Supply-chain CAPTCHA attack hits over 100 car dealerships

A security researcher has discovered that the websites of over 100 car dealerships have been compromised in a supply-chain attack that attempted to infect the PCs of internet visitors.
As researcher Randy McEoin explains in a blog post, cybercriminals infected the systems of LES Automotive, a company which provides a video services to help car dealerships market vehicles online.
As a result, webpages that were supposed to display a video of an enticing vehicle could instead redirect dealerships' online visitors to a third-party webpage which - in a technique known as a "ClickFix" attack - presented a CAPTCHA asking if they could prove that they were "not a robot."
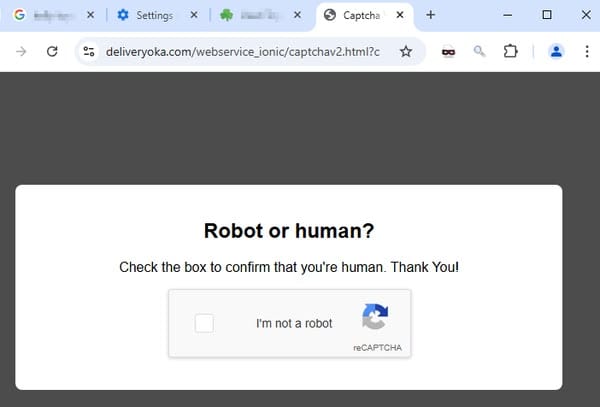
In itself, a CAPTCHA is not an unusual sight on the internet. But all is not as it seems, because the user is then presented with a very specific method for proving that they are human and not a bot.
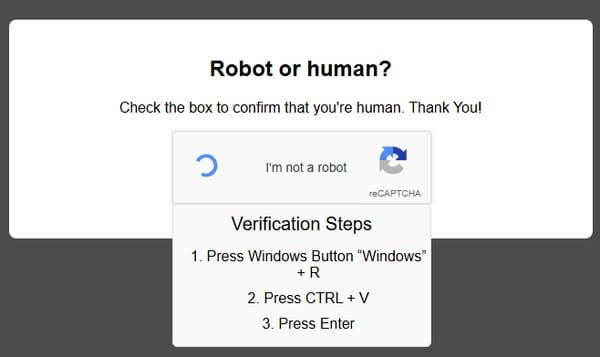
Verification Steps 1. Press Windows Button "Windows" + R 2. Press CTRL + V 3. Press Enter
This is very different from being asked to identify the traffic lights or a fire hydrant in a photograph!
The instructions by the bogus "verification" request initiate a Windows Run command, pasting whatever malicious code the webpage has put into the computer's clipboard.
And this is what is somewhat ingenious, because the malicious hackers have cleverly waltzed around the protection of traditional security tools. It's you, the user, manually entering a malicious command on your PC. It's not an external piece of dangerous software or script on a website that's doing it.
For some months it has become increasingly common for cybercriminals to use the disguise of a fake CAPTCHA verification to trick users into unknowingly running PowerShell commands that allow security to be breached.
In the particular case of the car dealerships, it appears that the aim of the attackers is to socially-engineer innocent users into an infection by the malware known as SectopRAT.
If a PC is unfortunate enough to become infected by SectopRAT, malicious hackers can steal sensitive data from the infected computer such as their cryptocurrency wallet credentials.
In October last year, the US Government advised users and organisations to be vigilant as it detailed the threat, and gave examples of websites that impersonated Google Chrome, Facebook, reCAPTCHA, and others using the ClickFix social engineering tactic.
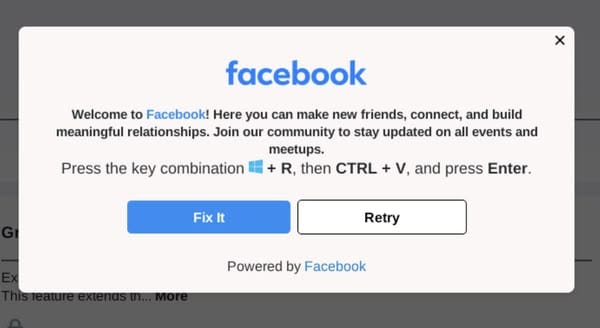
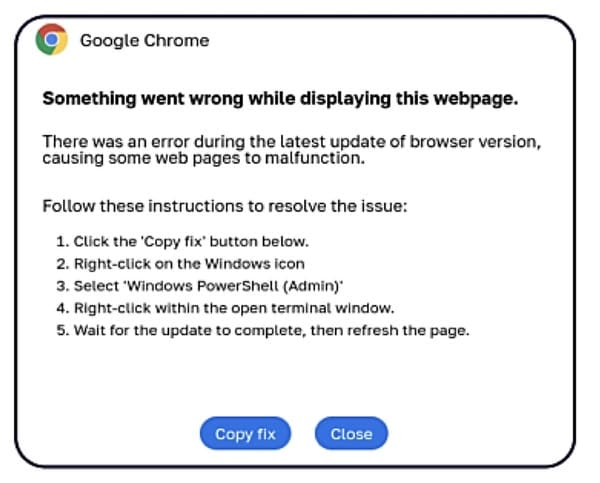
Every day thousands of people are falling for ClickFix scams, and helping their computers become infected as a result. One type of malware which has been distributed in this fashion is Lumma Stealer, a trojan horse that targets web browsers, cryptocurrency wallets, two-factor authentication extensions and instant messaging services such as Telegram to extract valuable sensitive data.
Don't make life easy for the hackers. Be extremely cautious if a CAPTCHA asks you to perform a peculiar action - such as an odd key sequence - to prove that you are human. You could be unwittingly infecting your computer with malware.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








