Steam Users Alerted to Potential Malware in 'Sniper: Phantom's Resolution' Demo
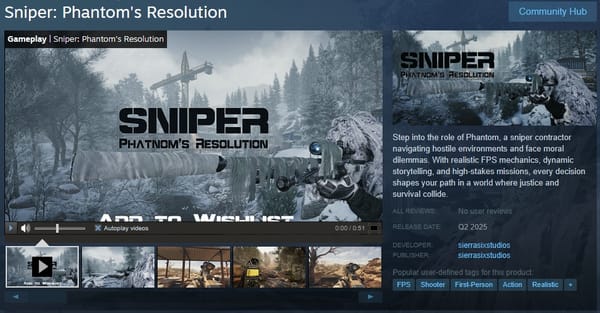
Valve's Steam has been abused again to spread malware. The game Sniper: Phantom's Resolution has raised alarms within the gaming community after users noticed the official Steam page linked to a demo likely containing malware.
In most cases, games on Steam that have demos available to download are hosted on the platform — however, the developers of Sniper: Phantom's Resolution linked to a page outside the Steam ecosystem.
Malware quickly found by the gaming community
The issue came to light when a Reddit user noticed the promotional materials for Sniper: Phantom's Resolution appeared to be sourced from other titles, casting doubt on the game's legitimacy.
This tactic is nothing new to the Steam platform, but it's enough to cast aspersions on any game.
The user also noticed that the Steam page did not host the demo directly but had a link to an external website. The gaming community got into gear and, following a short investigation, discovered that the main executable file from the demo was named "Windows Defender SmartScreen.exe."
If any user ran the demo, it would require administrator privileges and open a web browser. This is classic behavior for info stealer malware designed to steal saved user credentials stored in browsers.
Users also found that the demo was accessing GitHub-hosted resources, such as wincrypt, a wrapper built in Rust that uses the native windows api's CryptProtectData and CryptUnprotectData functions.
Essentially, this wrapper can be used to access encrypted data (saved passwords, authentication tokens) or encrypt malware payloads, making detection harder.
And all of this is just the beginning. The "game demo" also creates startup tasks and runs numerous command lines in an effort to remain undetected.
Valve's response and security Implications
Following user reports, Valve removed the game from the Steam Store. However, the game's listing remains visible on Steam's website, indicating that remnants of the game persist while the malicious link has been removed.
In response to similar incidents, Valve has implemented additional security measures, including requiring two-factor authentication for developers updating their games on Steam. This move aims to prevent unauthorized access to developer accounts and the potential distribution of malicious software through the platform.
GitHub also removed a project that hosted the malware payload, ran by the same developers listed on the Steam website.
Only a few weeks ago, Valve removed PirateFi, a free-to-play game, because it hosted malicious code.
Recommendations for users
Users are advised to exercise caution when downloading demos or additional content, primarily when directed to external websites outside the Steam ecosystem. It's crucial to ensure that downloads come from reputable and verified sources. Additionally, maintaining security solutions up to date and performing regular system scans can help mitigate the risks.
The discovery of potential malware within the purported "Sniper: Phantom's Resolution" game demo serves as a reminder of the vulnerabilities in digital distribution platforms.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








