Scammers Impersonating DHL Delivery Service Seek to Harvest Customer Login Credentials and Credit Card Details

Bitdefender Antispam Lab has recently uncovered a trio of phishing campaigns spoofing the DHL delivery service in an attempt to collect login credentials and defraud international customers by stealing their credit card information.
Most emails use the DHL logo and graphic design, making it appear that the shipping company sent the correspondence.
The English version of the phishing email imitates a regular DHL message and urges the recipient to download an attachment to view and print a receipt for an incoming parcel.


The attacks originate from IP addresses in Portugal (95%) and Brazil (4.6%) and have spread across the US, Europe, and Asia. Specifically, 53% of the fraudulent emails reached users in the US, 15% in South Korea, 9% in the UK, 5% in Japan, 3% in India, 2% in Germany, and 1% in France, Switzerland and the Netherlands.
In this particular case, attackers are phishing for the victims' email passwords. The HTML attachment directs to a fake webpage the asks users to enter their email password. The login box is pre-filled with the target email, as seen below.
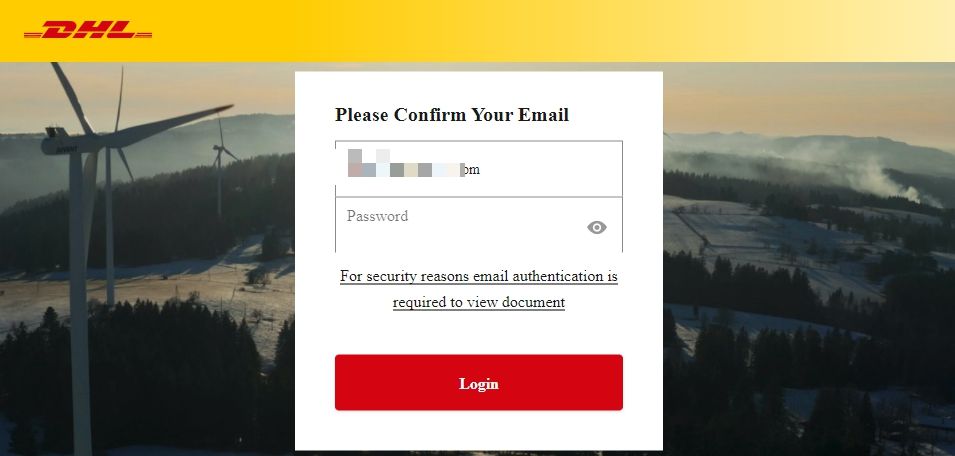
However, the German version alerts victims that their package could not be delivered due to an unpaid custom tax of 2.99 Euros. 95 percent of the emails originate from Japan and target users in Switzerland, United States, UK and Germany.
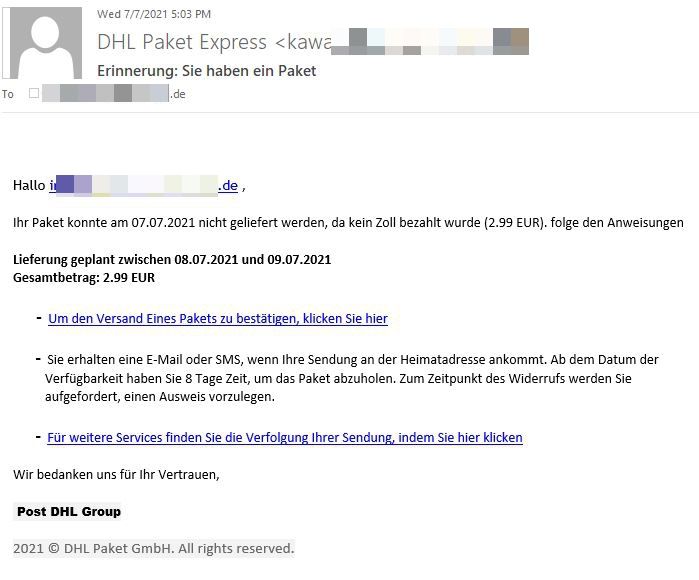
The email asks recipients to click on a link to confirm the shipment of the package. When accessed, a fake DHL tracking page requests customers to pay the shipping fee by entering their name, credit card number, expiry date and CVV. The currency of the payment changes depending on the IP of the victim.
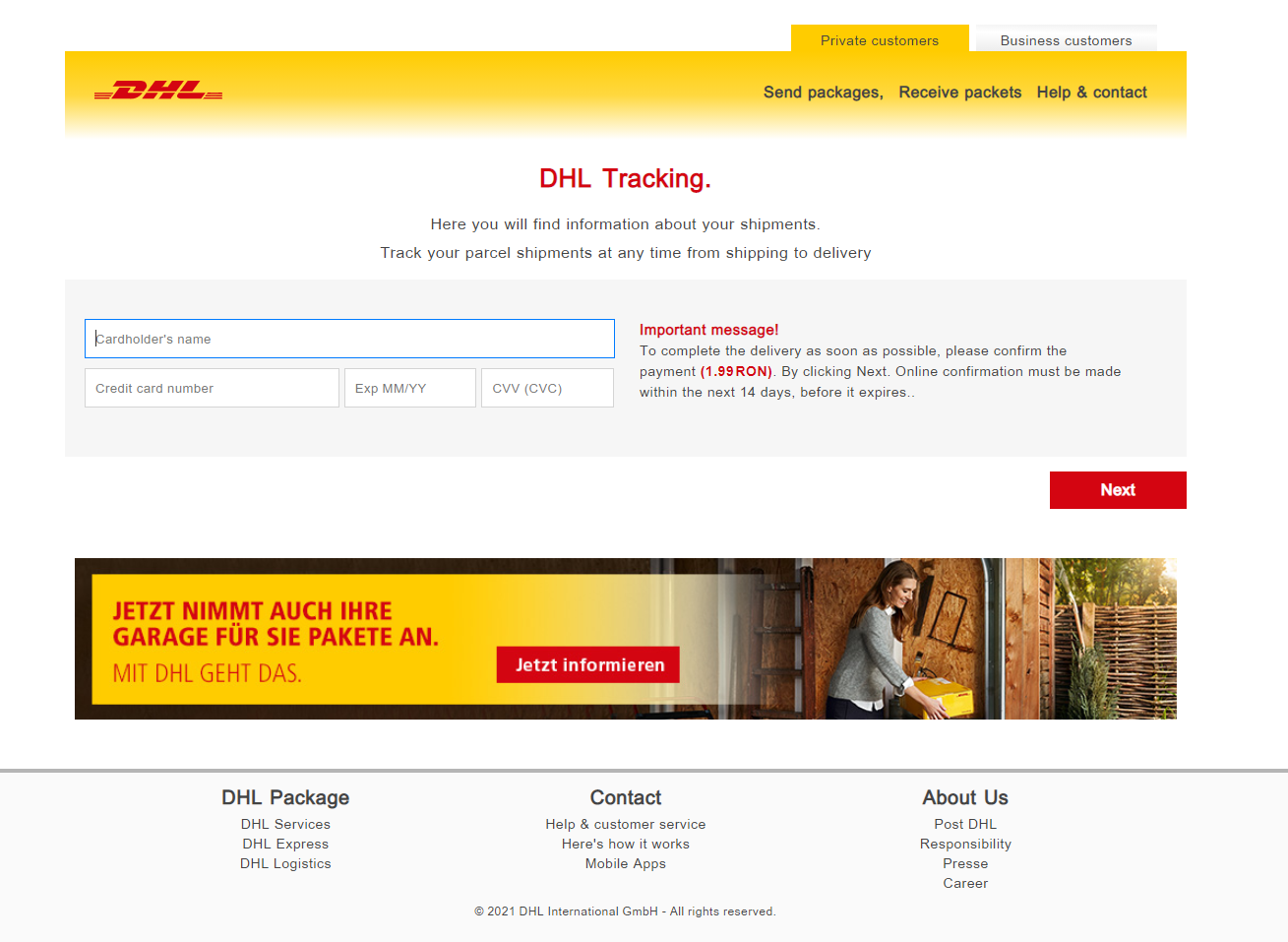
In this particular attempt, fraudsters rely more on social engineering tricks to tempt victims into clicking on links and providing sensitive info, such as their credit card data.
They provide additional information and directions for recipients. Users are notified that they will also receive a text message or email when the package arrives at their address, the time frame in which they may collect the package, and a link to track their shipment.
In Italy, the phishing campaign tries to trick users into believing that a DHL package could not be delivered due to incomplete details. The attackers used an IP address from Bangladesh to distribute fraudulent correspondence. The phishing page is no longer in use, but we can assume that the attackers' goal was to harvest additional personal information from targets.

Messages from delivery companies such as FedEx and DHL will easily capture recipients' attention. It's no surprise that scammers continue to impersonate these brands to spread fraudulent or malicious correspondence.
According to DHL's fraud awareness page, official correspondence from the company will always be sent from email addresses using @dhl.com, @dpdhl.com, @dhl.de, @dhl.it, or another country domain after @dhl.
Customers who receive any suspicious emails should report the scam email via phishing-dpdhl@dhl[.]com. After sending or forwarding the message, make sure to delete the email. Do not attempt to reply to the sender, access attachments or click on any links. If you provided passwords or personally identifiable information, make sure to immediately reset your login credentials to all online accounts using the same password and email combination, and notify your bank.
Note: This article is based on technical information provided courtesy of Bitdefender Antispam Lab
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








