A Deep Dive into Stream-Jacking Attacks on YouTube and Why They're So Popular

Stream-jacking attacks have gained significant traction on large streaming services in recent months, with cybercriminals targeting high-profile accounts (with a large follower count) to send their fraudulent ‘messages’ across to the masses.
Starting from the fact that various takeovers in the past resulted in channels morphing into impersonations of known public figures (e.g. Elon Musk, Changpeng Zhao) that promoted various scams (e.g. crypto doubling scam), we began a thorough analysis.
This writeup will focus on the takeovers and impersonations found on the YouTube platform.
Modus Operandi
Lately, there have been many instances of suspicious YouTube livestream pop-ups in the feeds of the end-users that promote the same content. Although distinct, these channels seem to have a lot in common:
A) The names of the channels try to portray them as Tesla, with variations that include: Tesla Official, Tesla US, Tesla News, Tesla (Inc)
- Lots of names are, in fact, homoglyphs in which the letter
lis replaced with capitali(I): TesIa, TesIa Factory, TesIa Motors, etc.
B) The handles of the channels are also variations of Tesla. Some of them include noise characters like _ and -
- @tesla—us_
- @tesla—corp.
- @ustesialive
- @tesla_us_live24
- @teslalive2023us-ceo
- @tesla—inc.
C) The titles are the same and are relatively limited in diversity:
- A New Era for Tesla’s Model 3 - Live Reveal with Elon Musk!
- A New Era for Tesla’s Model 3 - Live Reveal with Elon Musk! Twitter Rebrands to X!
- Live Stream of Tesla Model 3 2024 Unveiling with Elon Musk!
- CEO Elon Musk Presents: Live Reveal of Upgraded Tesla Model 3 2024!
- Twitter’s X Rebranding: Elon Musk’s Live Announcement & Logo Unveiling!
- Tesla Q2 Earnings Report Coverage & Analysis - Live Reveal with Elon Musk!
- SpaceX Launch Hughes JUPITER 3 Mission! Elon Musk gives update on Starship!
- Live Reveal with Elon Musk - A New Era for Tesla’s Model 3!
- Elon Musk: Would you buy an all-electric Tesla Flying Car in 2050?
- SpaceX Jupiter 3 Falcon Heavy Launch! Elon Musk gives update on Starship!
- Elon Musk Unveils Tesla’s New Model S Plaid 2024 Today!
- Tesla Unveils the All-New Model S Plaid 2024 Today! Live Coverage with Elon Musk!
- LIVE: Tesla’s unveils a masterpiece: The Tesla that will change the car industry forever - Tesla CEO
- Tesla US Live Stream
- The description and tags of the videos are largely the same
- The thumbnails of the livestreams and channels are usually the same
- The banners of the channels are usually the same
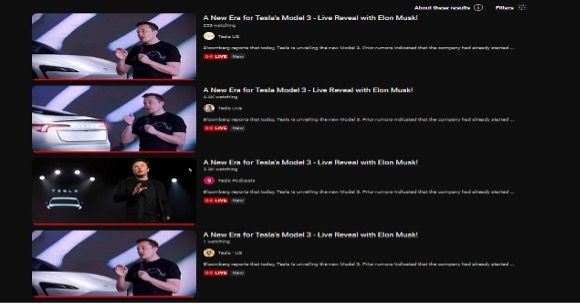
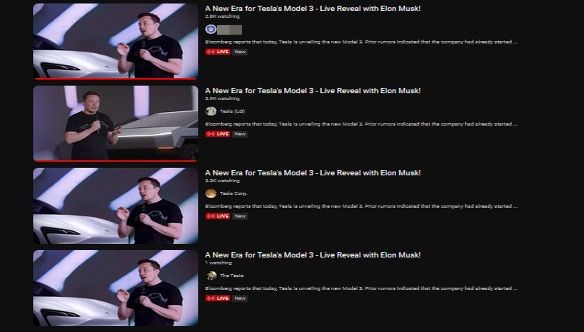
Upon discovering these similarities, it would be rather clear to say that something malicious is happening in the distribution of such generic and misleading content.
On manual inspection, it seems that the content of the livestreams is usually a looped video that’s proprietary to Tesla or that includes Elon Musk (for example, 2023 Annual Shareholder Meeting)
The titles of these livestreams seem to be inspired by official Tesla streams.
These, however, are not ordinary re-broadcasts/re-uploads by fan channels, but rather re-broadcasts that embed a scam in themselves. The commentary sections of all detected malicious livestreams are either disabled or enabled. But here’s the catch: only subscribers of 10 or 15 years can comment (typically long periods of time that wouldn’t allow most of the community to reply). This prevents users who are aware of the scam from commenting and alerting others.

Observing such a “large-scale operation” made us wonder about the channels behind these scams and, upon closer inspection, we noticed that most of the YouTube channels were in fact hijacked/stolen.
The bulk of these “malicious” channels have no other content than the livestream scams themselves – it is assumed that all the original videos were either set to private or deleted because they are not discoverable by any means. The channel description also seems to have been edited to resemble the official Tesla channel, and other relevant contents such as playlists are also presumably deleted.
The process is very likely automated, as conducting an operation on such a large scale would be time-consuming and could potentially give the actual owner of the channel enough time to spot suspicious behavior.
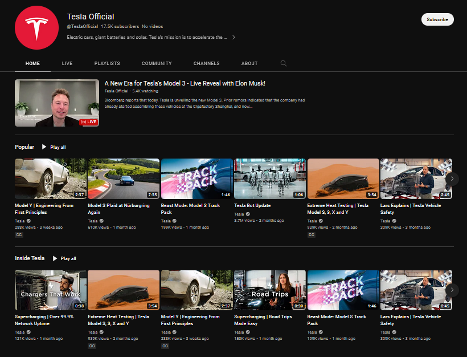
Furthermore, some of the hijacked channels list official Tesla playlists for an air of legitimacy. But this also means the attackers sometimes leave evidence behind.
In some instances, the channel name or handle was not changed (thankfully YouTube has a limit of two changes in two weeks), or instances in which playlists, community posts or even channel videos are still present. Sadly, in most of cases analyzed, it seems that, if the malicious activity is detected by YouTube, the actual channels are deleted altogether. This means that the legitimate owner of the channel will lose everything (videos, playlists, views, subscribers, monetization, and everything that goes beyond the YouTube channel itself while still being related) unless talks are undertaken with YouTube.
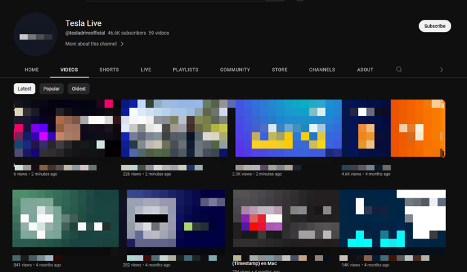
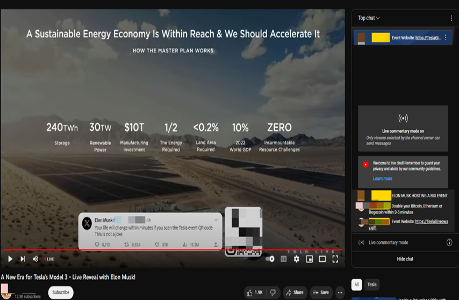
In the cases in which the comment section is subscriber-only, either the actual channel hosting the livestream or specific moderators selected by the channel can leave comments that lead users to crypto scam websites promising life-changing gains on a reduced availability. These moderators also use channel avatars portraying Elon Musk.
One other common detail of both livestreams with enabled and disabled comments is that attackers embed a QR code in portions of the video that leads to a phishing/fraudulent website. If the comment section is enabled, the moderators post the same link that can be found in the QR code.

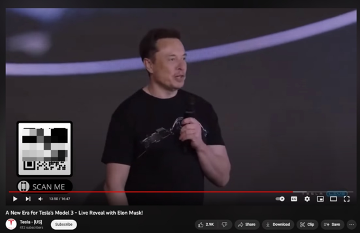
Links propagated via hijacked YouTube channels promote a similar and well-known scam. The ruse involves sending any amount of cryptocurrency (Bitcoin, Ethereum, USDT, Dogecoin, BNB, Shiba Inu, etc.) and promises to send double the amount back to the scammed person. In rare cases, phishing links are written directly in the video.
We’ve also spotted some instances in which the audio and the video looped in the livestream are deep fakes of Elon Musk, through which the hackers try to promote the importance of cryptocurrencies and any event promoted in the referenced links (the crypto doubling scam). The audio deep fakes are of high quality and might seem genuine to the average viewer. During our analysis, we also concluded that some of the livestreams are view-boosted at the beginning of the broadcast, making it look more trustworthy to the public. However, as soon as the view-boosting stops, we see numerous fraudulent livestreams with only 1 or 2 viewers.
The same applies to the number of subscribers – even though there are enough occurrences of channels that have a low number of subscribers, the median value seen in our analysis is close to 2,300. This indicates potential subscriber boosting.
We have also deduced that all of the pages we investigated were created using automated software (phishing kits).
Another interesting detail is that these websites try to prevent saving the content of the page to the disk or opening developer tools by keyboard shortcuts. Doing so redirects (either knowingly or mistakenly) to a page that gives details about the potential actor behind the creation of the phishing kits:

Furthermore, a Telegram channel is suggested and generic details of the kit are mentioned (number of templates, ease of installation and configuration etc.).
Upon searching for the mentioned Telegram group, another one of interest is found, in which the threat actor promotes the phishing kits:
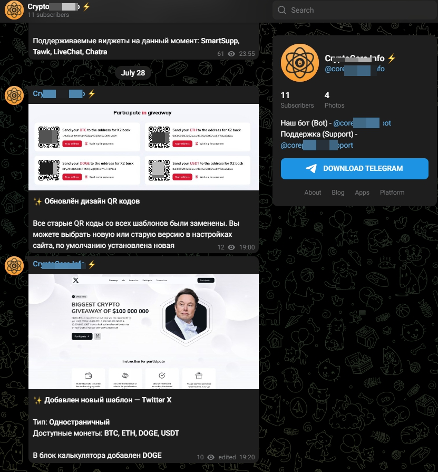
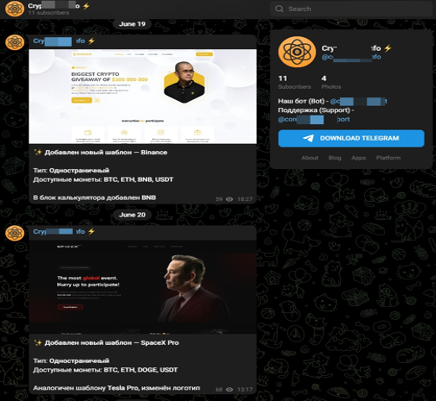
The kits promoted on the telegram group are identical to those found on the hijacked YouTube channels. The websites usually portray Elon Musk as a central figure and are designed to be visually attractive. Moreover, these websites seem to have live chat plugins that would allow the end user to communicate with a so-called “support team.”

Receiving replies is not that common, but when it occurs, they usually try to lead you to send an amount of cryptocurrency to the indicated addresses while also giving reassurances with regard to the legitimacy of the procedure.
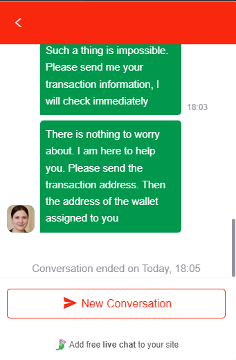
It is unclear whether real people are responding on the live chats, or if the procedure is automated using Large Language Models.
Using both automated and manual procedures, we have found more than 1300 videos that promoted crypto scams on similar websites that likely came from the same phishing kit. It is rather common for videos to point to the same website, but more than 150 distinct websites have been found so far.
All of the promoted scam websites have Cloudflare protection, which increases the difficulty of automatically analyzing them.
A safe assumption would be that lots of videos that also fall in the same category as the aforementioned ones were missed, for various reasons:
- Channels are being taken down by YouTube before the content is found – there does not seem to be a pattern in this direction. Some livestream recordings have stood up for weeks while others were deleted in a matter of minutes or seconds;
- Original channel owners discovering the fraud and taking the necessary measures to eliminate the malicious content and lock the attackers out;
- Limitations related to the manual and automated search – the diversity of these scams could be much greater than what we found;
The impact of such fraudulent schemes can be seen in the community of the channels that were recovered. While some channels recover in multiple steps by stopping the livestreams and setting videos back to public status, the name of the channel remains unchanged, even though the handle was successfully reverted to the original name.
Other channels don’t recover immediately, with significant evidence of getting banned or completely removed due to breaches of YouTube’s terms of service. The specifics of recovering an account after it has been officially removed by YouTube aren’t widely known, but it seems possible.
Having an account completely removed from YouTube for several days could result in both emotional and financial losses (SocialBlade reports indicate that channels with a large number of views, for example in the hundreds of millions, might end up losing tens of thousands of dollars).
Accounts that do not have huge amounts of subscribers or views might never end up recovering the data.
The phenomenon – in numbers
Note: data was collected between 27.07.2023 and 28.09.2023
Further analysis of the obtained data leads to the following interesting measurements:
- Maximum number of subscribers of a hijacked account: ~9,990,000 (for one account)
- Maximum number of views of a hijacked account: ~3.643.275.137 (total views/one channel)
- Subscribers count median value: ~ 2260
- View count of channel median value: ~ 211,820
- Total number of subscribers from the biggest top 10 hijacked channels: ~ 36.950.000
- Total number of views from the most viewed 10 hijacked channels: ~ 10.356.700.312
- Number of distinct channels that were found to be hijacked: 1190 and growing
- Number of distinct broadcasted livestreams that were found: 1370 and growing
- It seems that there are examples of hijacked channels that belong to governmental entities
- Most hijacked channels use a variation of the Tesla official logo or even the official logo itself, with more than half of promoted videos using the same description
Top 10 most subscribed hijacked channels
| Channel name when discovered | Subscriber count |
|---|---|
| Tesla Official | 9.990.000 |
| [Unchanged Name] | 7.700.000 |
| Tesla (US) | 4.900.000 |
| Tesla [Us] | 4.040.000 |
| Tesla Motors | 2.250.000 |
| Tesla Official | 1.990.000 |
| Tesla (US) | 1.730.000 |
| TesIa OfficiaI | 1.510.000 |
| Tesla US | 1.430.000 |
| [Unchanged Name] | 1.410.000 |
Top 10 most viewed hijacked channels (total channel views)
| Channel name when discovered | View count |
|---|---|
| [Unchanged Name] | 3.643.275.137 |
| Tesla [Us] | 1.534.420.831 |
| Tesla (US) | 1.486.112.673 |
| Tesla [Us] | 885.682.783 |
| Tesla Official | 716.998.231 |
| Tesla (US) | 534.394.765 |
| Tesla [MODELS] | 465.659.837 |
| Tesla US | 417.434.100 |
| Tesla Motors | 394.732.381 |
| Tesla US2023 | 277.989.574 |
Note: mentions of [Unchanged Name] in hijacked channel tables refers to the fact that the original channel name was not changed following the account takeover attack
Top 10 most common channel names after hijack
| **Channel name ** | Occurrence count |
|---|---|
| Tesla US | 179 |
| Tesla Live | 126 |
| Tesla (US) | 44 |
| Tesla News | 36 |
| Tesla [US] | 32 |
| TESLA [US] | 32 |
| Tesla Official | 28 |
| TesIa OfficiaI | 19 |
| Tesla | 18 |
| Tesla LIVE | 13 |
YouTube channels with a sizable subscriber count are highly desirable to cybercriminals who can monetize them by either demanding ransom from the legitimate owner or distributing scams and malware to the accounts’ audience.
The lifecycle of YouTube scams proliferated via high-profile can differ, but no matter the case, hackers usually follow the same MO – attracting their prey by leveraging big brand names or personalities to defraud unwary viewers.
The first step of the attack
This scam, faced by more and more YouTube channels, often originates from targeted phishing attacks. The malicious actors send emails that present opportunities ranging from brand collaborations and sponsorship deals to fake copyright notices from YouTube.
The deception lies in the email’s authenticity. It’s presented as a legitimate business proposition. Cybercriminals, especially those targeting popular channels, mimic communications from trusted third-party vendors or use email addresses that don’t raise immediate suspicion.
The attacker’s main aim is to lead the recipient to download a malicious file. This file is presented as an integral component of the brand collaboration or an important document. While it looks like a regular PDF, it carries the Redline Infostealer malware. This malware is known in certain online circles and is traded in underground markets. Its large size, sometimes over 300MB, is designed to slip past many standard security checks.
When the recipient opens this file, it has no immediate visible effects. However, in just 30 seconds, it gathers vital data from the victim’s computer, focusing on session tokens, cookies, and other valuable information.
After this data is collected, even with two-factor authentication activated, the stolen session tokens grant the attacker direct access to the YouTube account, eliminating the need for passwords or other verification. As a result, the channel becomes compromised.
Red flags to look out for in emails
- Unexpected emails or text messages that look like they’re from a company you know or trust
- Emails that use broad greetings like “Dear User” instead of your name/channel.
- Email addresses that look similar to legitimate ones but might have slight misspellings or different domain extensions.
- Emails that prompt urgent action through links or documents attached.
- Messages with noticeable spelling or grammar mistakes.
- Promotions or offers that seem overly generous or implausible.
- Unexpected email attachments, such as PDFs or .scv files (usually its malware disguised as a screenshot), especially if you didn’t request them.
Signs your YouTube channel has been hijacked
- You can’t sign into your account
- Your account settings have been altered
- Your profile picture, description and handle have been changed
- Videos you did not upload appear on your channel
- You receive notifications about unfamiliar devices or locations that access your account
Tips to help protect your YouTube channel from hijackers
- Ensure that your account is set up using a unique and strong password – never recycle passwords, you can opt for a dedicated password manager service to help generate and manage secure passwords across all your online accounts
- Enable additional layers of security such as 2FA or MFA
- Use caution when interacting with links you see in the comment section of your videos
- nstall a security solution to protect against phishing and malicious attacks
- Immediately contact the platform’s support team to report suspicious activity or if you have been logged out of your account
- Periodically review the list of individuals who have access to your YouTube channel and ensure that only necessary users have access, and limit permissions based on roles and responsibilities.
- Review the list of third-party applications connected to your account and remove any apps you don’t use, and only keep those that are trustworthy and essential for your channel.
- Consider using digital identity protection services. These services monitor the web for any data breaches involving your information. If your data is compromised, promptly change the passwords of the affected accounts.
- Practice good password hygiene by changing your YouTube password account every three months.
Internet users also need to be vigilant and learn how to spot compromised or suspicious accounts by:
- Scrutinizing videos with click-bait titles that encourage you to invest in crypto or promise hefty returns in Bitcoin investments
- If it sounds too good to be true, it probably is! Stop and think before you rashly click on links you see in the description of videos
- Never scan QR codes you see in videos promoting free crypto giveaways
- Closely inspect the channel for suspicious activity, such as missing or hidden videos
- Pay close attention to the comment section in videos or livestreams – if the comment section is closed it could be a sign of compromise
- Use a security solution with anti-phishing technology that detects and blocks phishing attempts before they can damage your finances and identity
tags
Author
I'm a software engineer with a passion for cybersecurity & digital privacy.
View all postsWith over a decade of cybersecurity experience both developing and leading developers, and a passion in building things from scratch, I always look forward to the next challenge to sharpen my skills.
View all postsWith more than 15 years of experience in cyber-security, I manage a team of experts in Risks, Threat Intel, Automation and Big Data Processing.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks
















