IoT search engine exposes passwords of over 30,000 vulnerable DVRs

We’ve often warned on the Bitdefender BOX blog of the risks of not keeping your IoT devices updated with the latest security patches. After all, if you leave a vulnerable device online there’s always the danger that a hacker might access it over the internet and exploit the flaw to hijack it for their own malicious purposes.
But now a researcher has discovered that it’s easier than ever before to hack at least one brand of internet-enabled DVR, as an IoT search engine has cached their passwords within search results.
Security researcher Ankit Anubhav raised the alarm last week in a series of tweets about the number of vulnerable Dahua devices accessible online.
A new low has been achieved in the ease of hacking IoT devices. One does not even need to connect to the Dahua devices to get the credentials (thread) (1/n) #iot #infosec pic.twitter.com/K2tgvoXOCS
— Ankit Anubhav (@ankit_anubhav) July 12, 2018
Vulnerabilities in the Chinese manufacturer’s DVRs were first brought to light five years ago, but although patches have been available for years it is clear that tens of thousands of devices have still not had their firmware updated.
The flaw in the Dahua DVRs allows remote attackers to bypass authentication checks, and obtain sensitive data such as usernames and passwords, alter passwords, clear log files and perform other actions.
And it is through this flaw that the vulnerable Dahua DVRs, which are often connected to CCTV camera systems, have spilt their login credentials in plaintext to publicly accessible IoT search engines, such as ZoomEye.
It’s worth noting that the ZoomEye IoT search engine wasn’t trying to gather the passwords of vulnerable Dahua DVRs – it’s just cached what was returned to it when the DVRs’ ports were scanned.
Anubhav reports that many of the vulnerable devices have weak passwords such as “admin123”. Almost 15,800 Dahua devices were using the password “admin”, and more than 600 were using possibly the worst password of all – “password”. Meanwhile, over 13,900 of the devices, for instance, have the (diabolically poor) password of “123456”.
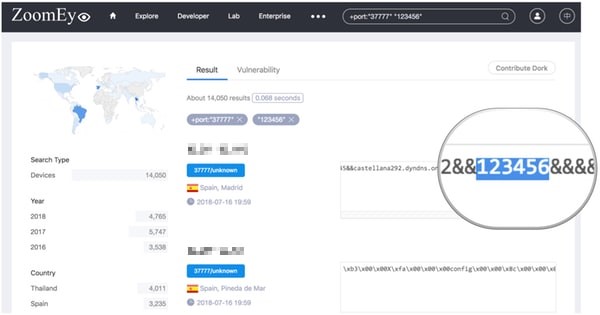
In all, over 30,000 vulnerable DVRs have been found attached to the internet.
If users have not chosen a strong password, there’s little chance that they will have been diligent about ensuring that their Dahua DVR is also running the latest firmware.
But, regardless of whether your Dahua DVR is “protected” by a weak password or not, the point is clear – the strength or uniqueness of your password is irrelevant if a vulnerability has allowed an IoT search engine to cache your device’s password.
Anubhav has contacted ZoomEye requesting that the passwords be removed from its cache of results, but so far no action appears to have been taken.
If you live in one of the many households, or work in one of the growing number of companies, that is embracing IoT then it is clear that relying solely upon manufacturers to automatically update their devices with the latest firmware is playing with fire.
Many IoT devices are built cheaply, with little consideration for security. If you want to ensure that your home or office is not the next to have its internet-enabled devices hijacked you’re going to have to find a better way to secure yourself.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








