Phishing Campaign Targets CloudFlare Customers
Popular content distribution and DDoS specialist CloudFlare has issued a warning about a targeted phishing campaign making the rounds among its customers.
According to a support notification issued by CloudFlare, the rogue e-mail message comes with a spoofed e-mail address that belongs to CloudFlare. To make it seem more legitimate, the message includes the domain the victim is using in conjunction with the CloudFlare service.
The e-mail scares CloudFlare users into believing they have exceeded the server load for their plan. If they are curious enough to investigate the incident, they are advised to follow the phishing link in the message.
This is not your average slice of spam, but rather a highly-targeted attack on the company`s customers. If you`re wondering where these attackers get their info, don`t worry, it`s not from CloudFlare themselves, but rather from the Whois database.
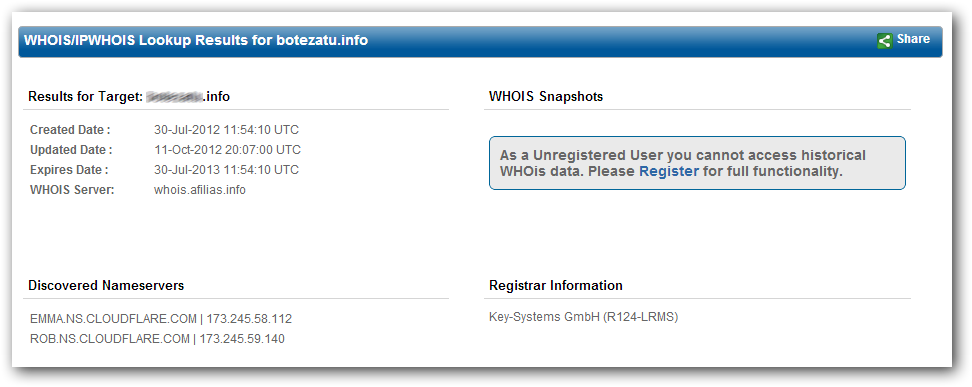
In order to enable CloudFlare on a domain, the customer needs to change the domain nameservers to the CloudFlare ones, a change that is publicly visible on the Whois lookup page for the respective domain. In other words, it`s safe to assume that, if a domain uses CloudFlare nameservers, the respective owner of the domain is a CloudFlare Customer.
Whois info publicly lists used domain nameservers
Once the attackers lay their hands on the CloudFlare login credentials, they can do quite a few bad things with your domain, including pointing it to another website, disrupt e-mail communication for that domain or better yet, access your credit card details in the billing information area of your account. (Update: according to this article, the credit card data is not shown in the input fields once it’s saved).
If you got the message and entered your personal information on the phishing page, you are advised to use the “forgot password” link on the CloudFlare page to reset your password.
[via Softpedia]
tags
Author
Right now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









