How Does a VPN Work to Protect You?

The more you care about your online privacy and the more you protect it, the better you understand how technology can influence your life, your work, and your future.
Knowing how a VPN works and why you need to use it for your security can make all the difference in having a private digital space where you are not tracked or monitored.
Take a minute to learn from cybersecurity experts how to have a smaller digital footprint by using a VPN, to make sure your private information really stays private.
What is a VPN? A Quick Recap
Interested to know more about what a VPN really is? By definition, a VPN (Virtual Private Network) is a software program that hides your true IP address.
This layer of protection is essential because your IP address includes information that pinpoints your real location, down to the GPS coordinates:
- Internet Service Provider
- City, State, Region, Country, Continent
- Time zone, postal code
- Latitude and longitude
- Connection type (broadband)
- IP assignment (static or dynamic)
- IP language
- Hardware specifications
When you use a VPN, a website operator or a mobile app owner can determine the IP of your VPN provider, not your real one, effectively hiding all these details.
A VPN also includes several other security and functionality-related benefits. Besides protecting your IP from mass data collection, scammers, and cyber-criminals, using a secure VPN improves the safety of your overall online activity.
A VPN that keeps no traffic logs helps you leave a significantly smaller digital trail on the web. This prevents Internet Service Providers (ISPs) from collecting information about your location, the websites you visit, the ads you see, the type of online content you consume, and the physical places you use your device from.
The fewer details can be collected about you, the lower the risk of personal data exposure in case the information is stolen (if they become the target of a cyber-criminal attack).
How Does a VPN Work?
When you use a trusted VPN, a network of secure servers (spread around the world) camouflages your online activity. It sends your data over the Internet from one location to another without revealing it.
This enables you to safely send and receive information across shared or public networks – unprotected Wi-Fis included – through an encrypted VPN tunnel.
How Does a VPN Connection Work?
With your VPN app open, simply hit the "connect" button and you will get a random IP assigned to maximize your Internet speed, or you can choose a specific country to get an IP from.
Once turned on, your VPN encrypts your data as it sends it through the secure servers of the VPN provider. They can be either physical servers or virtual ones.
Using a VPN is like using a significantly safer network on top of the usual network you use when connected to the Internet.
The VPN servers form a secure tunnel that protects your data from prying eyes and interference (malicious software or phishing attempts).
Moreover, you will not lose the speed advantage you have when you are not using a VPN.
“You may be concerned that the VPN will slow down your connection. Actually, it’s the opposite. The VPN uses compression at the origin so that means that you’re going to do less traffic when using VPN and your internet might actually be faster than you would expect it to be.”
Alex "Jay" Balan (Director of Security Research, Bitdefender)
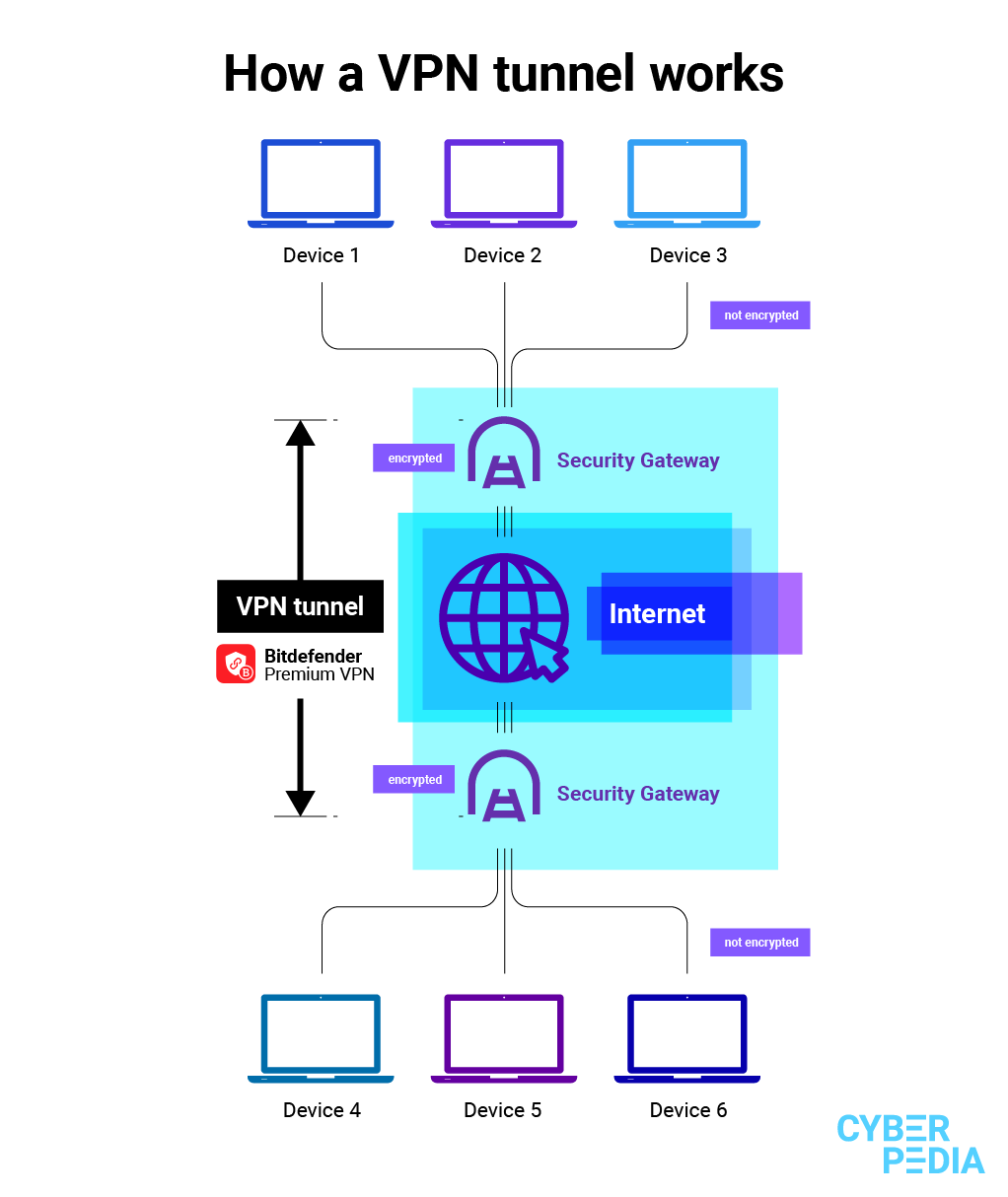
How Does a VPN Tunnel Work?
A VPN tunnel applies encryption to your data in transit (meaning data that is actively traveling through the Internet). This prevents unauthorized parties from viewing the data, which means they also cannot collect it, modify or otherwise manipulate it.
To make sure your data always always travels through the secure VPN tunnel, you can choose to run Bitdefender Premium VPN at startup. It will automatically start each time you turn on your device, casting a layer of encryption over your online activities until you switch off for the day.
A reliable VPN will also give you a wide range of servers to choose from. Typically, top VPN providers will have their network of secure servers spread in countries with stringent data protection laws.
How Does a VPN Server Work?
A VPN server is a piece of computer hardware or software with a dedicated configuration that enables it to deliver VPN services to users from all over the world. Multiple users can connect to the secure, private network a VPN server provides, as it is set up for performance and stability.
Once you activate the VPN on your device, your data gets encrypted and reaches the VPN server the same way, which shields your IP and internet traffic details from your ISP and other snoopers. When the data you are trying to access reaches your device, the VPN app will decrypt it for you, so you can read and use it.
What is also specific to a VPN server is that it uses a range of security protocols specifically implemented for stronger privacy and protection. Some of these protocols focus on encrypting your data, some of them on ensuring its integrity, while others filter unauthorized and malicious parties from accessing your data.
“The first thing you need to do is to make sure that the VPN solution is actually working. Many times, some VPN solutions will expose your real IP address when they misfire, when they encounter an error, or they shut down. We have tried to create a VPN solution that prevents these accidents from happening.
If you’re in the middle of something and your VPN solution drops, your IP address will not be exposed. It’s the Internet connection that goes down and resumes with the IP address of the VPN server that you chose.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
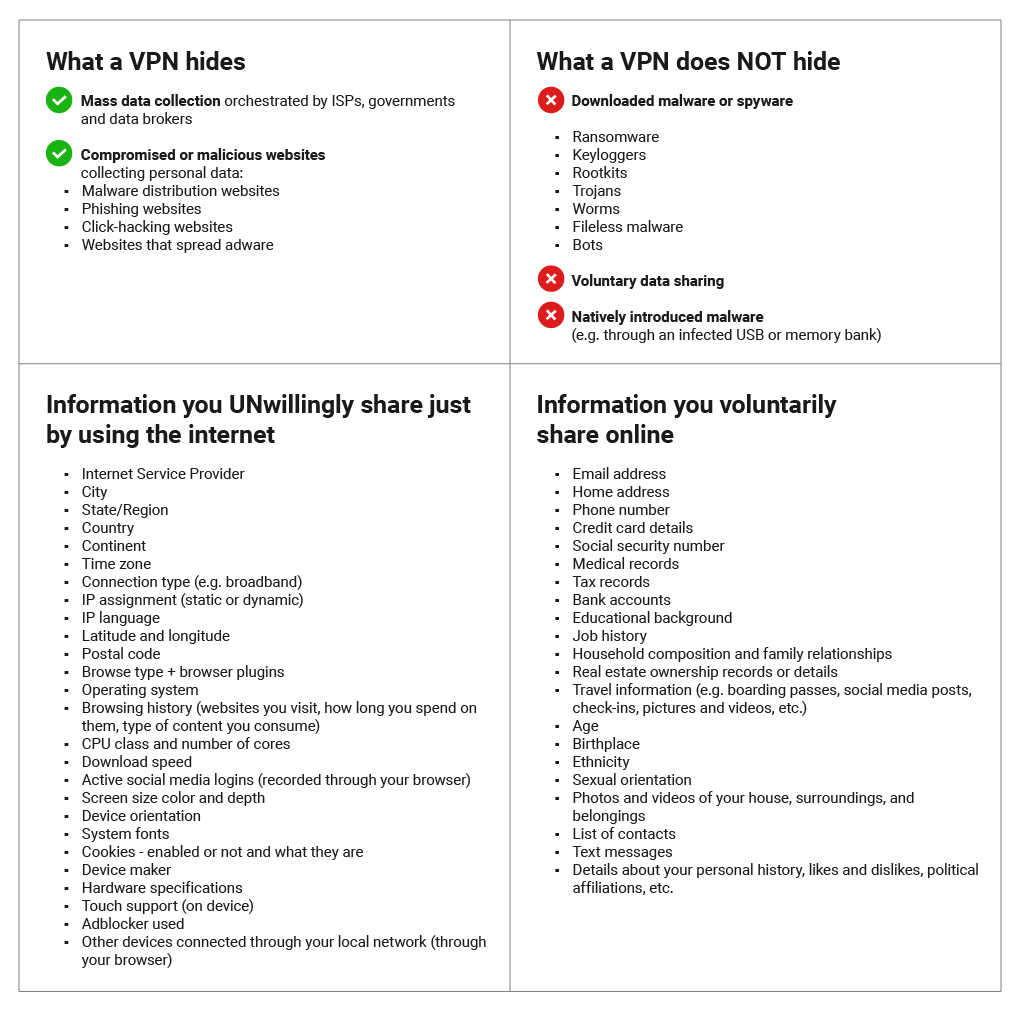
What Does a VPN Hide?
You may be surprised to find out how much information you give away simply by using the Internet, even if you do not actively share these details yourself. This is what mass data collection has focused on gathering and what has made a secure VPN a necessity in every person’s setup.
Types of VPN - Essential Differences
There are two main types of VPN products available on the market:
Remote access VPNs enable users to connect to a private network and access the services and resources it provides from a remote location. While the connection from the user to the network happens through the Internet, it remains secure and private due to the VPN’s encryption protocols.
You may already be familiar with this type of VPN from the work-from-home context, where employees need to access their company’s resources while not at the office. The same logic applies to home users who use a VPN to reduce their digital footprint, bypass regional content restrictions or safely download content.
Site-to-Site VPNs are another category that large companies usually use. They employ this type of VPN to connect branch offices located in various geographies and make sure they can collaborate effectively.
These two types of VPNs also mark another distinction, depending on their use case: for business or personal use.
If you look at the number of protocols a VPN uses, you can also differentiate between multi-protocol and single-protocol VPNs and between those that keep logs and no-logs VPNs (that do not record any details of your online activity).
From laptops to mobile devices and desktop computers, it has never been easier to use a VPN as a daily habit that constantly improves your online privacy.
For example, Bitdefender Premium VPN gives you unlimited encrypted traffic for up to 10 devices, keeps no traffic logs and makes online media streaming and downloads safe. Plus, it also includes protection against a range of malicious websites that try to collect your information and can infect your software or your device with malware, spyware, or other cyber-threats.
“Our implementation of VPN helps people both secure against malware and privacy invasions by filtering some malicious URLs - something that’s not typical of a VPN solution.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
As always, the best digital protection you can build includes multiple layers that complement and boost each other, working together to keep you safe.
A reliable password manager, a powerful antivirus solution, a secure VPN, and constant updates for all your apps and software. Or even try an all-in-one protection mega-suite which includes them all.
The best part? Once you set them up, you will be surprised at how easy and effective it is to have peace of mind and privacy protection that works and never interferes with your daily activities.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

