Cybersecurity Grand Prix: Circuit of the Americas Track Guide

In our micro series, the Cybersecurity Grand Prix, we explore the thrill of Formula 1 racing while partnering with Scuderia Ferrari HP, providing knowledge and tools to keep data safe in the race against cyber threats. In this episode, we explore the COTA track and why enterprise cybersecurity strategy needs a comprehensive approach.
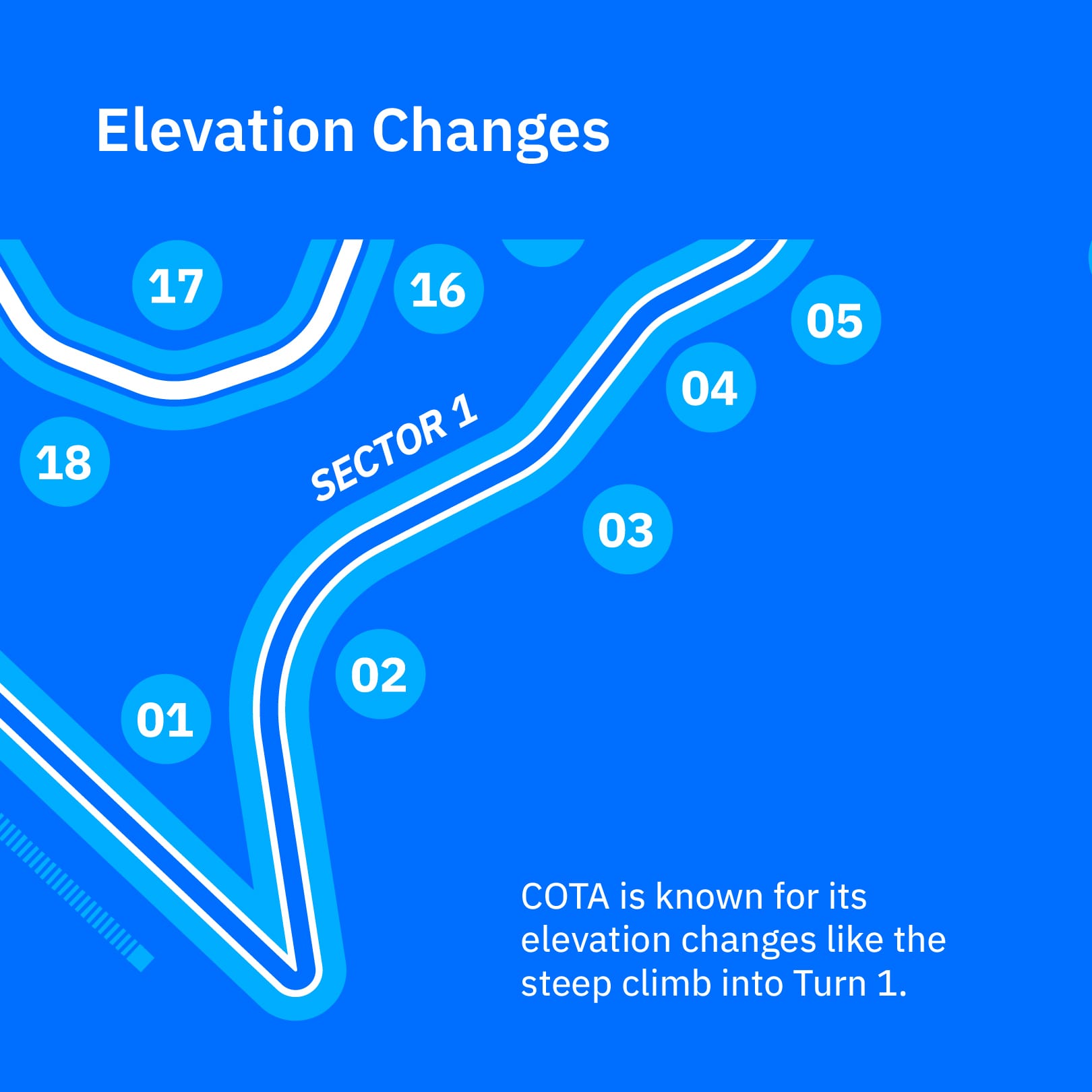
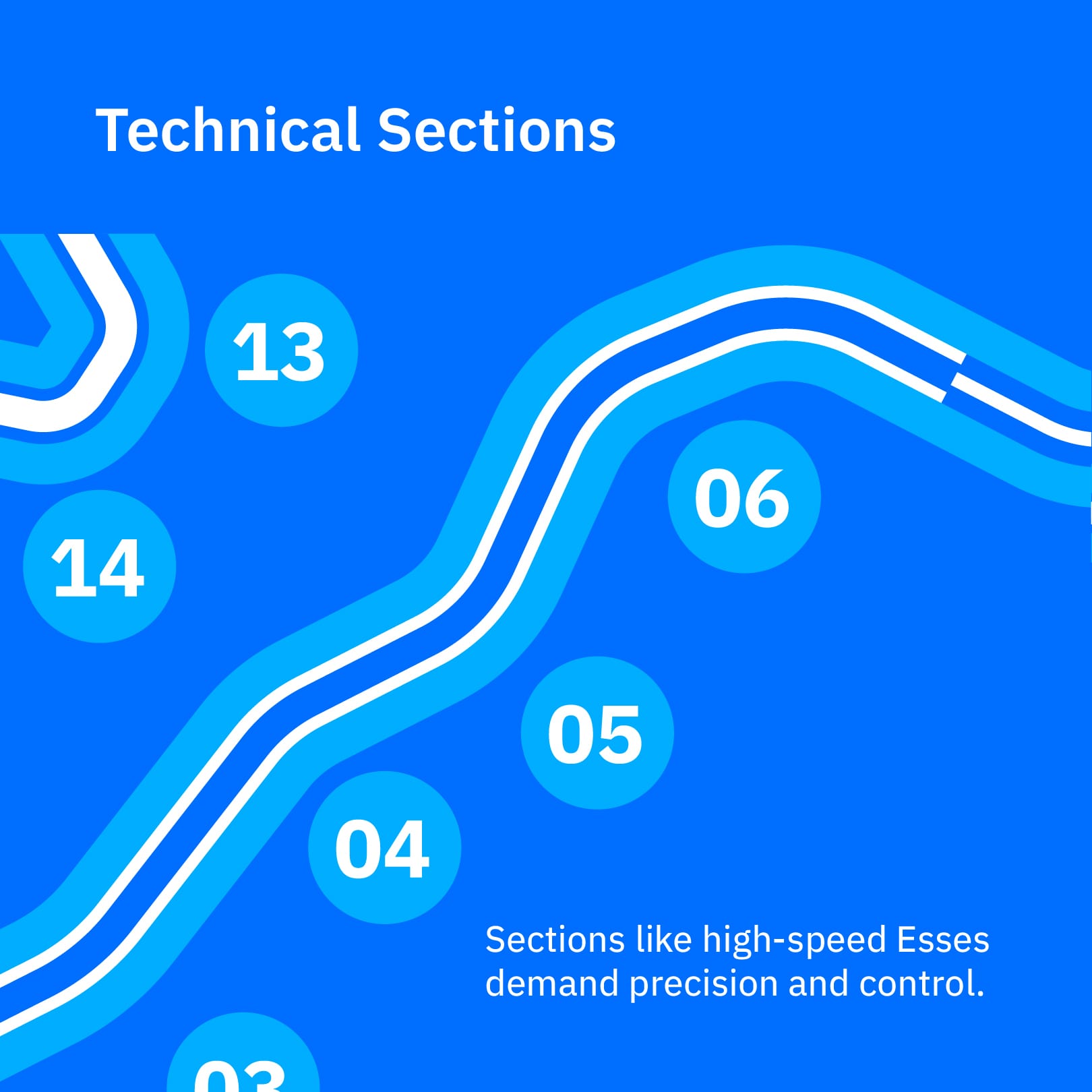
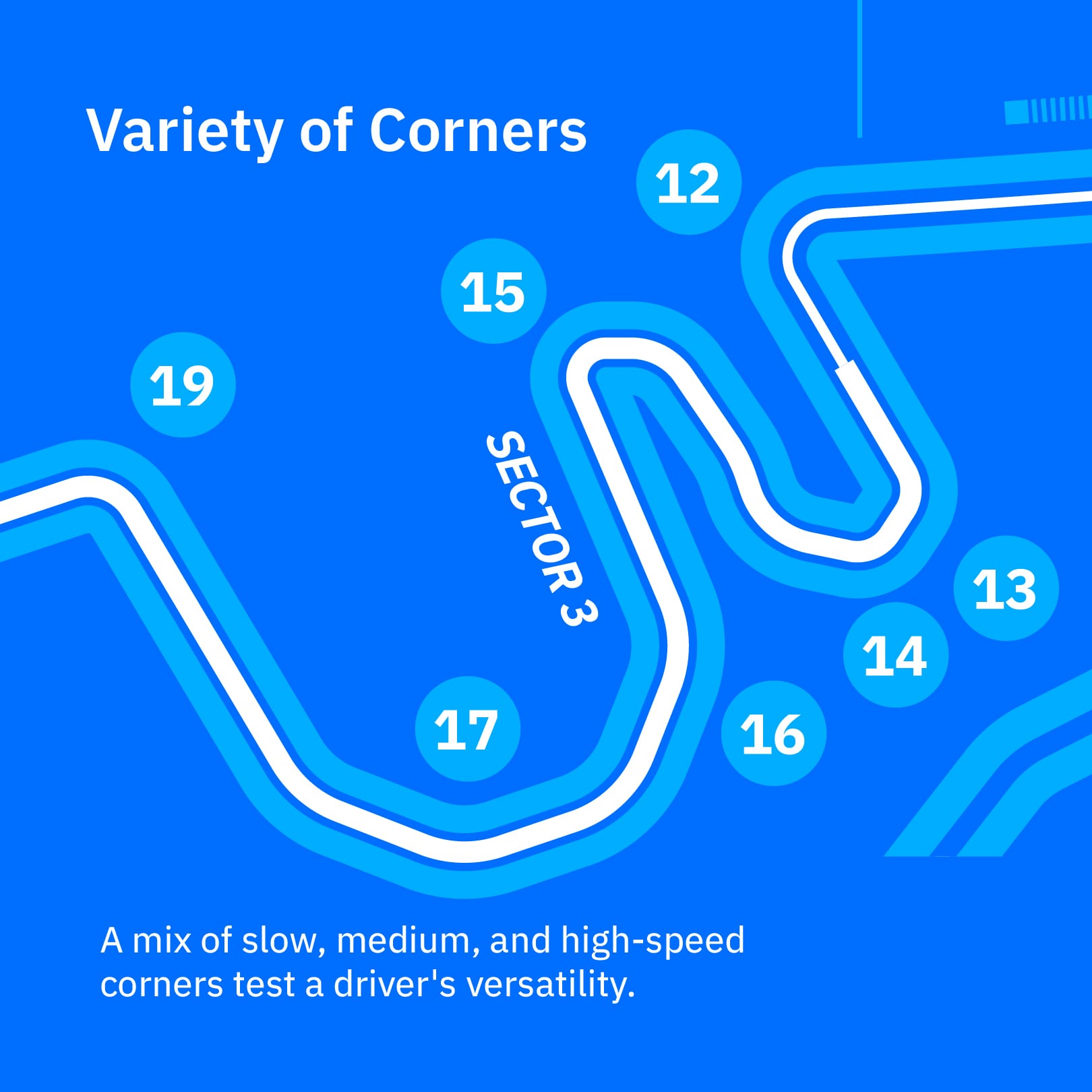
To succeed at The Circuit of the Americas (COTA), an F1 car must be fast and adaptable, handling the steep climb into Turn 1 as easily as navigating the high-speed Esses.
This versatility is not just about raw power but also precision, stability, and control, making COTA a true test of a car's all-around capabilities.
Just as a race car needs to be an all-round performer to meet the varied demands of the COTA track, an enterprise cybersecurity setup must be just as adaptable to cybersecurity threats that can come in many forms.
Bitdefender Track Guide to COTA
The Circuit of the Americas (COTA) was opened in 2012 and is known for its unique combination of corners that mimic famous sections of other tracks, such as Silverstone and Suzuka.
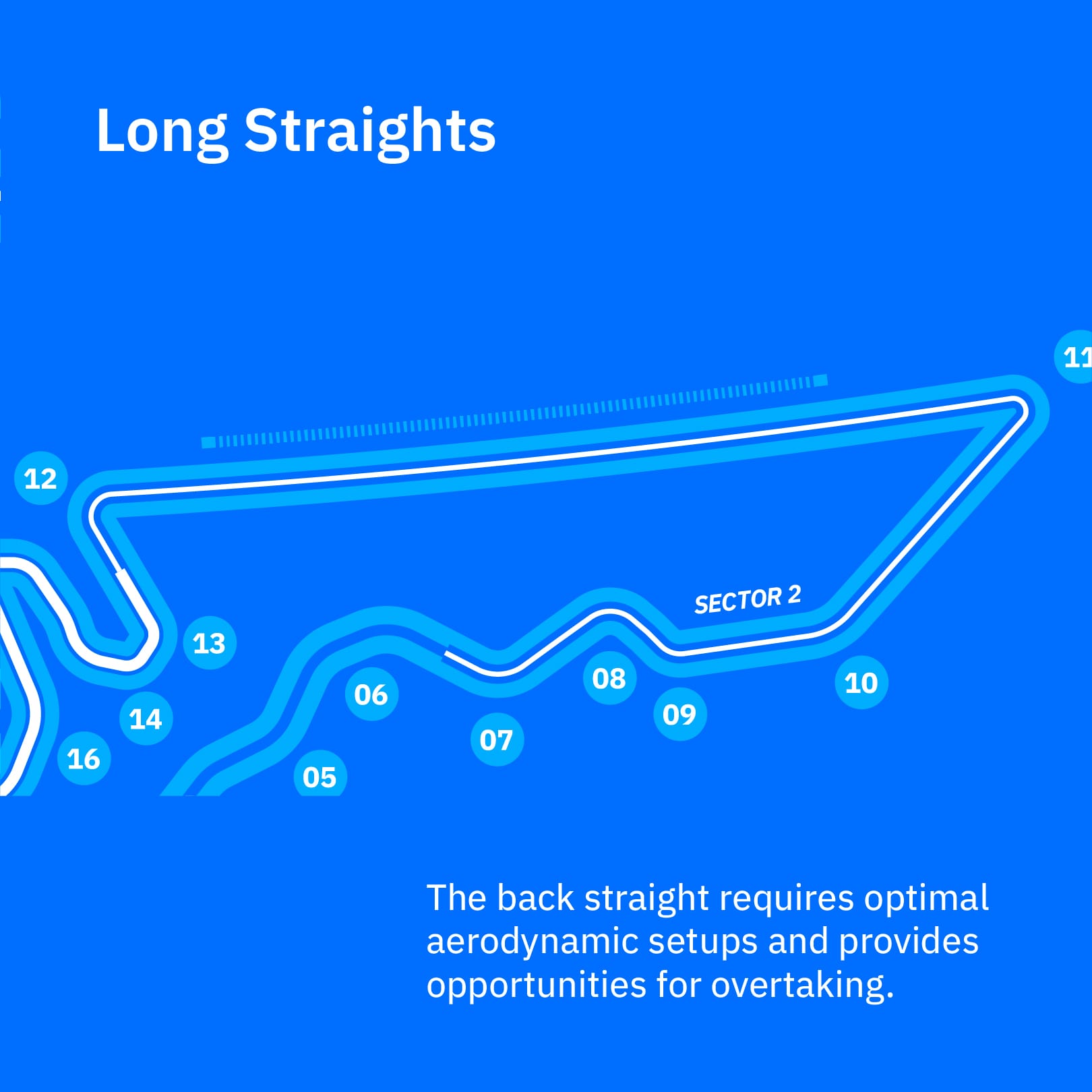
The core challenge of COTA for a race car setup is achieving a balance that handles diverse elements like elevation changes, technical sections, and a mix of corner speeds effectively.

A Versatile Enterprise Cybersecurity Setup
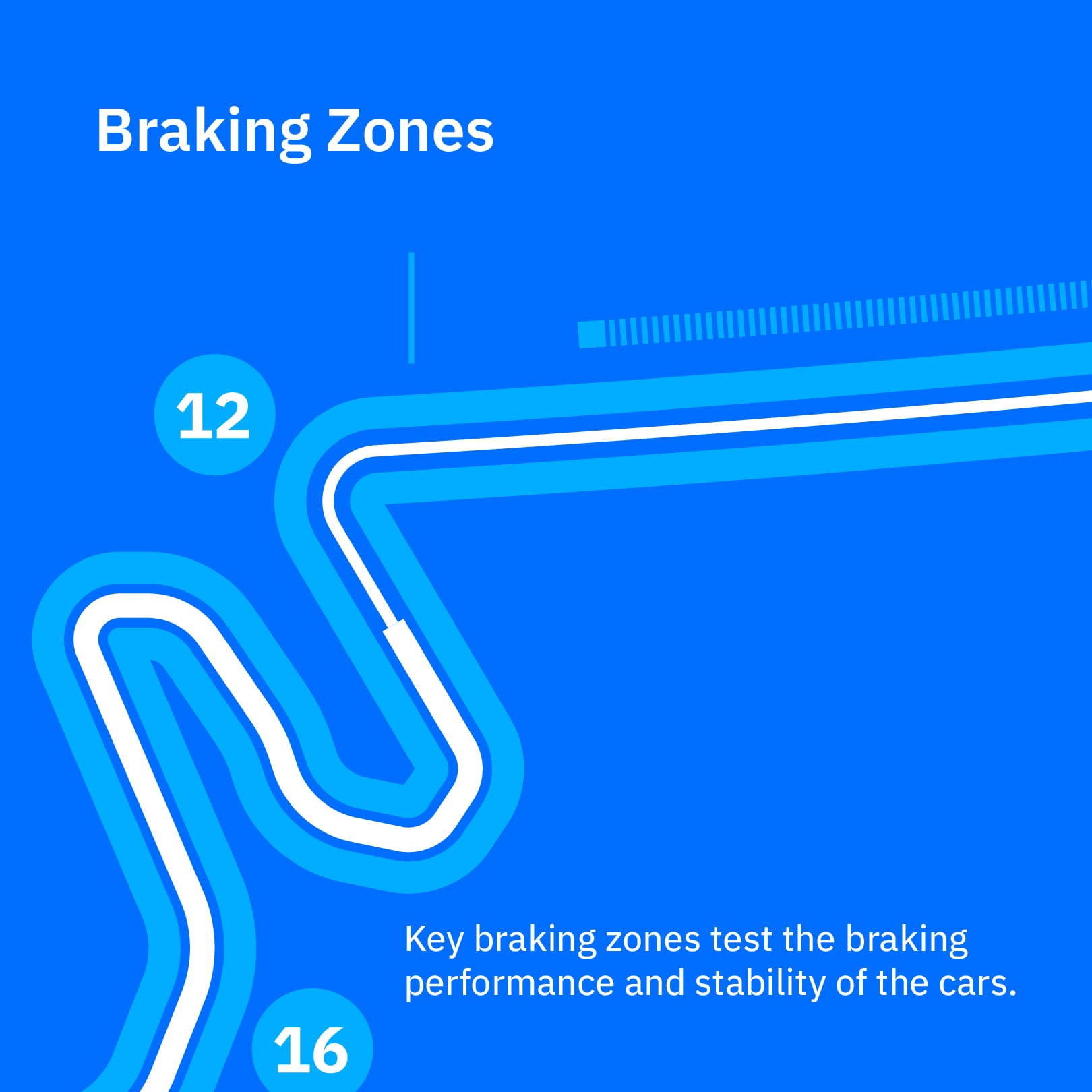
COTA is a track that tests a car from all angles—from the long straits, which test aerodynamics, to heavy breaking, which tests breaking performance, tire management, and the driver’s skill to avoid locking up.
A robust enterprise cybersecurity strategy must be similarly all-encompassing, incorporating various defenses such as firewalls, anti-virus software, and behavioral analysis tools to deal with threats from all angles.
Let’s examine some of the parallels between this versatility and race performance at COTA and enterprise cybersecurity.
- Complex Attack Vectors
Complex attack vectors in cybersecurity refer to the multifaceted methods that attackers use to breach systems.
These vectors involve a combination of phishing, malware, and social engineering techniques, making them difficult to defend against with one-dimensional security measures.
An enterprise cybersecurity’s firewalls, anti-virus software, and behavioral analysis tools work together to protect against a wide range of attacks, much like a race car must have a versatile performance set-up to meet the unique challenges at COTA.
- Adaptive Threat Detection
Adaptive threat detection in cybersecurity involves using advanced technologies, such as machine learning and artificial intelligence.
These systems continuously learn from new data, allowing them to detect anomalies and new attack patterns.
Just as the Scuderia Ferrari HP can adjust strategies based on incoming race data, machine learning algorithms can help businesses analyze user behavior, detecting unusual login patterns or data transfer volumes that deviate from the norm.
These advanced analytics can provide early warnings and help prompt responses to threats.
- Incident Response
Effective incident response and recovery protocols are vital in any enterprise cybersecurity strategy.
An example is initiating a "containment, eradication, and recovery" process in a ransomware attack, which involves isolating affected systems, removing malicious elements, and restoring from backups.
Just as the Scuderia Ferrari HP team at COTA must be able to promptly respond to any unforeseen event, such as safety cars or unexpected incidents, maintaining performance and safety in enterprise cybersecurity means being able to respond rapidly and strategically.
- Intrusion Detection Systems
Intrusion Detection Systems (IDS) are crucial in cybersecurity for monitoring network traffic and identifying suspicious activities that may indicate a cyberattack.
They act as overseers, much like the race control who constantly monitor the track and cars for irregularities or incidents.
Just as race control can signal a caution or safety car when detecting an issue, IDS alerts security teams to potential threats, enabling quick intervention to protect the enterprise network.
When it comes to taking on the track or implementing a robust enterprise cybersecurity strategy, versatility, and all-around performance are key. Just as a car setup must be able to handle diverse track challenges, a comprehensive cybersecurity strategy must be agile and responsive to evolving threats, ensuring optimal protection for the enterprise.
tags
Author

The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








