LockCrypt Ransomware decryption tool

LockCrypt has been around since mid-2017 with a particular focus on business customers. Spreading by bruteforcing Remote Desktop Protocol credentials, this ransomware family has several sub-variants with the following specific extensions:
- .1btc (decryptable and included in this version of the tool)
- .lock (decryptable, not included in our tool)
- .2018 (decryptable, not included in our tool)
- .bi_d (not decryptable)
- .mich (decryptable, not included in our tool)
The ransom-notes it leaves on the compromised machines may have the following names:
- ReadMe.txt
- Restore Files.txt
- How To Restore Files.txt
The encrypted files are renamed using the ransomware KeyStream and further encoded to Base64 to ensure the charset is acceptable as filename. Any encrypted file also gets the victim ID included as seen below:
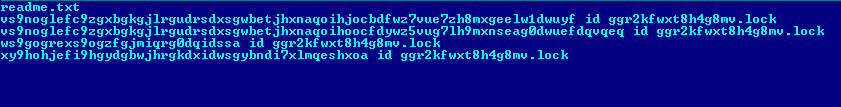
Regular expressions for naming the encrypted files:
- Renaming template: ^[0-9a-zA-Z+/=]+\sid\s[0-9a-zA-Z]{16}\.lock
- Renaming template: ^[0-9a-zA-Z+/=]+\sid\s[0-9a-zA-Z]{16}\.1btc
- Renaming template: ^[0-9a-zA-Z+/=]+\sid\s[0-9a-zA-Z]{16}\.2018
- Renaming template: ^[0-9a-zA-Z+/=]+\sid\s[0-9a-zA-Z]{16}\.bi_d
- Renaming template: ^[0-9a-zA-Z+/=]+\sid\s[0-9a-zA-Z]{16}\.mich
As seen in Fig. 2 and Fig. 3, the two ransom notes preserve several common aspects between sub-families (including typos) but also have notable differences:
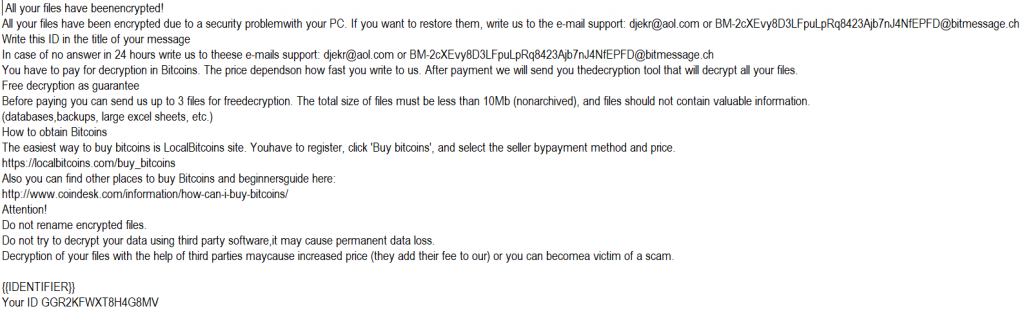
Fig. 2 : [.lock] / ReadMe.txt
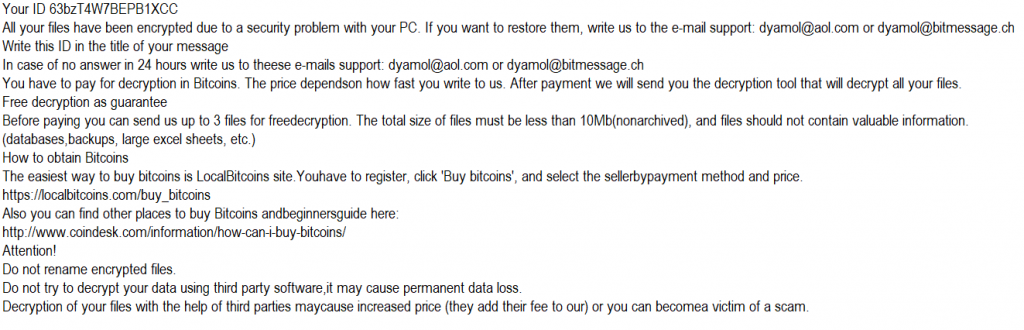
Fig. 3 L [.1btc] / Restore Files.TxT
At this point,our removal tool is optimised to decrypt [.1btc] extension only. We hope to add support for the other decryptable versions in the near future. If you got your files encrypted by this sub-version of LockCrypt, please follow the next 4 steps to try to decrypt your files:
Step 1: Download the decryption tool below and save it somewhere on your computer.
Download the GandCrab decryptor
This tool does not require an active Internet connection.
Step 2: Double click BDLockCryptDecryptor.exe and allow it to run elevated at the UAC prompt.
Step 3: Accept the End User License Agreement
Step 4: Select “Scan Entire System” if you want to search for all encrypted files. Alternatively, just add the path to the folder containing the encrypted files. We strongly recommend that you also select “Backup files” before starting the decryption process, should anything unexpected occur during the decryption process. Start the decryption process by clicking the “Scan” button.
At the end of this step, your files should have been decrypted. The tool generates an operation log in the %temp%\BDRemovalTool\BDRansomDecryptor\BitdefenderLog.txt location.
If you need assistance, contact us at the feedback address listed in the tool. We kindly ask you to attach the above-mentioned log file to help you isolate potential issues and minimize response time.
tags
Author
Right now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













