78% of Malware Activity in 2018 Driven by IoT Botnets, NOKIA Finds

IoT botnets scanning for unpatched vulnerabilities in connected devices accounted for 78 percent of the malware carrier network activity detected in 2018, according to NOKIA’s analysis of “network traffic for malware command-and-control communication, exploit attempts, hacking activity, scanning activity and Distributed Denial of Service (DDoS) attacks.”
“IoT devices are usually unprotected by normal security measures such as firewalls and anti-virus that are commonly available to traditional computing devices,” reads the report. “They are often left to fend for themselves in a hostile network environment. A vulnerable IoT device that is visible from the internet will be exploited in a matter of minutes and added to one of these many botnets.”
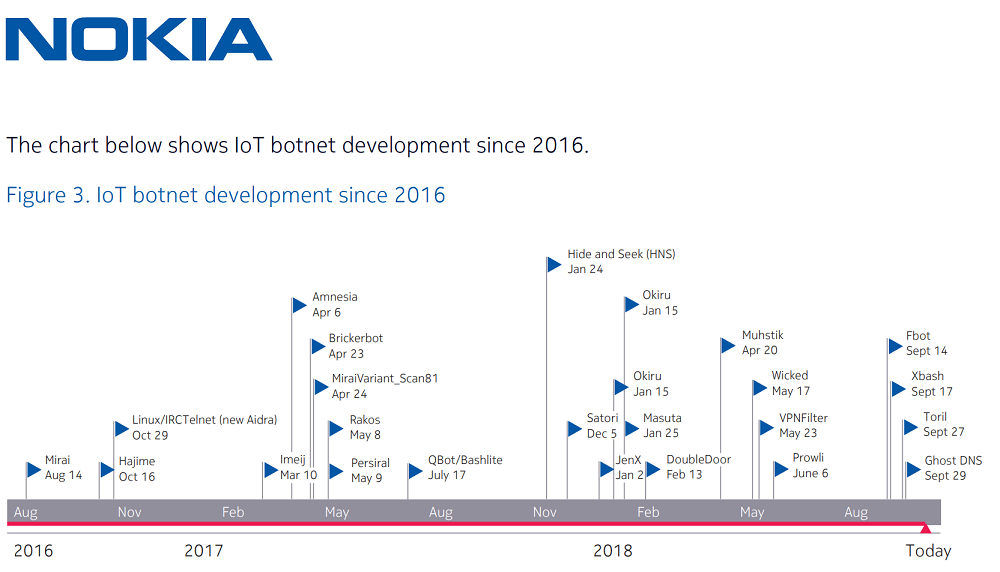
The most noteworthy malicious activity came from IoT botnets leveraging Mirai’s source code (35%). Once it was made available online in October 2016, Mirai malware rapidly evolved into more advanced, self-propagating strains, like Hajime and Satori, with some keeping only a small chunk of the original code. Although they share some architecture similarities, the new variants developed independently could be far more damaging than the original Mirai detected in 2016.
While Mirai mostly launched large-scale DDoS attacks by exploiting vulnerabilities in Linux consumer devices to bypass security, the most recent botnets can do more harm than just DDoS attacks. Many Mirai variations can also perform bitcoin mining or data theft, or completely destroy the IoT device by deleting the file storage system. Hajime is a worm that has turned out far more advanced than Mirai, communicated through a peer-to-peer network and focused more on corrupting as many devices as possible rather than launching DDoS attacks. The Satori botnet targeted some 500,000 routers worldwide and BrickerBot malware destroyed around 10 million connected devices, most often by rewriting their firmware.
Another rising threat not only for IoT devices, but also for mobile devices and web scripts, is cryptocurrency-mining malware. Cybercriminals often turn to crypto-jacking, exploiting users’ hardware, power and network infrastructure to covertly mine cryptocurrency, while some resort to crypto-stealing malware that hijacks wallets. Some crypto-mining malware that’s growing in popularity is specifically designed for devices with low computing power such as IoT devices.
“Malware based crypto-coin mining has expanded from targeting high-end servers with specialized processors to targeting IoT devices, smartphones and even browsers. Crypto-coin mining will continue its upward trend in years to come,” added the Nokia Threat Intelligence Lab research team.
Regular software patching and firmware updates, some knowledge about common tactics such as social engineering and third-party application vulnerabilities, and strong passwords could help reduce unauthorized access in user networks.
tags
Author
After having addressed topics such as NFC, startups, and tech innovation, she has now shifted focus to internet security, with a keen interest in smart homes and IoT threats.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








