the user side with Windows computers, the system notification should also be raised each time when they connect to a Wi-Fi network which uses WEP or TKIP for security.
Vulnerabilities top risks
Log4j related vulnerabilities were in the spotlight last year, but our top detections are another clear reminder of the importance of keeping systems up to date with the latest security patches while also employing strong perimeter defense. Attackers don't need to scour for new exploits or novel techniques when they know that many organizations are vulnerable to older exploits due, in part, to the lack of proper patch management and risk management.
CVE-2022-23302 – JMSSink in all versions of Log4j 1.x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to.
CVE-2022-33915 - Versions of the Amazon AWS (Amazon Web Services) Apache Log4j hotpatch package before log4j-cve-2021-44228-hotpatch-1.3.5 are affected by a race condition that could lead to a local privilege escalation.
CVE-2020-9488 – Improper validation of certificate with host mismatch in Apache Log4j SMTP appender. This could allow an SMTPS connection to be intercepted by a man-in-the-middle attack which could leak any log messages sent through that appender.
CVE-2019-17571 - Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code.
CVE-2022-23305 - By design, the JDBCAppender in Log4j 1.2.x accepts an SQL statement as a configuration parameter where the values to be inserted are converters from PatternLayout. The message converter, %m, is likely to always be included. This allows attackers to manipulate the SQL by entering crafted strings into input fields or headers of an application that are logged allowing unintended SQL queries to be exe.
CVE-2022-23307 - Identified a deserialization issue that was present in the Apache Chainsaw component of Log4j 1 can lead to malicious code execution.
CVE-2020-9493 - A deserialization flaw was found in Apache Chainsaw versions prior to 2.1.0 which could lead to malicious code execution.
CVE-2022-29072 - 7-Zip through 21.07 on Windows allows privilege escalation and command execution when a file with the .7z extension is dragged to the Help>Contents area. This is caused by the misconfiguration of 7z.dll and a heap overflow.
CVE-2009-2409 - The Network Security Services (NSS) library before 3.12.3, as used in Firefox; GnuTLS before 2.6.4 and 2.7.4; OpenSSL 0.9.8 through 0.9.8k; and other products support MD2 with X.509 certificates, which might allow remote attackers to spoof certificates by using MD2 design flaws to generate a hash collision in less than brute-force time.
CVE-2020-36518 - jackson-databind before 2.13.0 allows a Java StackOverflow exception and DOS (Denial of Service) via a large depth of nested objects.
Key findings and solutions
In conclusion, vulnerability management is a continuous process of identifying, classifying, prioritizing, and remediating vulnerabilities. Patches can also interfere with productivity by slowing down or interrupting primary business functions. This is one of the reasons why the security team should create a patch management policy. We must remember many companies struggle with the lack of security specialists who can be dedicated only to security tasks. Therefore, the process should be fully automated, allowing even a single administrator to discover potential vulnerabilities, manage patches, and monitor for new patches and vulnerabilities.
Not only vulnerabilities can lead to the incident but also misconfiguration and user behaviors. Open services and weak or blank passwords can be easily used by attackers as initial access to the corporate network. Administrators should be able straightforwardly to find and remediate any potential security gap in the organization to minimize security gaps.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide, helping organizations reduce their risk of exposure and improve their digital experience. With Bitdefender GravityZone which includes Risk analysis, the customers get unified security and risk analytics platform.
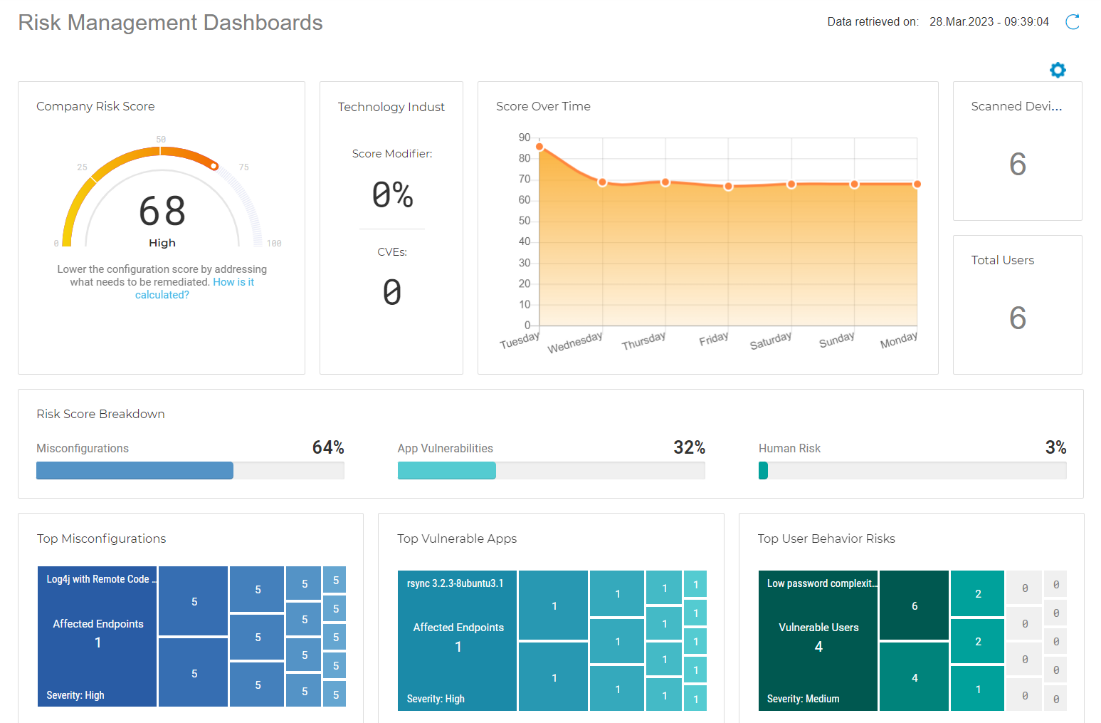
With the GravityZone platform, organizations can effectively manage the risks posed by vulnerabilities, security misconfigurations, and human error. The Risk Analytics feature, combined with its integrated Patch Management add-on module, provide a comprehensive, easy-to-use, solution to help organizations identify, manage, and eliminate all potential threat vectors that could be exploited by hackers. Together with add-on XDR (eXtended Detection and Response) mechanisms, security specialists can measure cyber security posture even with zero-day vulnerabilities.
Learn more about Bitdefender GravityZone to assist with mitigating and identifying cyber risks.
tags
Author

Grzegorz Nocon is a graduate of the Faculty of Physics at the University of Silesia. With over 16 years of experience in the IT industry, he currently works as a Technical Marketing Engineer at Bitdefender. A strong supporter of a holistic approach to security and passionate about solving security problems in a comprehensive and integrated way. Outside of work, an avid CrossFit enthusiast and a lover of fantasy literature.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











