"Activate the new security system" is a phishing scam targeting Italians
Ingenious phishing scam targets Italy’s post office and bank operator, Poste Italiane, with e-mails designed to con users into willingly give away authentication data to their online money accounts.
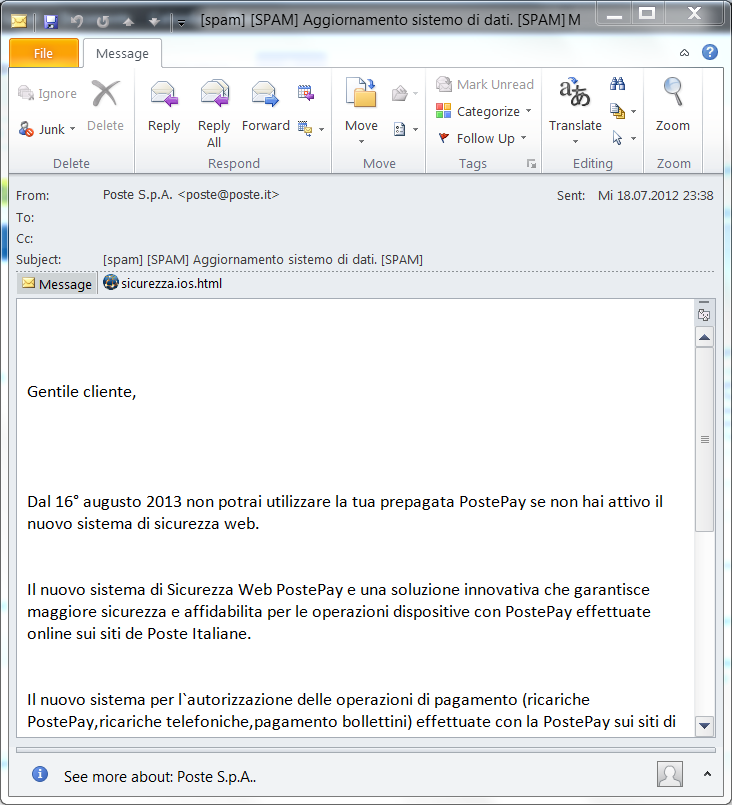
The fake e-mail officially informs customers they can no longer use the prepaid PostePay service if they don’t activate the new web security system of Poste Italiane by August 16th 2013.
Fig. 1 Bogus e-mail allegedly sent by Poste Italiane
To activate this new security system, customers need to confirm their identification data by accessing a link to a login page where the user must fill in personal information such as user name, password, card ID or security card number.
Fig. 2 Phishing form
Filling in the form gives the crooks pretty much everything they need to access any cash in the compromised accounts, impersonate the victims or use that data in fraud or future spam campaigns.
This scam is knitted around the launch of the Poste Italiane new security system, on February 1st, 2012, to make the con more credible and boost its chances of success.
This new web security system allows customers to operate secure payment transactions such as recharging PostePay, phone cards, or pay ing bills online using the Postepay website of the Poste Italiane with only two instruments: a PostePay card and a phone number where a One Time Password will be generated and sent for each payment.
With Poste Italiane, for instance, people may continue to fall for this kind of attack because this postal service and bank at the same time has as customers mostly elderly, people from rural areas or inexperienced teen-agers. They can’t or won’t properly receive the warning messages the service providers, media or security companies send, making them easy targets for crooks.
A few months back, Bitdefender reported another attack against Poste Italiane customers ” a con asking users to confirm their login data this time for maintenance reasons.
Fig. 3. Spring phishing campaign on Poste Italiane
What was particularly interesting then – and it is used again in this attack – is that the stolen information is neither sent via e-mail to an attacker nor saved in a database. Instead, it’s stored in a plain text file on the same compromised server that hosts the phishing form, making the attack way worse, as this information is not only available to attackers, but also to anyone who knows how to use a search engine to find valid CC info.
In July, another bogus message, impersonating CartaSi, targeted Italians using the service. The phishing e-mail informed customers that the account statement for the previous month may mistakenly include charges for stamp and delivery costs due to technical problems. The user was notified that the amount will be reimbursed in the next statement and that the user needs to check his account to make sure that all the private data is accurate.
Fig 4. Fake phishing e-mail allegedly sent by CartaSi
The user was guaranteed all data was stored in encrypted form and never sold to third parties not involved in managing the service. The e-mail provided the user with a link to a fake site to fill in personal information such as user name, password and access code. Crooks fish for identification data from CartaSi customers for fraud, impersonations, or further spam campaigns. Once users’ data is stolen and stored there is no exact telling of what will happen to that information.
The webpage may look a lot like the official CartaSi webpage but it is definitely not genuine. No financial institution asks customers via e-mail to fill-in, check, validate critical data by sending a form or providing a link.
So, every time you have any suspicions regarding your online card account data, immediately call Poste Italiane, CartaSi or any other institution to have all recent transactions blocked at once. They will direct you through the steps necessary to have your card re-issued.
As a rule, always avoid giving out credit card information, especially when you need to disclose your PIN or CVV info. Banks and other institutions working with money never ask clients to change IDs or passwords via e-mail. When in doubt, pick up your phone and call or pay them a visit to make sure. Also, install anti-virus software and keep it up to date.
tags
Author
A blend of product manager and journalist with a pinch of e-threat analysis, Loredana writes mostly about malware and spam. She believes that most errors happen between the keyboard and the chair.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks











