Gamers Should Still Take Precautions Despite No Evidence Of User Compromise in Electronic Arts Data Breach

This summer, malicious actors breached the internal network of Electronic Arts (EA), stealing over 750 GB of data, including the source code of popular video game FIFA 21.
What happened
The exfiltrated data was dumped on a dark web marketplace in July after a failed attempt to sell it for a staggering $28 million. The stolen data also included other game development tools that had no market value on underground forums peddling stolen user data, including personal data, account login info and credit card information.
The gaming giant did not give in to the extortion attempt, and the data was made public.
“We’ve been made aware of an extortion threat from the alleged hackers, and a portion of some files were released to the public,” EA said in a statement. “We have analyzed the files released by the alleged hackers, and at this time, we continue to believe that it does not contain data that poses any concern to player privacy, and we have no reason to believe that there is any material risk to our games, our business or our players.”
The hackers who stole EA’s data were even willing to explain how they stole the company’s info. In an interview with Motherboard, the group said they tricked an EA employee on a Slack chatroom. After gaining access to EA’s internal network, the hackers were able to access FIFA’s 21 matchmaking servers, software development kits and API Keys, and download the source code for the game.
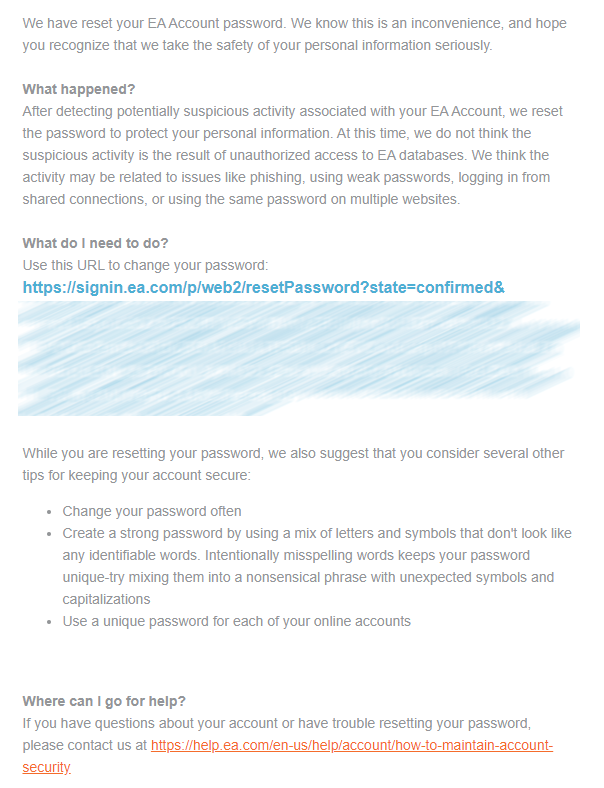
EA’s sending automatic account password resets to users
Starting September 15, EA sent users automatic password reset emails. The notification states that potentially suspicious activity was detected, and that this step was necessary to help protect personal information. EA says the suspicious activity is most likely due to phishing or poor cyber hygiene.
“After detecting potentially suspicious activity associated with your EA Account, we reset the password to protect your personal information,” the email reads. “At this time, we do not think the suspicious activity is the result of unauthorized access to EA databases. We think the activity may be related to issues like phishing, using weak passwords, logging in from shared connections, or using the same password on multiple websites.”
How can users secure their online data and accounts
Even if you did not receive a notification email telling you to reset your account password, you should. Stick to this habit every time a company announces a data breach, regardless of whether customer data was involved, and enable an extra layer of security using the two-factor authentication feature provided by the company.
Don’t offer too much personal information when signing up on platforms. Use the privacy settings to control how your profile appears to members of the gaming community. Be wary of unsolicited emails that ask for sensitive information or urge you to download attachments.
Opt for a local security solution to block and detect malicious software, and alert you to any phishing attempts. Last but not least, log out of your account when using a shared or public device and stick to official sources for downloading updates, apps and game-related purchases.
Were you a victim of a data breach? Time to find out with Bitdefender’s Digital Identity Protection tool. The dedicated online privacy service helps you take control and minimize your digital footprint by continuously monitoring for data breaches. Our service also lets you detect social media impersonators that can ruin your reputation. The tool proactively scans the web for accounts set up using your data (email address and phone number) and notify you each time a new profile is created so that you can quickly inspect it and stop impersonation attempts before they cause irreparable harm.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







