Your Business Should Be More Afraid of Phishing than Malware

The headlines love to talk about sophisticated hacking gangs, exploiting zero-day vulnerabilities to break their way into businesses and steal corporate data.
It seems not a day goes past without a security firm warning about a new strain of ransomware, or how criminals are planting cryptomining code on poorly-protected IoT devices and insecure data centres.
And although these are real problems and shouldn’t be ignored, I would argue that there is another more down-to-earth threat that is more commonly encountered and has the potential to cause massive harm to your organisation.
If you were to make a list of the most common causes of security breaches, it is phishing attacks that would surely dominate.
A recent study of 100 UK-based CISOs confirms that phishing is a major concern, with nearly half of respondents blaming the phenomenon for the biggest security incidents they had suffered in the last 12 months.
The figures speak for themselves:
- In fact, even when malware was combined with unpatched systems (coming to a total of 41% of reports) it still failed to be as big of a problem as phishing.
A phishing attack is considerably easier for a criminal to orchestrate than the creation of a brand new piece of malware, and can be reused time and time again with often little or no need for change between victims.
For instance, if you were an online criminal and your intention was to break into the cloud service used by a corporation in order to steal their sensitive documents, you could use the same phishing template posing as the cloud service time and time again.
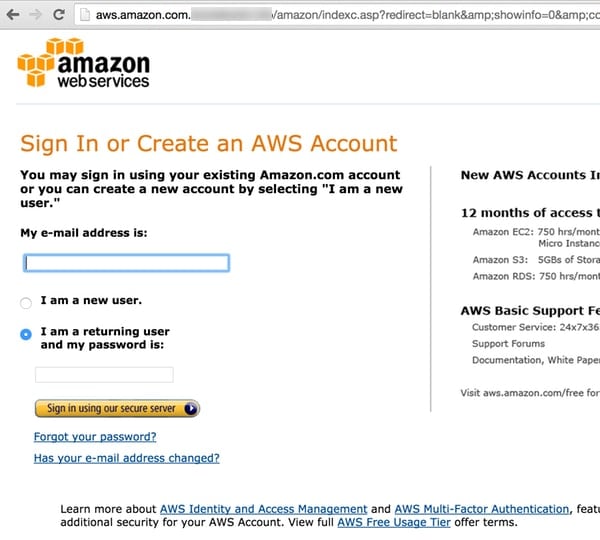
Similarly, if your intention was to – say – break into an organisation’s email system and you knew that they used Office 365, you could simply construct an email that tricks the victim into clicking on a link that they believed would log them into their Office 365 account, but really was designed to steal their password.
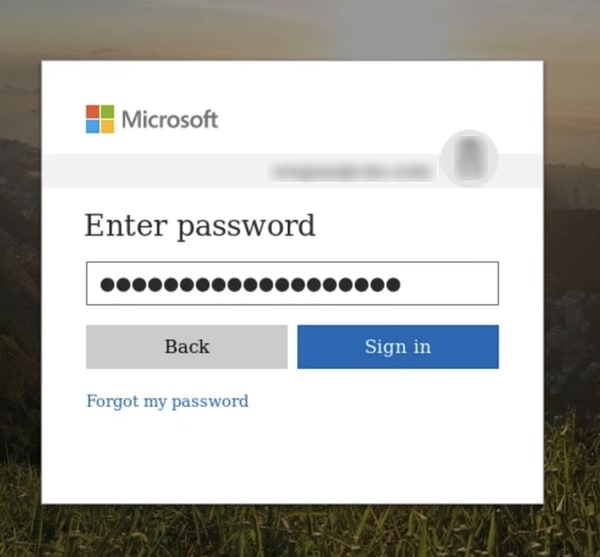
Most users will find it very hard to tell the difference between a fake login page and a real one.
And if your organisation is being specifically targeted by hackers, they may have gone to additional effort to make the webpage which aims to steal your login credentials even more sophisticated.
The browser’s URL bar is perhaps where the most obvious clues of trickery can be observed, but how many users can we really expect to carefully inspect the sometimes lengthy and complex URL?
It’s only human to click without thinking, to fail to spot where the URL was really pointing, to enter a password on auto-pilot without realising what you’ve just done.
I don’t believe that raising awareness amongst users of the tricks used by phishing pages, and to look for clues in the URL bar, is a waste of time – but we must recognise that if a person’s role is not security-focused, it’s unfair and unrealistic to assume that they will always have their guard up and be alert to potential threats.
A stronger defence, therefore, is to prevent as many suspicious emails as possible from entering your organisation in the first place, visibly warn users on-screen to take additional caution when an email originates from outside the business or if it contains keywords associated with phishing emails, enable multi-factor authentication wherever possible, and deploy a enterprise password management solution.
These last two points I believe are particularly important, as they put technology to work in helping reduce the chances of what is essentially a human problem.
More and more services now offer business users the option of enable multi-factor authentication or two-step verification. The huge security benefit of turning on such features is that even if online criminals do manage to steal the username and password of an account, they will not be able to access it unless they also have the one-time-password (OTP) used for an additional layer of authentication.
Systems like this are not necessarily completely fool-proof, and a sophisticated and determined attack may be prepared to go to the additional efforts required to try to still crack into accounts – but there is no doubt that it is considerably more difficult for a data breach to occur if such additional levels of authentication are in place.
Don’t take my word for it, it was revealed a couple of months ago that not one of Google’s 85,000 employees had had their accounts compromised by phishing in the last year. The reason? All staff gad been required to use physical security keys to authenticate their identity, rather than relying on passwords.
Google is setting a good example for other businesses here, but there is little evidence that enough other computer users are following in its footsteps.
Earlier this year, despite the alarming rise business email compromise and phishing attacks against organisations, Google reported that less than 10% of its customers have enabled two-step verification to harden their accounts from compromise.
Password managers also bring a big benefit in the fight against phishing. That’s because, aside from their well-understood talent for storing strong passwords securely, password managers can also offer to enter a username and password when they recognise a login page.
In other words, if they *don’t* recognise a login page – perhaps because the potential victim’s browser has ended up on a bogus webpage with a lookalike but non-identical URL – the password manager will not offer to enter their credentials.
Phishing may not be the sexiest threat out there, but do not underestimate its seriousness – and the impact it could have on your organisation if not treated with respect.
tags
Author

Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










