Hackers Can Attack Social Logins to Impersonate Users, IBM Study Shows
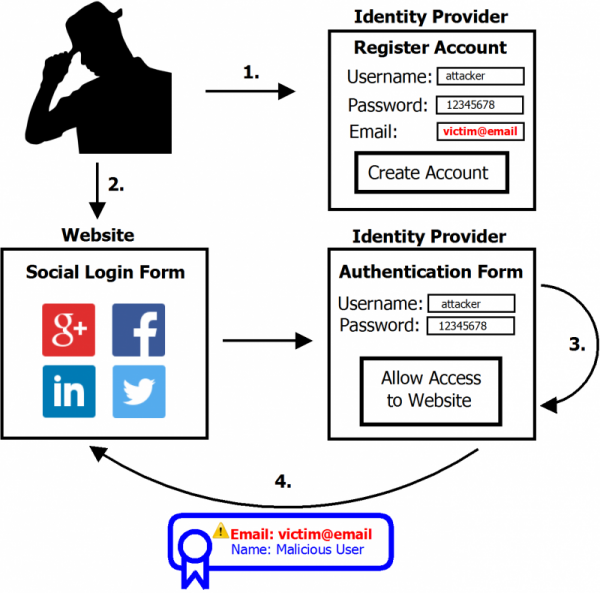
Cyber-criminals can exploit social logins, such as the “Sign In With Facebook/LinkedIn/etc” buttons, to hijack accounts and impersonate users through a technique dubbed SpoofedMe, according to IBM research. To run the attack, hackers register a spoofed account at a vulnerable identity provider using the victim`s email address. Cyber-criminals can then post misleading information and even malware on victims` behalf.
The IBM study revealed that hackers can easily abuse the mechanism that allows users to quickly gain access to various web accounts with the social login. After IBM`s warning earlier this year, LinkedIn and Amazon moved to update their systems.
LinkedIn`s security team fixed the issue by denying social login requests that include the email field, in case the email isn`t verified. Vulnerable third-party websites that also rely on LinkedIn include Nasdaq.com, Slashdot.org, Crowdfunder.com and Spiceworks.com. Several shopping websites use Amazon as a login.
“If you have a piece of malware code and you take over someone`s trusted account and say Ëœhere`s this code,` because you`re leveraging trust already established in the community, others on the website are more likely to use it,” IBM Executive Security Advisor Diana Kelley said. “That would be a big Ëœgotcha`.”

To be successful, the SpoofedMe attack requires a combination of flaws, according to IBM X-Force security team:
- a vulnerability with a social login identity provider such as LinkedIn, Amazon and MYDIGIPASS.
- a known design issue in the websites that rely on the identity providers for verification.
- an email address that hasn`t already been used in an account at the vulnerable identity provider.
Before announcing the hacking technique, IBM reviewed the popular identity providers, privately disclosed details to the vulnerable ones, and waited for them to apply fixes. The SpoofedMe technique can still be exploited in the wild, as there are identity providers and websites vulnerable to both the social login, and the design problem.
tags
Author
Bianca Stanescu, the fiercest warrior princess in the Bitdefender news palace, is a down-to-earth journalist, who's always on to a cybertrendy story.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








