LinkedIn Data Leak: Hundreds of Thousands of Spam Emails Flood Users' Inboxes
Users of the employment-oriented online service are being targeted with an assortment of phishing emails and scams in an attempt to hijack their LinkedIn accounts or promote fake LinkedIn email leads.
According to Bitdefender Antispam Lab telemetry, ramifications of the LinkedIn data leak incident seem to have already manifested through new spam campaigns targeting inboxes of hundreds of thousands of users.
Although the recent uptick in LinkedIn-themed spam can’t be directly associated with the leaked information of 500 million platform users, the overwhelming number of deceptive and fraudulent emails suggests otherwise.
Spammers and scammers and fraud, oh my!
The Bitdefender Antispam Lab has spotted over 500 million scam emails selling premium LinkedIn leads from the US, UAE, Middle East and Canada.
Despite the sheer number of legitimate companies that provide such email marketing services, fraudsters often pose as lead-generation specialists to promote bogus sales leads to digital marketers. They advertise the delivery of “verified and 100% accurate LinkedIn leads” but rarely stick to their word, swindling their targets out of thousands of dollars. If they do deliver, recipients are likely to receive fake, recycled or stolen user information.
The scammers don’t ask for your personally identifiable information or include any malicious attachments.
At the end of each email, the unsubscribe button leads users to suspicious domains that may inform the scammers when recipients hit the unsubscribe button. It verifies if the email was viewed and confirms that the recipient’s email address is valid – so it can be used in future spam campaigns.
Samples of these unsolicited emails can be seen below:

Sample 1.

Sample 2.

Sample 3.
Hi, I’d like to join your LinkedIn Network
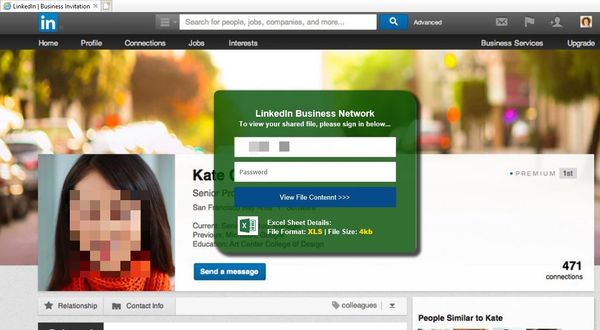
Some threat actors stick to classic phishing tactics to steal LinkedIn login credentials by sending out bogus connection requests to users. In one version of the scam, recipients receive a seemingly valid connection request from a Sales Manager named Kate.

However, upon close inspection of the email, you immediately see the red flags.
The perps did put some effort into creating the email by not using a standard email template. They deliberately generated an image mimicking a LinkedIn invite with which users cannot interact with. Maxim efficiency is ensured, as targets are forced to access the attachment for more information.
When recipients click on the Linkedin.html, a fake LinkedIn page opens.

The green window asks for the account password and conveniently has the recipient’s email addresses filled in.
Amanda would also want to join your LinkedIn network to pitch a business offer you can’t resist. She’s also a Sales Manager working for a US-based company.

Crooks phish for your credentials via LinkedIn business inquiries
Other cybercrooks send fake LinkedIn business inquiries to targets.

Recipients interested in what Molly has to say who click on the Accept Business button will open a separate window that asks for the user’s password.

Even if the above scam and phishing emails don’t ask you to act immediately due to a security alert or account termination, they may still fool unsuspecting LinkedIn users into giving their account passwords to cybercriminals.
The most recent LinkedIn-themed spam campaigns may differ from brick-and-mortar-style ruses, but their purpose remains the same. Before you realize it, your account password is in the hands of the bad guys, and they can now take over all of your online accounts that use the same email and password combination.
Check if your personal info has been stolen or made public on the internet with Bitdefender”s Digital Identity Protection tool.
Note: This article is based on technical information provided courtesy of Bitdefender Antispam Lab.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








