What is Social Media Impersonation? Action Tips for Cautious Users

Nothing to worry about? A mild nuisance? A serious issue that makes you anxious?
No matter how you feel about social media impersonation, it is still a serious threat to your online privacy, safety, and peace of mind.
You might think that just because someone is using your online identity to create a fake account does not have long-term consequences. However, cybersecurity experts will show you how social media impersonation can sometimes spiral out of control in unimaginable ways.
Believe it or not, it all starts with your social media presence, and better managing your digital footprint. Curious how? Let’s start with the basics.
What Is Social Media Impersonation?
Social media impersonation is a form of digital identity theft. Using this tactic, a cyber-criminal or scammer creates a profile on a social platform using personally identifiable information (name, picture, location, background details) stolen from a certain individual.
The first step is to manipulate the victim’s contacts into thinking the fake profile belongs to a real person they can trust. Then, the end goal is to use that impression of authenticity to exploit those who interact with the fake account (by asking for information, money, or discrediting the owner of the account).
Impersonating real people on social media falls into the larger category of social engineering, a series of tactics that rely on psychological manipulation. The intention is to trick victims into revealing confidential information or act despite their better judgement.
Malicious actors impersonate both individuals and organizations on social media platforms to carry out their illegal activities.
Although some people may perceive social media impersonation as a mild annoyance at most, cybersecurity experts consider it a very serious issue.
Because it is a type of identity theft, it falls under the 1998 US Identity Theft and Assumption Deterrence Act. Through this act, the Department of Justice defines the felony as the situation where a malicious actor:
“knowingly transfer[ring] or us[ing], without lawful authority, a means of identification of another person with the intent to commit, or to aid or abet, any unlawful activity that constitutes a violation of Federal law, or that constitutes a felony under any applicable State or local law.”
Depending on the gravity of the actions and their consequences, social media impersonation can also involve harassment, credit card fraud, computer fraud and financial fraud which fall under the provisions of this Act.
So if you are wondering if creating a fake account is illegal, you now have your answer.
Chances are you have already interacted with fake accounts at least once in your digital life so far.
Types of Social Media Impersonation
Here are the main types of social media impersonation to look out for when engaging with people and organizations on your favorite social platforms.
Personal Account Impersonation
With so much personal information available on billions of people around the world, it is easy for cyber-criminals to copy information and piece it together to create a seemingly real profile.
They even have tools to automatically generate fake profiles and post content to make them seem authentic. This makes their malicious actions easily scalable.
You have probably read news around account take-downs that involved millions of fake accounts used for anything from digital fraud to propaganda. Hackers are generating them by the thousands, and it is happening constantly – even as you are reading this.
Social Media Account Hijacking
Another type of impersonation happens when cyber-criminals break into legitimate accounts and use them to distribute malicious or fraudulent content.
There are multiple examples of this, because popular accounts with millions of followers on Instagram, Facebook, and Twitter are especially attractive targets. From business leaders to politicians and celebrities in the entertainment industry, no account is off limits for scammers.
Fake Accounts or Bots
Another type of social media impersonation comes from bot accounts.
Generally speaking, a bot consists of a software application that runs tasks online in an automated manner. They give online criminals a massive potential to amplify their malicious operations because bots can perform a high number of tasks.
“Fake accounts are dangerous because cyber-criminals use them to lure other people into different types of scams.
One of the most frequently encountered scams is social network accounts run by bots that impersonate the military. There’s this decorated war hero fighting somewhere in Afghanistan and planning to retire. They contact senior people and try to establish some sort of a personal connection which would eventually lead to romance.
These bots are trying to convince the victim they’re real people with genuine intentions and the only thing that separates the two of them is distance and shortage of money. So, eventually, the victim ends up getting scammed for ticket money or emergency funds they need.
It’s such a popular and heartbreaking scam that Australia, for instance, has issued numerous warnings, particularly to senior people, to make them aware of these scams.
Never engage with people who are supposedly working in the army and attempt to meet you because you’re falling for a modern version of the Nigerian prince scam.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
On social media platforms, bots can:
- post automatically generated content
- spread malware-infected links and provocative ideas (usually disinformation, propaganda and other types of manipulation)
- follow users
- join groups
- amplify messages with a huge number of posts and shares
- generate fake followers to make these accounts seem legitimate
Unfortunately, to this day there are no rules and regulations to cover the implications of bot accounts on social media and other online channels. Therefore, their activity is virtually unrestricted. For example, over the last few years we have all seen (and continue to discover) the political implications of social media bot activity around the world.
“Bots can also do other things like incite panic or spread malware. Sometimes, bots can even be used as command-and-control servers. A few years ago, there were a couple of instances in which Twitter accounts were used to send commands to malicious software that infected victims’ devices.
So bots can do a lot of things, but they’re mostly related to trying to deceive people in some way or misinterpret or manipulate information. Or, as we’ve seen recently, amplify content.
For example, imagine you have an army of bots or fake accounts. If you want to get a story trending, all you have to do is post something on one of those accounts and then use the rest to amplify it and make sure it reaches as many people as possible. If it catches on like wildfire, it’s going to be difficult for people who don’t do a lot of fact-checking (which we should) to identify the truth. They’re going to believe the type of information that’s being propagated by those bots.”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
Executive Impersonation
Another specific type of social media impersonation is duplicating the identity of business executives.
Attackers and scammers set up accounts with executives’ names and other legitimate personal information. Their intermediary goal is to connect either with people inside the target’s organization or with potential business partners.
The final objectives range from harvesting sensitive information from trusting employees to defrauding unsuspecting individuals into sending money to the scammers through fake business proposals or false job openings.
This particular type of threat can have lasting consequences both for the individual and for the larger organization. The more important the executive’s role, the higher the reputational risk.
Brand Impersonation
Using trademarked content (name, logo, images), they set up business pages, engage in conversations with genuine social media users, run fake promotions and even respond to customer support questions. These activities are meant to boost activity on the fake profile and increase its appearance of legitimacy.
The objective is to collect as much information on as many people as possible by engaging with them one on one or directing them to websites infected with malware or to phishing pages that solicit personal information (home address, phone number, credit card details, PIN).
“There are plenty of examples in the brand impersonation category because scammers usually ride on the popularity of brands.
One such example would be giveaways and other raffles that use the names of supermarkets to lure customers into clicking on malicious links which leads to having their information or their online banking credentials stolen.
Other types of brand impersonation can actually happen in what we call ‘competing wars’. The tactic might be used by organizations to hijack a different brand and tarnish their reputation online just by posting jokes or discrediting these companies in the eyes of their current customers.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Why Does Social Media Impersonation Work So Well?
There is a combination of factors that makes it easy for fraudsters to carry out their attacks and scams.
From their perspective, it is easy to create fake profiles, copy information, buy followers and generate activity on the account that mimics the writing style of the person or organization they are impersonating. They can even disguise their fraudulent content sandwiched between legitimate posts in your feed.
As humans, we are wired to trust others. We also have a deep need for connection which we are increasingly satisfying through digital interactions. We tend to consume content fast, pay less attention to it, and get excited about opportunities that seem to match our interest or surprise us. We also let our guard down when using social media because we are mostly there to relax, have fun and be entertained.
Cyber-criminals know all these things. They play on our psychological traits and human needs to get what they want, whether that is data or money – often, both.
That is why social media impersonation is not just a mild inconvenience we can easily dismiss. There are teams of researchers and other cybersecurity specialists who work alongside law enforcement, legal experts and academia to find reliable solutions to curb this type of online threat.
How Hackers Take Over Social Media Accounts
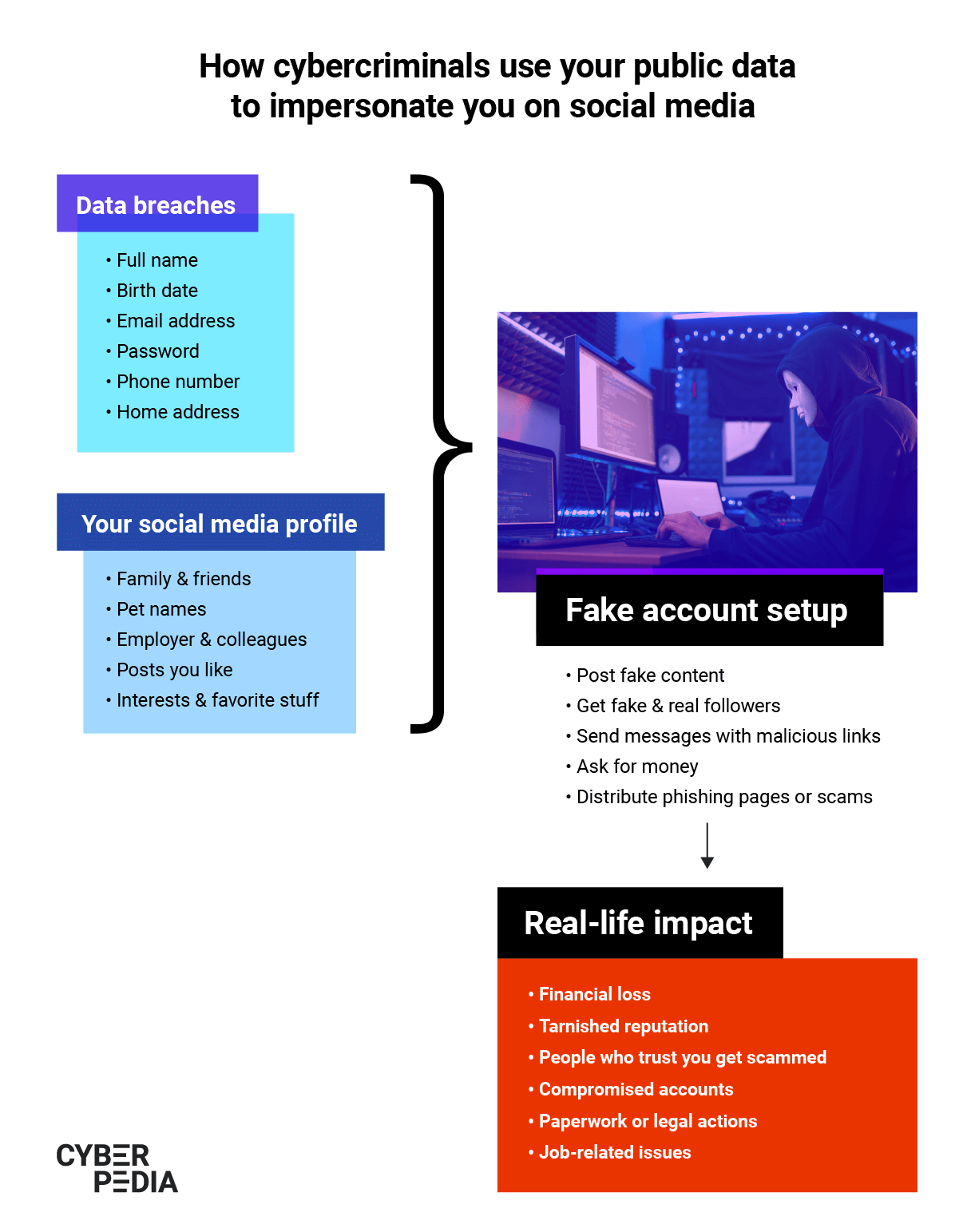
It has become strikingly easy for cyber-criminals to break into social media accounts. All they have to do is leverage the overflow of personal information leaked through data breaches.
Here is what attackers do with this personal data that includes email/username and password combinations, personal addresses, telephone numbers, and a range of other details.
“One of the most frequently encountered methods that expose social network accounts is credential stuffing.
Data breaches generate a lot of information about us, that’s for sure. Some of the information includes usernames and passwords. With those credentials, cybercriminals attempt to log into different services, including social networks. They can do so at a very high rate because they have a lot of computing power (and time to spare!).
If users have reused those leaked passwords, they will – sooner or later – find a matching identity on social networks that accepts those credentials and take over the account.
From there on, attackers are just clicks away from conning other people into installing malware, donating money or even going through private conversations or sending private pictures.
Credential stuffing is still the number one problem associated with digital identities and it works very well even now, 20 years after the Internet boom.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Credential stuffing or brute-forcing is a type of attack where a hacker tries multiple combinations of usernames and passwords to log into your accounts. To make sure their attacks are increasingly effective and to avoid triggering security alerts, cyber-criminals routinely buy lists of hundreds of millions of leaked emails and passwords. They eliminate unsuccessful combinations from their attacks and use fresh data leaks to increase their success rate. They also use timing to avoid being detected by automated security systems social networks have, creating fake accounts weeks before the actual attack.
Besides brute-force attacks, phishing is also a common tactic used to gain control of a social media account. It may look like a link you receive in a private message with a question meant to determine you to click on it (“Hey, I found this picture of you online!”). The link usually leads to a fake page that asks you to fill in your username and password which the attacker can then collect and use to lock you out of your account.
Because social media impersonation is a form of digital identity theft, it can also have lasting consequences. One of the least visible repercussions is that, once captured, your data goes on to live in cyber-criminals’ systems and the underground economy.
Moreover, if you’re using your social media accounts to log in to other services and products, once malicious actors crack your username/password combination, they can also access those.
Unfortunately, once your data is out there, there is no way to reverse the process. Often, victims have no idea they are being impersonated and this type of digital identity theft can go undetected for a long time.
The highest risk is the one related to your non-perishable personal information which includes your birth date, your parents’ names, your social security number, and other details that remain unchanged throughout your entire life.
“There are various goals attackers will try to achieve when compromising a social media account.
One of them is perpetuating the attack: using your contacts list to distribute other pieces of malware to your contact list or to scam them.
There’s the financial motivation: once they gain access to your account, you’re either subjected to potential blackmail or they can gain access to your financial assets.
There’s the reputational damage that’s connected to both blackmail and financial loss. And there’s also the fact that they may use your account to spread propaganda, for instance.
Granted, if your account is compromised and at some point and it starts spreading misinformation, links to fake, fraudulent campaigns or information that is not legitimate or is misleading, your contacts will likely try to let you know that something’s going on.
However, most of these attacks are not that obvious. So whenever attackers gain access to your accounts, they’re usually trying to monetize that coverly, either by using the data they collect and selling it on the Dark Web or directly going for your financial assets.”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
What To Do If Someone Impersonates You on Social Media
If you discover someone is pretending to be you on a social network, here are the steps you should take to limit the damage:
- Take screenshots of the fraudulent profile and any related activities
- Do NOT contact the imposter and avoid engaging with them - you don’t want to tip them off
- Warn your contacts about what’s going on, so they will act with caution
- Report the impersonation using the platform’s dedicated support section
- Check the accounts where you have used the social network as a login option and change your passwords
- Use an online privacy service like Bitdefender Digital Identity Protection to get alerts when malicious actors use your email addresses or when social media impersonators set up accounts using your personal information
- Keep an eye out for suspicious activity not just over the following weeks but generally as you go about your business online.
“And, of course, do your due diligence. Constantly check for your online presence, constantly Google yourself, or use digital identity protection tools to ascertain whether or not the accounts that there are online or the information that is online is indeed related to you and not some fake profile.”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
This is reliable advice for the networks where you have an active presence. But what about all the others? What should you do if someone impersonates you on a platform you do not have even an account with?
“You can’t really report something unless you’re a member because the social network will have no record of you whatsoever. They don’t have the original to compare against the impersonator.
So, for once, it may be a good idea to book your handles in advance, even if you’re not going to use them. This way, you’ll be able to claim them and make them unusable for somebody who would like to build an online person on our behalf.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Can You Report Social Media Impersonation to the Police?
Absolutely!
The US government encourages you to report malicious and fraudulent activity that involves digital identity theft, imposter scams, fake prizes and sweepstakes, and many other types of cyberattacks.
There is also an international Internet Crime Complaint Center (IC3) that you can turn to no matter where you live.
The more data authorities have on these scams, the better they can act to curb their impact.
Social media impersonation is an extremely versatile attack tactic that gives cyber-criminals many ways to use and manipulate your data, reputation, and network. It is one of the fastest-growing threats as billions of people use it not just for entertainment but also to get their news, cultivate relationships and grow their careers and businesses.
The risk of impersonation on social platforms is bound to get even greater as synthetic, AI-generated content (such as deep fakes) gives attackers a whole new range of tools to manipulate your perception and override your mental safeguards.
Using a reliable digital identity protection service to create an automated early-warning system for impersonators and constantly educating yourself on this topic puts you in a much stronger position.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

