Hackers Hijack Indian PM Narendra Modi Twitter Account
- Twitter account used to spread cryptocurrency scam
- Hackers deny that they have hacked Paytm Mall, India’s leading online shopping app
A Twitter account posting tweets on behalf of the Indian Prime Minister’s personal website and mobile app has been hijacked by hackers, who abused it in an attempt to scam 2.5 million followers.
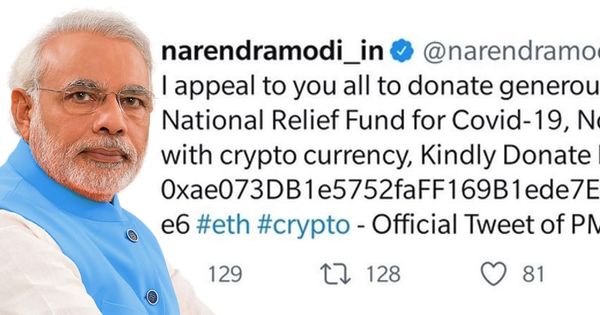
The @narendramodi_in account, linked to Indian Prime Minister Narendra Modi”s website, was commandeered by hackers who posted bogus messages asking followers to make cryptocurrency donations to a supposed national Covid-19 relief fund.

One unauthorised tweet read:
I appeal to you all to donate generously to the PM National Relief Fund for Covid-19, Now India begin with crypto currency, Kindly Donate Bitcoin to [REDACTED BITCOIN ADDRESS] #eth #crypto – Official Tweet of PM Modi
Of course, you’re fooling yourself if you believe that sending cryptocurrency to the wallet address quoted in the now-deleted tweet will ever end up helping people affected by the pandemic.
In a separate tweet posted by the hackers, they claim that they are a hacking group known as “John Wick” and deny claims that they were responsible for an alleged hack at Paytm Mall, India’s leading online shopping app.

For its part, Paytm Mall denies it has suffered any security breach.
In July, a number of high profile Twitter accounts were hijacked by malicious hackers to spew out a cryptocurrency scam – after seemingly gaining access to Twitter’s internal systems.
A number of young people alleged to have been involved in that attack have since been apprehended and – in at least one case – have made virtual court appearances that have themselves been disrupted by online intruders.
It is not believed that the hack of the Indian PM’s Twitter account is related to the spate of account hijacks that took place in July.
Which means that we can’t be certain as to how the @narendramodi_in was compromised. However, it would seem sensible for all Twitter users to ensure that they are using a unique, hard-to-crack password for their accounts, and have enabled two-factor authentication.
In addition, although it may not be the reason why the account was compromised on this occasion, it is sensible to regularly review what third-party apps have access to your Twitter account, and revoke permissions for any that you no longer require.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








