XDR: The Latest TLA or Newest Cyber Shield?

The cybersecurity industry is full of three-letter acronyms (TLAs). Often, they are simply a new marketing spin on an existing technology. Now, the market is a buzz with XDR - or extended detection and response solutions as the next set of effective offerings that focus on extending observability, detection, and response capabilities to stay ahead of the ever-changing threat landscape
As we saw at the recent RSA Conference, it seems to be on everyone’s radar.
Analysts forecast the XDR market to grow from $985M in 2022 to $2,358M in 2027, a CAGR of 19.1%. But XDR is not simply another acronym – it provides real benefits to overburdened cybersecurity teams and greater protection against threats in today’s increasingly distributed business environments.
Though many cybersecurity vendors are jumping on the XDR bandwagon, few companies have intentionally designed and purpose-built a holistic, native XDR solution as Bitdefender has. Instead, most have cobbled together a variety of security tools, including endpoint detection and response (EDR) technologies and security information and event management (SIEM) solutions, and call it XDR. But this approach cannot deliver the benefits of a purpose-built XDR solution, such as a unified detection layer with built-in response capabilities and an integrated user experience.
Sifting through the alphabet soup: EDR vs. MDR vs. XDR
EDR and managed detection and response solutions (MDR) are both important security options and each have their benefits. By monitoring all the endpoints throughout an organization – such as desktops, workstations, smartphones, and servers – EDR solutions effectively cover the points where most attacks occur. From phishing attempts to employees unintentionally downloading malware, most attacks find their way into an organization through an endpoint of some sort.
EDR solutions provide a detection layer that analyzes the telemetry and events coming from the endpoints, performs analysis, and flags it to the security team if it’s determined to be an incident. MDR services do the same for their customers, while also adding the benefit of 24x7 monitoring by skilled security analysts who can also triage incidents and carry out investigations.
EDR and MDR both deliver important benefits to organizations, but XDR takes detection and response to the next level.
The benefits of XDR
Having evolved from EDR solutions, XDR provides greater coverage for an organization by incorporating telemetry and event information from a far wider set of sources. XDR extends coverage beyond the endpoints to include data from sensors and sources throughout the network, such as adding telemetry from specific systems like identity and authentication systems, productivity tools (e.g Office 365), and even systems in the cloud.
But there is a lot more to XDR than simply adding data sources.
Here are five key aspects organizations should look for in a purpose-built, native XDR solution:
A shared detection layer
One of the most important differentiators between a true XDR solution and a collection of security tools that have been simply repackaged an XDR, is a shared detection layer. As mentioned above, some security vendors will bundle together a detection tool for endpoints, one for the network, a separate response tool, and call it an XDR solution. What’s more, some vendors will expect their customers to integrate these various products and detection logic needed for incident management, which simply increases the workload on the security staff.
A true XDR solution should have a shared detection layer that spans all sensors and data sources throughout the organization. Only a unified XDR platform built on a shared detection layer can enable organizations to identify threats at various stages in the attack-kill chain, cross-correlate data from different sources, and gain a greater understanding of the incident. Additionally, Bitdefender XDR provides built-in response capabilities at any point that the threat is identified, enabling security analysts to perform their job more efficiently and effectively.
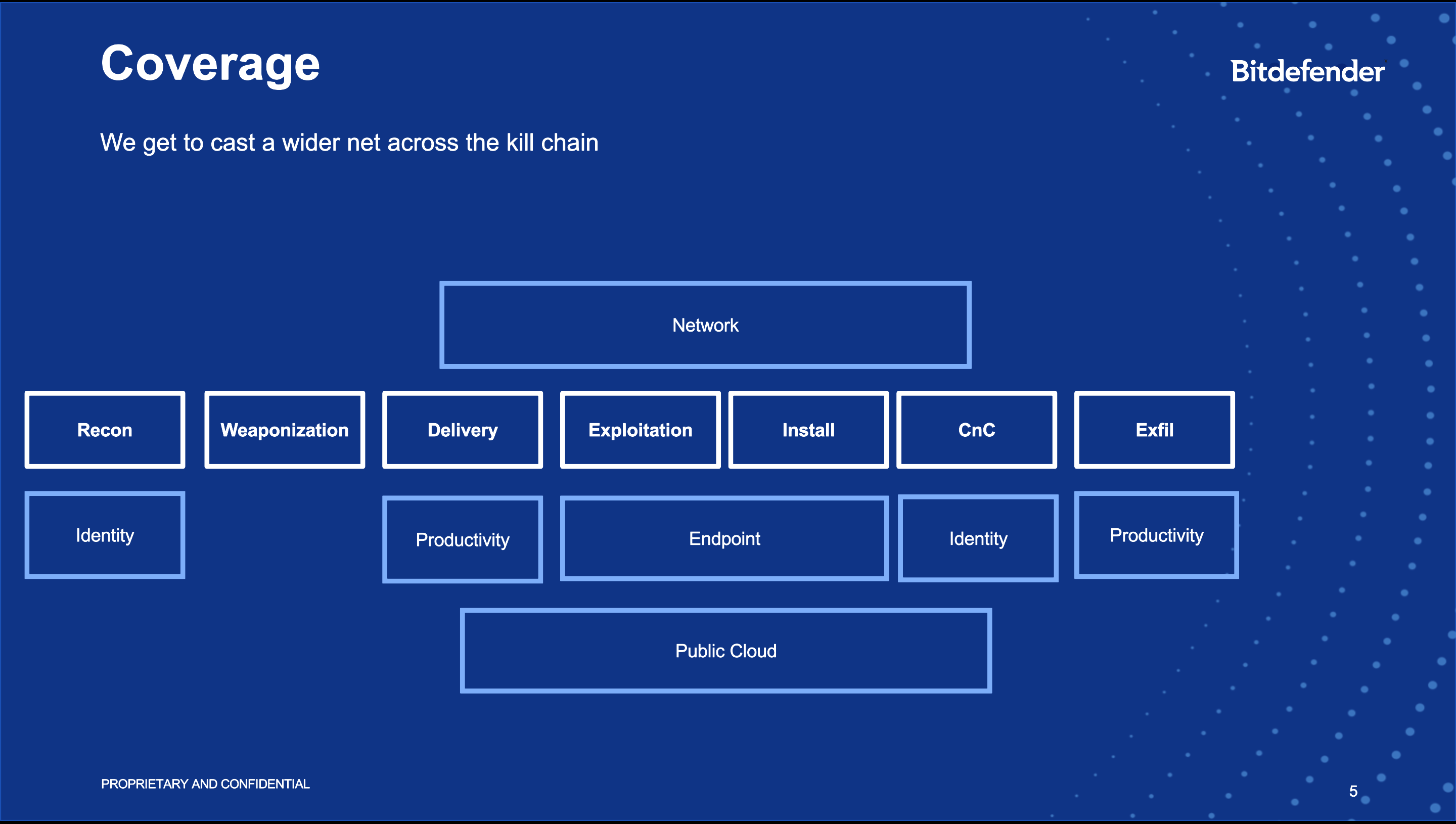
Coverage throughout the attack kill chain
Due to the shared detection layer, security teams can detect threats and intervene at any point in the attack-kill chain.
For example, with EDR solutions, security teams can only identify an attack at the exploitation and install portion of the kill chain, which take place on the endpoints. But with XDR, security teams can move much further up the kill chain to identify attacks earlier. They can identify attacks that are still in the early reconnaissance stage, for example, where an attacker might be testing an organization’s authentication system to see if they can get in. Security teams can also spot attacks taking place across the network, such as command and control systems being used to transmit data in a way they shouldn’t. With the right XDR solution, detection also extends to the public cloud and productivity systems such as Office 365, enabling security analysts to spot attacks in the delivery stage, such as phishing attempts, ransomware delivered by email, or in the exfiltration stage.
In short, a unified XDR platform with a shared detection layer provides security analysts much broader coverage and more opportunities to identify and stop threats at any point in the kill chain.
 Cross-event correlation
Cross-event correlation
With a unified XDR platform built on a shared layer of detection, security teams can cross-correlate data and events from various sensors and sources throughout the organization to identify related activity and build a more complete picture of the incident. For example, they can identify related activity based on time, IP address source, behavior, or other activities. This enables the security analyst to provide much more comprehensive analysis.
Without this shared detection layer and cross-event correlation, security teams may be able to identify the root cause of an attack for post-incident analysis, but they don’t have the capability to shut down an attack in progress through a comprehensive view of what is happening. The shared layer and cross-event correlation in an XDR platform provides the complete picture of what is happening and enables a more targeted approach to response. Security analysts can see the first incident that took place in the kill chain, go back and follow that path to stop the attack before it spreads further.
Improved incident response
An XDR solution must also provide security teams with built-in response capabilities. Because XDR provides coverage throughout more of the organization, security analysts could respond wherever the attack has been identified – whether on endpoints, in the network, in the cloud, or in productivity applications. With a shared response layer, analysts can target their response and know exactly what process to kill or which machines to disconnect for stopping the incident.
An XDR solution should provide both automated responses, such as blocking malicious network connections, as well as recommended one-click, manual response capabilities such as machine isolation or a user credential reset. More points of coverage and the ability to capture more context around threats also mean faster response time.
An integrated analyst experience
User experience is an important aspect of an effective XDR solution, and when done right, can be a significant benefit for security analysts. Broader coverage, increased detection and more information are counterproductive if it just means increasing the workload for the security team or creates needless noise.
Bitdefender GravityZone XDR provides security analysts an easy-to-understand overview of the entire incident – including machines, systems and sensors impacted - a timeline of the incident and more, in a human readable summary. Security teams can then forward the summary to stakeholders to provide an overview of the situation. At the same time, security teams also have the option to dig deeper into the details and see every user, activity, event, system, or file that has been touched as part of the incident. This level of detail is useful not only for incident analysis, but also for post-incident triage and root cause analysis.
Conclusion
With the alphabet soup of acronyms in cybersecurity today, it’s no surprise that people are wondering if XDR is simply the next buzzword, or a repackaging of EDR and MDR. When designed properly and purpose-built, the answer is “No.”
A unified, native XDR platform like GravityZone, with a shared layer for detection and response, a wide range of coverage, cross-event correlation across and an integrated user experience delivers far greater protection against sophisticated threats than either EDR or MDR alone. Security professionals should keep these aspects in mind when evaluating solutions to find the right XDR platform for their organization.
-2.jpg)
Learn more about Bitdefender GravityZone XDR being named a Strong Performer in The Forrester New Wave™ report for XDR providers.
tags
Author
Bitdefender is a cybersecurity leader delivering best-in-class threat prevention, detection, and response solutions worldwide. Guardian over millions of consumer, enterprise, and government environments, Bitdefender is one of the industry’s most trusted experts for eliminating threats, protecting privacy, digital identity and data, and enabling cyber resilience. With deep investments in research and development, Bitdefender Labs discovers hundreds of new threats each minute and validates billions of threat queries daily. The company has pioneered breakthrough innovations in antimalware, IoT security, behavioral analytics, and artificial intelligence and its technology is licensed by more than 180 of the world’s most recognized technology brands. Founded in 2001, Bitdefender has customers in 170+ countries with offices around the world.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











