Bug in Android Development SDK Triggers MasterKey Detection
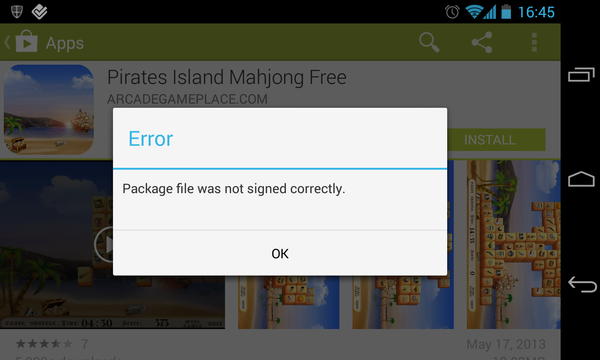
A couple of days ago we announced an update to the Bitdefender Mobile Security and Bitdefender Antivirus Free to mitigate the MasterKey vulnerability.
Since then, we started receiving reports about applications that manifest the MasterKey exploit behavior – overwriting identically-named files inside the archive as they were validated as digitally-signed.
A close look into a couple of applications hosted on Google Play and flagged as potentially harmful revealed a common trait: they all had the air. prefix, a marker for applications written in Adobe Air.
We looked into our collection of Android applications and, based on our telemetry, we discovered that nearly 1.25 percent of the applications written in Adobe Air manifest the MasterKey behavior and are blocked on patched Android distributions.
How the exploit works?
The MasterKey exploit works by including two duplicate files inside the same Android Package File (APK). When the Android device starts the application installation process, the operating system unpacks the APK file and extracts the files inside. However, since there are two identically-named files with the same path, the latter would overwrite the former, thus triggering the suspicious behavior. The introduction of a duplicate file is not voluntary (as it would be in the case of a malicious attack), but rather the side effect of a bug in the development tookit used by Android application developers – Adobe Air 3.7.0.153. The issue has been known and published on the Adobe bugtracker since Aprilie this year.
Who is impacted?
Although the icon substitution does not adversely impact device security, these applications will be denied the right to install on customers’ devices if they are running a patched Android version (Cyanogen Mod or the upcoming Android 4.3, among others).
I’m a developer, how do I fix this?
If you’re building Android applications using this specific version of Air, you should update to a newer version and rebuild your applications. If, for any reason, you are unable to update the development platform, you should simply remove any of the duplicate files by opening the APK file with any utility that can modify ZIP files and navigating to the \res\drawable-xhdpi\ folder and delete one of the icon.png files inside.
tags
Author
Right now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









