How to Check if Your Personal Info is Exposed

You cannot see it, but it is there: your digital identity has a life of its own. More precisely, a rich event history that you built up over the years.
The problem is that it is difficult to access that timeline freely because you would not know where to start, and it is almost impossible to keep track of everything you do online. But what if you could?
In this guide, Bitdefender cybersecurity experts teach you how to access your digital footprint and how to successfully manage and monitor it.
How Your Online Activity Exposes Your Personal Information
Before we jump to what you can do to protect your private data, first let’s see what type of information you really need to keep safe.
Four ways your online activity reveals your personal information |
|||
Online shopping exposes your: | Dating apps reveal your: | Search engines & browsers track your: | Social media harvest your: |
Name Gender Email address Delivery address Phone number Credit card details Product search history Frequently bought items Average shopping basket value Most browsed products IP address (which can also reveal your physical location) Device information | Gender Age Ethnicity Sexual orientation Phone number Private chats Political views Private pictures sent via DMs Likes & swipes IP address Device information | Online searches Browsing history Online interests Shopping habits IP address Location Passwords and Credit Cards (if you store them in your browser, which we don’t recommend) Device information Downloaded files Browser add-ons you use | Posts, photos & videos (including deleted ones) Messages & files (sent & received) Phone contacts Name Gender Email address Location Phone number Date of birth Relationships Groups or group chats Posts, pics & videos you’re tagged in & more |
Now imagine what can happen if you put all these details together. The result is a very accurate image of your digital persona that is sometimes even more precise than you expect.
Once they build an online profile of you (now closely tied to your offline life), you may be exposed to cyber-attacks, social media impersonation or digital identity theft.
What Is the Most Frequently Exposed Type of Personal Information?
Cyber-criminals love data leaks. The bigger the volume and juicier the data, the faster and more aggressively they can use it, sell it, and make a profit.
Data breaches frequently expose personal information such as:
- credit cards, bank details or other financial information
- Social Security numbers
- driver’s license information
- home addresses
- phone numbers
- email and password combinations
- medical records
- biometric data (fingerprints, full face photography)
- behavioral data (preferences, online activity history) and much more.
Just in the last ten years, hundreds of global organizations (including governments) experienced data breaches. This resulted in massive leaks of sensitive information about millions of individuals from all over the world.
In fact, it is estimated that, on average, 300 million people are affected by data breaches every year. That means malicious actors are taking full advantage of the situation. They are actively:
- collecting as much data as possible
- corroborating it to build accurate profiles for potential victims (including the relationships between them)
- leveraging this leaked data to launch further, more targeted attacks with higher chances of success.
Sadly, a universal solution does not exist yet, however there is something you can do to find out what personal information is out there and if a cyber-criminal is using it against you.
How to Check if Your Personal Data is Exposed
“So how do I check to see if my information was leaked online?”
Most advice out there will nudge you to start checking your main accounts one by one and see if your email info was leaked, for example. While that is a good way to start, it is also time consuming, and you will probably need extra help in the task of securing your private information.
That is why we developed Bitdefender Digital Identity Protection, a monitoring service with a real-time online dashboard (no download required), which can save you considerable time and effort.

Let’s take a look at what it does to keep you safe from online privacy threats such as identity theft and social media impersonators.
See Your Digital Footprint at a Glance
When you first log into Bitdefender Central, after activating your subscription for Bitdefender Digital Identity Protection, the monitoring service will automatically start mapping your digital footprint.
You then get a few prompts to validate if certain usernames, email addresses, and other personally identifiable information is (or has been) yours. This Accuracy Check helps the service better understand your online profile.
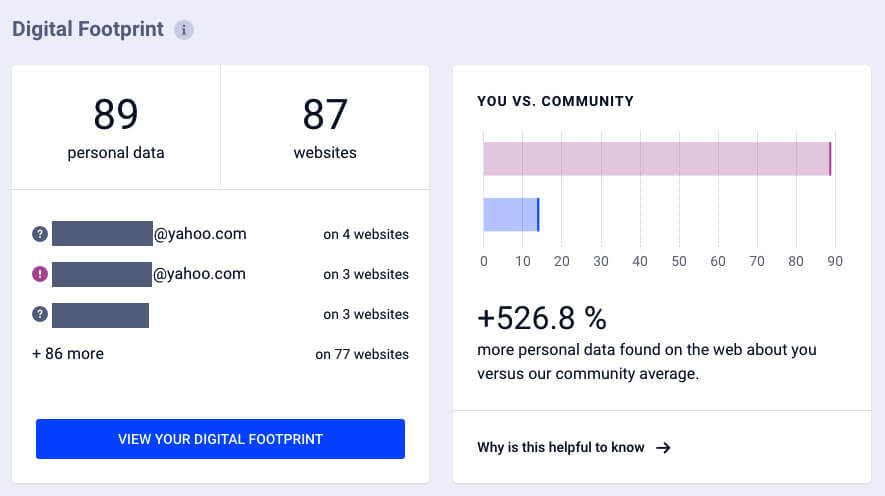
You even get to see how your “digital dossier” evolved over the years. It can sometimes be a real eye-opener as to how much information you are leaving behind.
Check Your Data Breaches History
Bitdefender Digital Identity Protection only needs your email address and phone number to crawl data leaked from breaches to see if your information was exposed.
You get a full list of organizations that revealed your details and what type of personal information was exposed. Plus, you get a bunch of action tips for each data breach so you can start closing those gaps in your online security.
This is just the beginning because, every time your personal information ends up in a data breach, Bitdefender Digital Identity Protection updates the chart and notifies you so you can act quickly and minimize the impact..
The larger your digital footprint is, the higher the chances of you being exposed on the web, giving cyber-criminals and scammers plenty of opportunities to sneak into your devices and software and use them to defraud you or leverage your good reputation for their gain.
How to Check if Your Email was Leaked
When you start using Bitdefender Digital Identity Protection, you get ongoing breach monitoring for five different email addresses. The best part is that it happens automatically: all you have to do is fill in the details and it takes care of the rest.
As it crawls the visible and inaccessible parts of the Internet (even the Dark Web), Bitdefender Digital Identity Protection may come across older email addresses you used at some point, which can still expose your personal information.
How to Check if Your Password was Leaked
When Bitdefender Digital Identity Protection scours the Internet for bits and pieces of information and tracks them back to your identity, it also checks for leaked passwords.
Your online dashboard also includes the recommended steps to take for each of your accounts involved in a data breach. Most often it will advise you to change your password and turn on two-factor authentication if that is an option.
How to Check if Your Account Information Was Leaked
Besides usernames and passwords, your online accounts pack a lot more info than you may realize. Service providers often ask for your physical address, credit card details and personal preferences to deliver your order. Data breaches spill this information into places malicious hackers can access, such as public repositories or Dark Web forums.
Each warning from Bitdefender Digital Identity Protection includes the type of information that was exposed because of a data breach.
Moreover, you may be surprised to find out that your private information was leaked through companies you have never used or even heard of. These data enrichment companies, also known as data brokers, often operate in grey areas when it comes to ethics, pulling together facts about individuals and selling these enhanced profiles to the highest bidder.
How to Find Out if Your Email Is on the Dark Web
Bitdefender Digital Identity Protection scans millions of websites and monitors the underground networks to check if your information was leaked on the Dark Web.
Now you may be wondering: “can I remove my email from the Dark Web?”.
Unfortunately, the answer is no. Once it is online, permanently deleting data is a difficult task. But there is still a lot you can do to protect your online privacy.
How to Check if Someone is Impersonating You on Social Media
Sure, you could run periodical online searches on the main social media platforms and do the same using search engines. But this is a lot easier with the Impersonation Check from Bitdefender Digital Identity Protection.
Once it identifies profiles that seem to be using your personal information, you can take action. After you validate the accounts you own, Bitdefender Digital Identity Protection constantly sweeps social media platforms for potential impersonation attempts.
This helps you act fast and limit the potential damage that can span from a mild scam to tarnishing your reputation to the long-term damage of digital identity theft.
What to Do if Your Personal Information Is Compromised
First, follow the recommended steps that Bitdefender Digital Identity Protection provides. This often includes changing your passwords and turning on two-factor authentication.
There are also other steps you can take:
- Watch out for phishing and scams such as fake antivirus messages, deceptive package delivery messages, phony calls from tech support you never contacted
- Monitor your credit card or bank account statements for expenses you’ve never made
- Check for suspicious logins into your accounts and activate notifications for them if the service you use provides them
- Be on the lookout for misleading password retrieval emails and messages and only change your credentials by logging into the account from the official website
- Check for signs of identity theft such as IRS notifications about more than one tax return filed in your name or collection agents contacting you to settle debt you have never taken on.
Cautiousness goes a long way when it comes to your online privacy and security, and preventing attacks before they happen can save you a lot of time, money and peace of mind.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

