What Is Your Digital Identity? (And How to Keep it Safe)

As we spend more and more time online, we are constantly generating data for cyber-criminals to target. This is why it is important to choose the right tools to protect our digital identity, activity, and personal information.
With so many options available, it can be difficult to know which tools are the best, how they work, and if they overlap. To help you make the best choices, here is an easy-to-follow guide put together by our team of cybersecurity experts.
What is Digital Identity? A Definition
The term ‘digital identity’ can mean different things to different people. To get an accurate definition, let's turn to cybersecurity experts to clear up any ambiguity.
"Digital identity is a very complex topic, and it consists of different data points that people leave behind when they interact with the Internet. From the easiest to spot, I would say that these data points are your name, your address, your browsing habits, your home location, maybe, and so on.
But if we go deeper into the more complex topics, somebody’s data points also consist of, for instance, medical history, diseases, list of medications they take, and so on. So all this information pieced together depicts a person’s digital life at a very, very granular level, much more than we usually think of."
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
When you realize that your digital identity is an extension of yourself in the digital world, you will want to see where your digital footprint begins (and where it ends).
Bitdefender Digital Identity Protection can help you do just that. It maps and monitors your digital footprint, so you can see where your personal data is and take the necessary steps to protect it.
Here are the three components that make it a powerful tool for understanding your exposure to online scams, cyber-attacks, and surveillance.
Let's take a closer look at each one.
Digital Footprint Mapping
Having a comprehensive and detailed view of your digital identity means having the facts to back up your assumptions. For example, you might think you're not that exposed online, but a powerful monitoring tool can show you otherwise.
Automatically finding private information online in legal and illegal data collections
- Starting from your full name, your email address, and your phone number, Bitdefender Digital Identity Protection combs the web for details associated with your person. It then organizes them into a repository you can access anytime from your Bitdefender Central dashboard.
Constantly improving accuracy based on the data you validate
- When Bitdefender Digital Identity Protection finds new accounts, email addresses, and phone numbers associated with your digital identity, it asks you to verify them. This improves the alerts you get when the tool comes across new bits of data that point to you.
Auto-updating the visual graph of your online exposure
- Bitdefender Digital Identity Protection not only digs up your information that is spread across the Internet, but it also presents it in context so you know what is important. Your digital footprint is compared to the average community exposure, so you can understand the status of your personal data.
Digital Footprint Monitoring
Once you give away your personal data, whether knowingly or unknowingly, it takes on a life of its own. Cyber-criminals will use your information, sell it, trade it, and manipulate it to get money, influence, or both.
While it is essential to take all the precautions you can to protect yourself against data breaches, it is also important to be aware of the sensitive information you may be unknowingly leaving out in the open.
Bitdefender Digital Identity Protection constantly monitors your data and immediately alerts you if your private information is leaked, if someone tries to impersonate you on social media, or if someone uses digital identity theft techniques to commit fraud in your name. The email alerts also include guidance on what to do to minimize the damage.
Guiding Remediation Through Actionable Education
Having the right information at the right time is critical to taking meaningful and effective action to protect your digital identity.
Bitdefender Digital Identity Protection provides you with actionable advice in context, on the spot. This means that you will receive specific guidance on how to protect your digital identity, based on the specific risks that you face.
- If it finds that an account you own was involved in a data breach, it will tell you how to curb the damage.
- If it finds that you are sharing too much personal information with a platform, it will show you how that platform is using your information and what you can do to minimize your exposure.
- If it detects a social media impersonator, it will tell you which details to evaluate and how to report them.
Identity protection vs security products: what is the difference?
Let’s take a look at how three of the most important tools in your online security and privacy toolbox work to keep you safe.
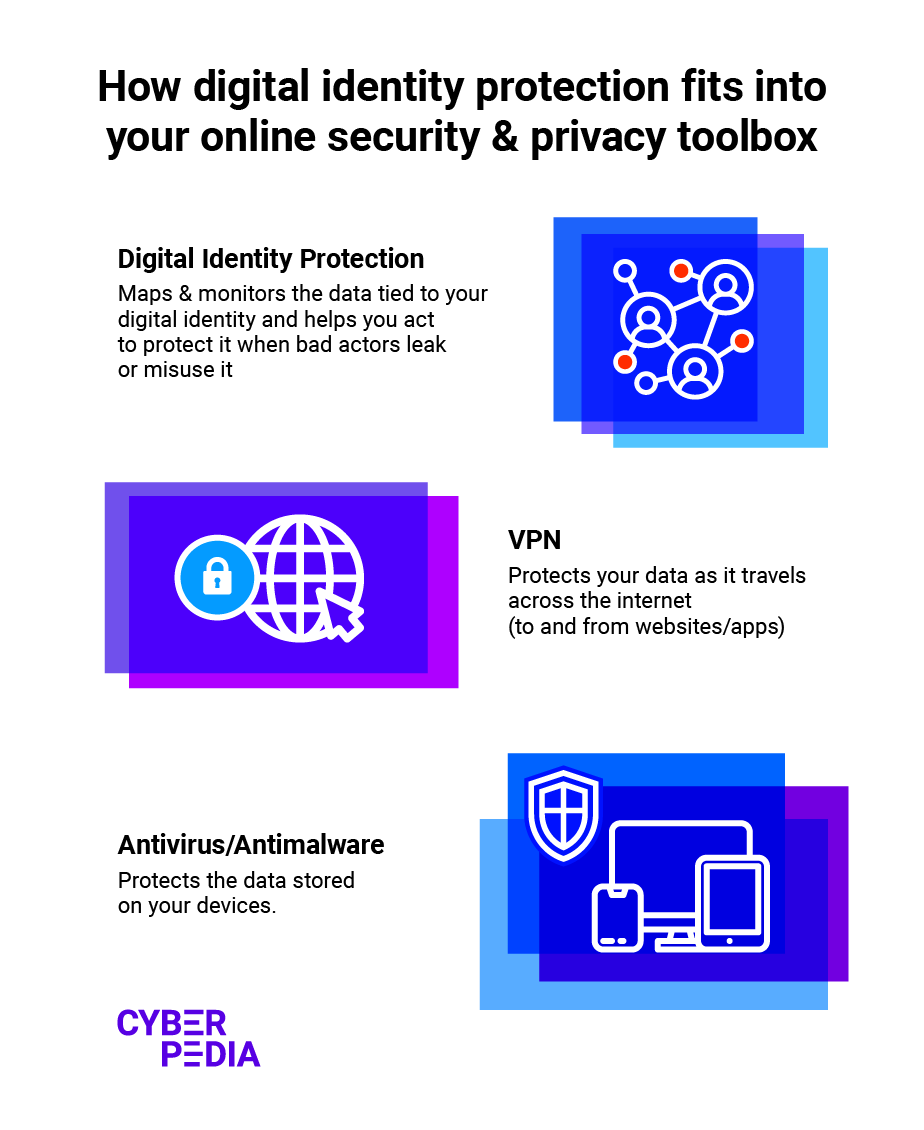
As this quick overview highlights, the role of digital identity protection is to provide you with a comprehensive view of the type of data that malicious actors can find about you on the Internet.
If you want to protect your data and privacy online, you need to know how your data is used and what to do if it has been exposed in a breach. You can also improve your protection by doing small things regularly, like changing your passwords and being careful about what information you share online.
By following these tips, you can make the most of a solution like Bitdefender Digital Identity Protection and experience the benefits of acting on expert advice.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

