Homoglyph domains used in BEC scams shut down by Microsoft

17 domains used in Business Email Compromise (BEC) scams have been seized by Microsoft's Digital Crimes Unit (DCU), following an investigation by the software giant into attacks that could have stolen millions of dollars from innocent firms.
The "homoglyph" domains impersonated domains used by legitimate businesses, and were used in attempts to defraud Microsoft Office 365 customers.
Homoglyph domains exploit the fact that many different characters look identical or very similar.
For instance, the capital letter "O" and the number "0" (eg. MICROSOFT.COM vs MICR0S0FT.COM) or an uppercase ninth letter of the alphabet “I” and a lowercase 12th letter “l” (eg. MICROSOFT.COM vs. MlCROSOFT.COM).
In the past, homoglyph attacks have also taken advantage of domains which contain Unicode characters (rather than conventional ASCII), allowing users to mistake - for instance - the Cyrillic "а" (U+0430) the ASCII character "a" (U+0061). They may look the same but they are different characters!
In a blog post, Microsoft said that it continued to see homoglyph domains used in BEC scams, nation state activity, and the distribution of malware and ransomware.
As Microsoft explains in legal documents, attacks often combined with phishing attacks to steal credentials and break into the accounts of customers:
Credentials are most typically stolen through an attacker sending a “phishing” email to the victim that contains a link to a malicious website used to socially engineer victims into divulging their account login credentials. Attackers accomplish this by using email domains chosen to impersonate trusted domains or appear otherwise legitimate, and malicious websites set up to impersonate legitimate Microsoft login pages (e.g., using trademark/copyright infringing images to spoof a legitimate Microsoft landing page). The attackers’ goal is to deceive targeted victims such that they visit the malicious site and enter their Office 365 account credentials into a counterfeit login page, and those credentials are then captured for subsequent use by an attacker. These types of malicious attacks persist despite the fact that Microsoft encourages all its customers to use certain precautions to protect account credentials such as enabling two factor authentication.
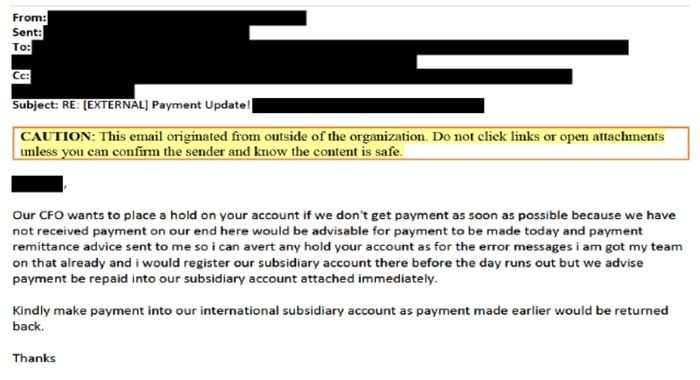
Microsoft says that its latest investigation began after a customer complained about a BEC attack that used a homoglyph domain in an attempt to trick the victim into transferring funds into a bank account controlled by cybercriminals.
In the example given by Microsoft, fraudsters came across a legitimate email at the compromised account of an Office 365 customer which referred to payment issues and requested advice on how to process payments.
The criminals seized the opportunity to send a bogus email - using a homoglyph domain nearly identical to the legitimate one, and the same sender name - which directed the victim to urgently transfer funds into a bank account under the control of the attackers.
According to Microsoft, the scammers are believed to operate out of West Africa, and are primarily targeting small businesses in North America.
Microsoft successfully won a judgement at the Eastern District of Virginia for the third-party domain registrars to disable the malicious domains it had uncovered, foiling the future plans of scammers to so easily impersonate employees of legitimate businesses and commit fraud.
Homoglyph attacks are not just useful for BEC scammers, but can also be used in all manner of other frauds - including phishing attacks.
"We continue to see this technique used in business email compromise (BEC), nation-state activity, malware, and ransomware distribution, often combined with credential phishing and account compromise to deceive victims and infiltrate customer networks," said Microsoft.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








