Abode IoT Security Camera Vulnerabilities Would Let Attackers Insert Images, Bitdefender Finds

Bitdefender's security researchers have identified several vulnerabilities in the Abode IOTA Smart Camera that would permit attackers to inject their own media into the timeline, obtain the devices' geographical location, and more.
It's difficult to argue against the usefulness of security cameras, but customers have to be aware they also introduce a bullseye into their smart home. The IoT ecosystem is chock full of vulnerable devices, and criminals have slowly shifted their interests towards this ever-growing industry. More and more people buy IoT devices but don't always protect them, keep them up to date or even bother to check if the manufacturer still provides support.
Smart security cameras are all the more dangerous because they offer unique insight into people's lives when compromised. They're also prime targets for attackers looking for vulnerable IoT devices.
Hardcoding credentials is a no-no
The Abode IOTA Smart Camera uses the XMPP protocol with authentication to communicate with the cloud, which in itself is unusual. XMPP is rarely used for this, and the reason the manufacturer chose this protocol is unclear.
"To configure them from a blank state, the devices connect to the setup.goabode.com XMPP service to receive the configuration parameters," say the Bitdefender researchers. "Those parameters include the XMPP credentials to use after configuration."
"The XMPP credentials are the MAC address of the device (that forms the username) and a random password. However, because the device does not know this password before it's configured, to connect to the setup server it uses a hardcoded one."
Furthermore, while the XMPP connection uses TLS (encryption), the device doesn't check the validity of the certificates, which only means that man-in-the-middle attacks are possible, allowing attackers to inject arbitrary commands and take control of the device. The firmware upgrades share the same vulnerability.
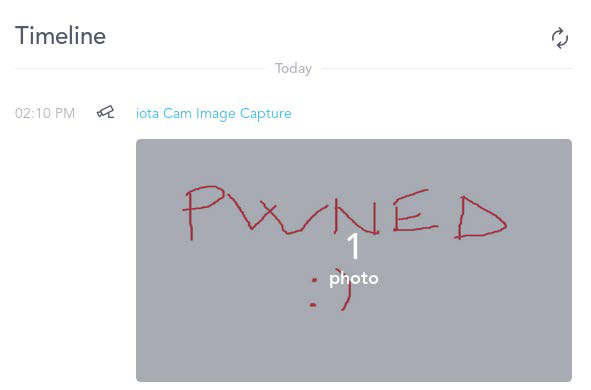
Making matters worse, while the image upload process uses HTTPS, the file is uploaded without authentication.
"The reporting ID is then used by the API to identify the account the media belongs to. If an attacker knows the reporting ID, together with the MAC address associated with it, they can upload any media to this API, and it will appear in the timeline of the device," the researchers add. Obtaining the ID is also a trivial matter.
Finally, it turns out that the device sends other information besides the ID, including the device's geographical coordinates.
Bitdefender initially contacted the vendor on May 19, 2020, but the manufacturer pushed the update for the affected devices to customers on Dec. 7, 2021.
You can check out the "Vulnerabilities Identified in the Abode IOTA Smart Camera: Fake Image Injection into Timeline" whitepaper for a full breakdown of the device and its security issues:
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks