When They ATT&CK, We Will D3FEND | Business Insights Bitdefender

On June 22nd, MITRE released a new framework called D3FEND to complement the industry-recognized ATT&CK matrix. The new framework, sponsored by the NSA, aims to create a foundation for identifying components and capabilities of security defenses. MITRE is not a private non-profit organization; it is a federal research and development organization.
D3FENSE is not just a knowledge base of defensive techniques. It is a knowledge graph, a catalog of generalized defensive techniques and their relationships to adversary methods.
The opportunity of defeating the enemy is provided by the enemy himself - Sun Tzu
To understand D3FEND, we need to start with the basic organization of the "knowledge graph of cybersecurity countermeasures" (see image). At the core of the framework, there are five "tactics" – Harden, Detect, Isolate, Deceive and Evict. If the "tactics" tell us WHAT the defenders plan to achieve, "techniques" tell us HOW it is achieved. There are 17 top-level techniques, such as "File Analysis" or "Application Hardening". Under the base techniques, there are almost 100 sub-techniques that include additional insights - definition, how it works, considerations, links to the patents, and more. D3FEND framework is at an early stage. It is still an experimental project – the initial release is not comprehensive, and MITRE will probably further expand this list.
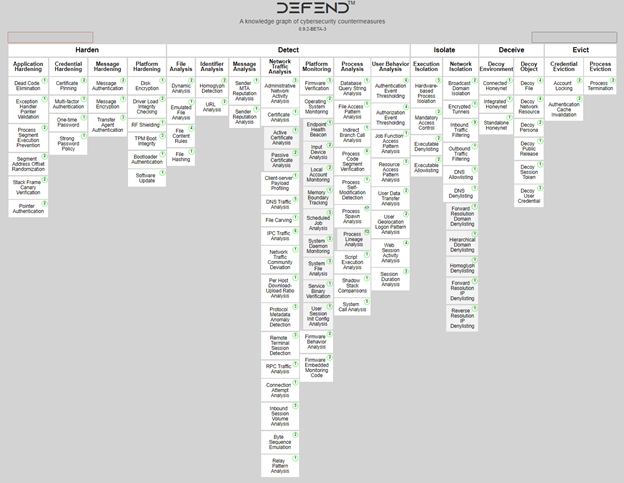
With ATT&CK, we know what threats to address. With D3FEND, we understand how to address them. D3FEND is complementing the ATT&CK framework, not replacing it.
To support mapping between the ATT&CK and D3FEND frameworks, MITRE introduced the concept of "digital artifacts." Think about it from the perspective of archeology – an artifact exists thanks to the adversary's actions (like file, email, or process). For example, when attackers perform a scan of your environment, they produce digital artifacts. When an adversary sends a phishing email, it results in digital artifacts on both the origin and destination systems (along the way). For D3FEND framework, it is not important if digital artifacts are observed or even accessible (e.g. outbox of adversary) – it is only important they have once existed somewhere.
Digital artifacts are the glue that ties the offensive and defensive models together. They are opportunities for defenders to prevent, detect, isolate, deceive or evict the attackers. This is the core of the D3FEND framework – a knowledge graph, a way to map offensive and defensive techniques together in one coherent picture.
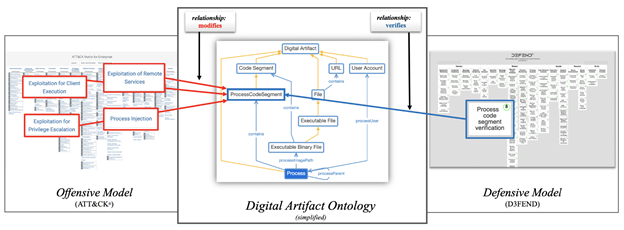
This mapping makes it especially useful for reviewing existing security controls. It is a map for defense in depth. You can review the existing portfolio of security tools to confirm that all core tactics are covered and make sure that you are prepared to detect artifacts generated by adversaries. This is multi-layered security, implemented from another perspective.
"Meow" means "woof" in cat - George Carlin
What is maybe even more interesting is that the D3FEND framework has the potential to change how we talk about security controls. It can help to standardize the vocabulary that we use to describe defensive technology.
The security industry is known for its use of acronyms and vocabulary descriptions. So much that analyst firms have to produce new taxonomy each year, often with modest technical changes. With over 5,000 companies in the cybersecurity defense market, each adding new jargon to the security landscape, adversaries often have an advantage.
By breaking down the security products into their capabilities and using predictable naming, D3FEND can help blue teams to base their buying decisions on capabilities, not on vendor claims. With less confusion, security teams are better able to provide maximum protection to their users and data.
D3FEND can make industry jargon easier to understand – and remove the barrier that prevents many people from starting a career in cybersecurity. The lack of a common language has been plaguing our industry for a long time. A common framework could remove this barrier.
The road to hell is paved with good intentions - Samuel Johnson
We have been talking about what D3FEND is. But it is equally important to explain what it is not. D3FEND does not prioritize security countermeasures, nor does it comment on their effectiveness. Like the ATT&CK framework, it is open to interpretation by various security vendors (we've blogged about decoding MITRE ATT&CK evaluations before).
There are some cautionary considerations when it comes to D3FEND. Suppose the D3FEND framework is widely adopted by cybersecurity vendors but becomes more of a "checkbox" exercise. By vendors trying to include as many D3FEND items as possible – without really solving the security challenges, the result will be mediocre quality. Therefore, it will continue to be important to remember that not all security solutions are equal – and using independent sites (such as AV-TEST or AV-Comparatives) to validate vendor claims can be even more critical than today.
But the good news for validation is that we also have the ATT&CK framework to measure things like detection. By mapping to ATT&CK framework techniques, it will become easier to validate claims by security vendors. Breaking down products into capabilities makes it easier for buyers to validate how adequate the security controls are. This makes it easier to compare claims across multiple products with common defensive taxonomy. Instead of looking at "all in one" solutions, a better approach may combine the best ATT&CK-validated security controls.
Unifying the language of our industry can also help with data collection and analysis. Reading some cybersecurity brochures is a daunting task even for human intelligence and far out of reach for current natural language processing models. Data input normalization could speed up data processing – and one day, we may even get a correlation between MITRE D3FEND and the Verizon Data Breach Investigations Report. I would love to see a heatmap of security controls and their applicability to real-life attacks.
Conclusion
D3FEND appears to be helpful as a knowledge base, but it's more important as a knowledge graph. It's a catalog of defensive cybersecurity techniques and their relationship to attack techniques. It does not prioritize them - nor does it comment on their effectiveness. Its primary goal is to help standardize the vocabulary that describes security components and capabilities, and we think it's a great asset for the industry moving forward. As vendors adopt this common body of language, organizations will be better positioned to understand what security controls are provided and deployed.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











