Wells Fargo Clients Targeted by Fareit Malware; Sensitive Info Exposed
Wells Fargo clients are again targeted by data-stealing malware through a well-crafted spam campaign. The Trojan known as Fareit comes packed with a password-stealing component that allows malware writers to gather sensitive details from users’ devices, including Facebook and email credentials.
According to Bitdefender data, the systems most infected with this family of Trojans are located in the US, home to Wells Fargo. In the last week, the same type of Trojan has been making rounds in France, Croatia, Italy, Australia, Belgium, Spain, Romania, Egypt, and the United Arab Emirates.
Fareit is a multiple-component malware family that consists of a password-stealing component that grabs sensitive information from the victim’s computer and sends it to a remote machine. The malware family also contains a DDoS component that may be controlled to flood other servers in collective attacks. Once installed, the malware also downloads and executes Zbot or Zeus, one of the most notorious and widespread Trojans so far.
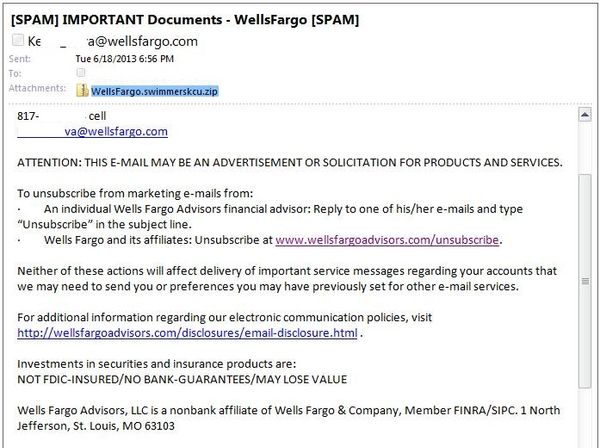
 With a general subject such as “Important Documents” the malicious emails pose as coming from Wells Fargo employees. To make the spam look legit, scammers included links to the authentic financial institution. When opening the attachment, which is also dubbed with the bank’s name, users end up installing a hidden EXE file packed in a PDF extension.
With a general subject such as “Important Documents” the malicious emails pose as coming from Wells Fargo employees. To make the spam look legit, scammers included links to the authentic financial institution. When opening the attachment, which is also dubbed with the bank’s name, users end up installing a hidden EXE file packed in a PDF extension.
When executed, the Fareit Trojan silently installs itself on vulnerable systems where it starts searching for sensitive details such as passwords and usernames. It also connects with the remote machine controlled by the attackers to make configuration updates and, on command, download additional malware. The Trojan also extracts passwords and usernames from browsers and mail clients, so be sure you disable the options that allow them to remember all your credentials.
Fareit also grabs account information such as server names, port numbers, login IDs and passwords from the FTP clients or cloud storage programs installed on the victim’s computer.
Bank clients are an easy target for cyber-criminals, who go as far as creating fake websites from scratch to trick individual users. Such fraudulent web pages look similar to the authentic ones, sometimes posing as their branches or local offices.
Bitdefender offers some tips to enhance protection against this type of malware attacks:
- Don’t open email attachments even if they look like they come from reputable institutions;
- Remember that banks will never ask for your personal information by email, nor send you ZIP files and tempt you to open them.
- Though they might sometimes put pressure on you, banks and financial institutions will not threaten clients with account closure or 24-hour deadlines for updating PINs and passwords. These are only a method scammers use to create a sense of urgency and make users click without thinking on malicious links.
- Install and update your software and antivirus solution. This will protect you from the latest cyber-attacks.
- Consider a solution such as Bitdefender Safepay, a browser that secures online banking and e-shopping, offering protection on Wi-Fi Hotspots.
This article is based on the technical information provided courtesy of Octavian Minea and Cristina Vatamanu, Bitdefender Malware Researchers.
All product and company names mentioned herein are for identification purposes only and are the property of, and may be trademarks of, their respective owners.
tags
Author
Bianca Stanescu, the fiercest warrior princess in the Bitdefender news palace, is a down-to-earth journalist, who's always on to a cybertrendy story.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









