Daixin Ransomware Gang Abandons Hack of AirAsia due to Airline’s ‘Chaotic Network Standards’

The threat actors behind the Daixin ransomware operation have reportedly abandoned attempts to extort AirAsia due to the chaotic configuration of the low-cost airline’s internal network. The hackers say the airline’s incompetence actually spared them additional attacks.
AirAsia, headquartered near Kuala Lumpur, is the largest airline in Malaysia by fleet size and destinations, operating scheduled domestic and international flights to over 165 destinations across 25 countries.
Data on all staff and 5 million passengers in hackers’ hands
As reported by Databreaches.net, the airline recently fell victim to a ransomware attack by the Daixin Team, with the hackers stealing information of AirAsia’s entire staff and personal data of 5 million passengers.
In an exchange with the blog, a Daixin spokesperson said the victim company “asked in great detail how we would delete their data in case of payment.” The airline then reportedly abandoned communications, refusing to negotiate with the hackers, presumably because of Daixin’s high ransom demands.
Daixin later leaked samples of the stolen data on the dark web, including names, dates of birth, medical record numbers, patient account numbers, Social Security Numbers (SSNs), and other personal and medical information. The data belonging to AirAsia’s employees reportedly also includes the secret questions and answers for password resets.
The leak, as shown in a screenshot published by The Hacker News (embedded below), instructs potential buyers to use the data to conduct fraud and phishing attacks, take out loans in the victims’ names, obtain a driver’s license with a different photo, and even give false information to police during an arrest.
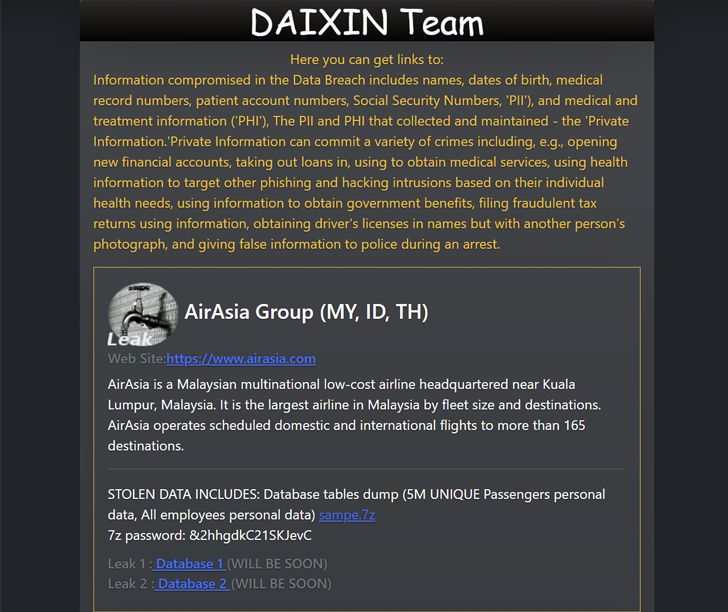
Credit: thehackernews.com
Lax security standards, chaotic network
The Daixin spokesperson clarified that the crew abandoned further attacks on AirAsia’s network due to the airline’s incredibly poor security standards and the chaotic organization of its IT infrastructure.
“The chaotic organization of the network, the absence of any standards, caused the irritation of the group and a complete unwillingness to repeat the attack,” the spokesperson for Daixin Team said. “The group refused to pick through the garbage for a long time. As our pentester said, ‘Let the newcomers sort this trash, they have a lot of time.’”
Asked if AirAsia’s poor organization spared the airline from more attacks, the spokesperson responded:
“Yes, it helped them. The internal network was configured without any rules and as a result worked very poorly. It seemed that every new system administrator ‘built his shed next to the old building.’ At the same time, the network protection was very, very weak.”
Besides leaking the passenger and employee data, the group plans to disclose vulnerabilities in the network, including ‘backdoors’ – presumably planted by the Daixin gang itself.
Daixin Team on the FBI’s radar
The Daixin hackers were the subject of a recent security advisory by the FBI, the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS). They described the group as a cybercrime organization actively targeting US entities, with a notable focus on the healthcare and public health (HPH) sector via ransomware and data extortion operations.
The October hack of CommonSpirit Health, which reportedly led to medication errors and delayed life-saving cancer surgery, is said to have been conducted by the Daixin crew. CommonSpirit is believed to have ceded to the attackers’ monetary demands in a bid to protect patients’ lives, privacy and security.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








