Exploring The Spectrum of Threat Intelligence Types

Security companies understand the crucial role threat intelligence (TI) can play in hardening security, reducing alert fatigue, and accelerating incident response. It’s not a question of if security providers need TI, but rather what kind of TI they need, and where they should get it from.
Unfortunately, the industry can’t agree on a set of standards for how we define threat intelligence, and how we format raw data about threats.
The fact that TI is a quickly expanding field complicates matters further. With a 17,9% CAGR and a lot of new providers in the market, there’s confusion about what threat intelligence is, and the types of TI organizations need.
To shed some light on the issue, we’ll go over the most common threat intelligence types in terms of labels, IoC types, data formats and use cases.
Types of Threat Intelligence Information
There are a lot of ways to categorize threat intelligence information, and TI providers don’t always agree on the definition. For example, the data behind “Operational TI” can mean two very different things based on the provider you license it from.
A good rule of thumb for assessing the potential value-add of TI is to look at the amount of enrichment, or manual analysis performed on the raw data. With that in mind, here are three essential types of threat intelligence.
Reputation TI
Reputation threat intelligence, also called Tactical TI by some providers, is straightforward. It usually refers to IoCs extracted out of live systems, with little context, simply providing a verdict about the reputation of IP addresses, URLs, domains, file hashes, certificates and other artefacts.
It usually involves the least amount of enrichment, to facilitate real-time transmission of data and help security teams keep up with attackers.
Reputation TI is especially useful in MRTI scenarios, integrating TI data like IP blacklists with EDR/EPP products, backends, NGFWs, and similar use cases. The main benefit of reputation TI is automated real-time protection.
Since they require the least amount of human intervention, TI providers can deliver reputational TI in large quantities.
Operational TI
Operational threat intelligence refers to specific threats, like enriched and correlated data about a group of indicators, threat actors, malware families, CVEs, victimology, exploits, and any other artefacts seen working together for malicious purposes. They’re especially relevant to SOC analysts and security researchers.
Operational TI is the lifeblood of investigations, incident response, digital forensics, and similar use cases that cannot rely on just internal host data.
Compared to Reputation TI, suppliers need to use more sophisticated tooling to create and validate Operational TI, attribute IoCs to threat actors, or further process artefacts in a cybersecurity lab. While some of these tasks can be automated, especially with the help of deep learning models, the core differentiator of Operational TI is human intervention on raw data, indirectly or directly.
Let's look at an example of Operational TI. In the Bitdefender IntelliZone portal, SOC analysts can query our TI datasets for a specific threat actor they’re researching. They’ll find numerous threats there, which detail the actor’s TTPs, recent activity, target industries, and a lot more. Starting from a threat list like the one below, SOC analysts can decide to explore threats more in depth, or pivot their focus on a different industry, country, victim, or more.
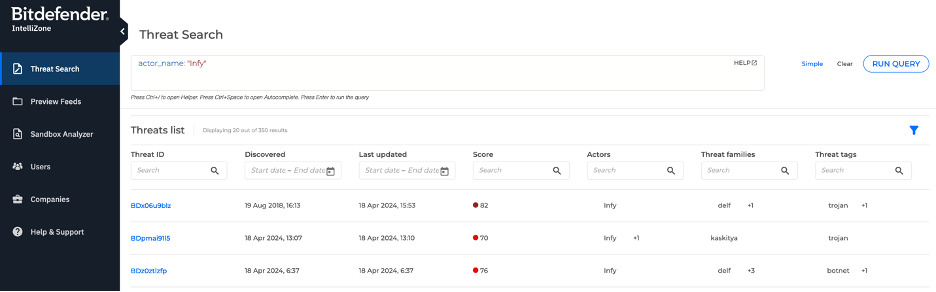
Strategic TI
Strategic threat intelligence signifies maturity in the threat intelligence market. It usually refers to high-value reports (PDFs), with manual or semi-manual input from data scientists.
Strategic TI reports usually provide a high-level analysis of trends in the cybersecurity space, with a focus on specific industries, geographic areas, or events.
These reports have a lot of use cases. For example, they can help management in making decisions on budget and focus allocation. They’re also useful to organizations that need to align their strategy to the threat landscape, like MSSPs, security service providers, defense contractors, states or any processors of valuable personal information.
Strategic TI can be further broken down into three types of reports:
- Recurrent: An analysis of actors or malware families over time. Usually with a focus on certain geographic areas or industries. Recurrent reports can be subject to some form of automation.
- Event-driven: Similar to recurrent reports, but they’re triggered by events, or a new development in the market. Examples of report triggers include wide-spread vulnerabilities or geopolitical developments.
- Bespoke: On-demand reports, typically requested by large enterprises or governments. They involve the highest costs, and most manual work.
To produce reliable threat intelligence, providers must first establish a reliable dataset of reputational and operational TI, which will be used to generate the insights of strategic TI.
Where To Get Threat Intelligence
Threat intelligence can be further broken down based on where partners can find the information they need.
Directly From Reputable Cybersecurity Providers
A threat intelligence portal is usually the interface to a single provider’s threat intelligence. The kind of data you’ll find in a threat intelligence portal depends on the licensing agreement with your provider, and their product range.
Let’s use Bitdefender as an example, which operates a TI portal called IntelliZone. It’s a one-stop shop for SOC analysts to find actionable insights on threats, threat actors, or TTPs. IntelliZone users can, for example, submit a file hash they’re investigating, and get a detailed breakdown of the threat, associated actor, and other relevant details.
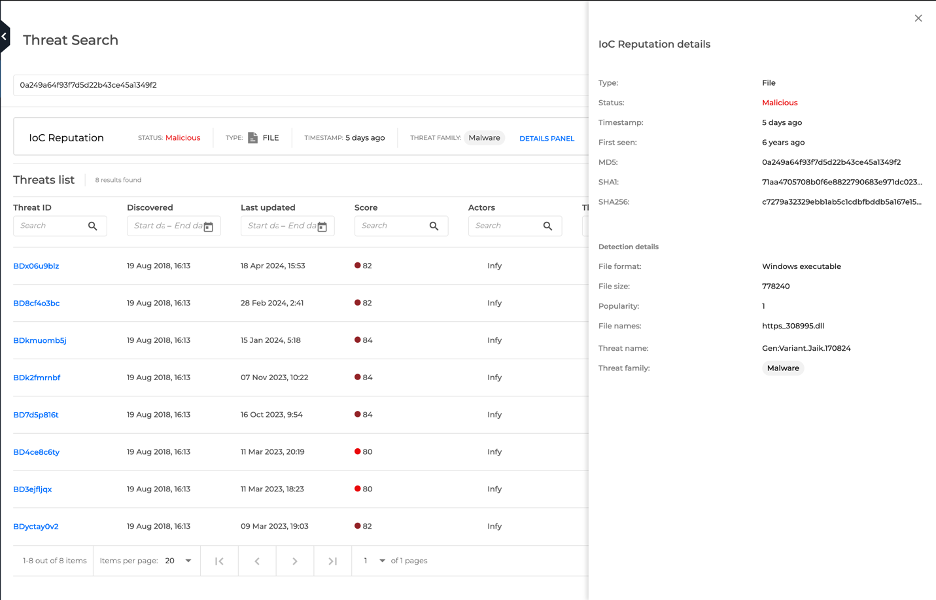
There are a few advantages to sourcing TI straight from cybersecurity providers. You get access to the largest, most detailed datasets. Plus, by using the provider’s tooling, you can stay on top of threats with real-time updates.
Threat Intelligence Platform (Third-Party)
A threat intelligence platform usually has a large marketplace that offers threat intelligence from multiple vendors. It funnels this TI to customers via a unified data model, in automated or manual ways, in a periodical manner (typically from every-6h to once-per-day). Here’s an example of feeds available to license on Anomali’s marketplace:

Most threat intelligence platforms will feature all types of TI data, including reputational, operational, and strategic TI.
Licenses for a SOAR/SIEM Platform
Companies that need threat intelligence to optimize their security operations can license feeds and queries straight from their SOAR (Security Orchestration, Automation and Response) or SIEM (Security Infrastructure Event Management) platform.
Most SOARs can collect and orchestrate threat intelligence from internal sources. While that’s a valuable feature, it’s not enough to make the most out of TI in security posturing. That’s why a lot of SOAR and SIEM providers incorporate external TI feeds into their offer.
Different Threat Intelligence Formats
The term “Threat Intelligence” encompasses a lot of different actual data, with various use cases, and even different formats for delivering information.
Data Formats & Protocols
Because TI is a quickly expanding, and relatively new field, there’s no standardized way to process threat intelligence. Providers use a variety of standards to deliver feeds and API responses, but the most common ones are STIX and MISP:
STIX (Structured Threat Information Expression) is a language and serialization format used to share threat intelligence. It outlines several standards on how to structure information about threats, threat actors or TTPs, and it’s adopted by a large part of the cyber security community.
MISP (Malware Information Sharing Platform) is an open-source project that operates a threat intelligence platform, and several standards for sharing TI. The MISP format is a simple JSON structure to facilitate sharing CTI, on the MISP platform or anywhere else.
Despite the undeniable usefulness of these formats, they have limits, and their applicability could differ between TI types. That’s why a lot of security providers develop their own data format to share intelligence.
TI Feeds vs TI APIs
As the name suggests, TI feeds refers to data streams of threat intelligence, usually delivered for MRTI scenarios. Most commonly, TI feeds will feature malicious IPs, C&C servers, URLs or domains used by attackers.
Feeds are very useful for hardening security. They can be used to extend NGFWs, expand the capabilities of an IPS, or other security hardening tasks. TI feeds are characterized by a high throughput of reliable data.
TI APIs are services that let partners query large datasets of threat intelligence as part of an investigation, incident analysis, or any other type of security research. While they have MRTI applications, TI APIs are mostly used by humans that want to analyze data manually.
All threat intelligence types (reputational, operational, strategic) can come in either feed or API format.
Find Out More
Bitdefender gathers threat intelligence from millions of sources worldwide. We centralize, vet, and package this information in various feeds and API services. You can find out more about the Bitdefender TI offer on our Advanced Threat Intelligence page.
We also operate IntelliZone, a threat intelligence portal that centralizes data from our telemetry and delivers it to SOC analysts and security researchers in a convenient UI.
tags
Author

Theodor Porutiu is a Technical Marketing Architect with a knack for writing engaging content and communicating complicated topics in simple terms. He enjoys short hikes and long gaming sessions in equal measure, and he gets really hyped about a different open-source project every week.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks







