Free Domain Provider Offers Safe Harbor for Spammers
Crooks replace co.cc and co.kr with Tokelau’s free .tk TLD in cyber-attacks.
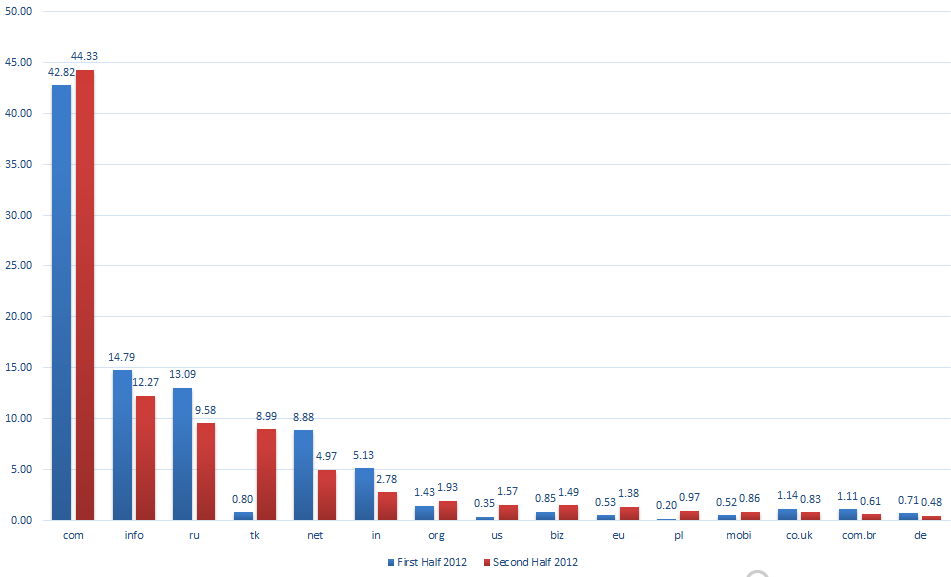
Cyber crooks have significantly abused .tk domains in attack campaigns in the second half of 2012. Compared to the first half, the number of malicious .tk domains jumped from less than 1 percent to 9 percent of all security incidents involving Top Level Domains.
The explanation for the jump is simple: In the second half, Tokelau’s Dot.TK was the only top level domain name registry that provides free domain names. An answer to the problem, though, is somewhat more complicated.
Free domain names have always posed problems for web users and security companies alike. In July 2011, sustained abuse prompted Google to delist domains registered with second-level registrars, such as the Australian co.cc and the Korean co.kr. Most antivirus companies also enforced web blockades for all domains registered with the respective registries.
The ban, and the bad publicity, made cyber-criminals lose interest in them, which explains their poor scores and drop in ranking. Co.cc ranks 16th and co.kr is was down in position 67.
Scammers register domains and create websites on top level domains where they host phishing forms and malware as part of cyber-attacks driven by spam, social media posts or instant messenger. When users click a malicious link or open an infected HTML spam attachment, they are either redirected to malicious pages, or an IFrame fetches malware from a compromised web location to infect users’ PCs.
In other attacks, crooks rely on mass-compromise of websites that run highly-popular content management software such as WordPress or Joomla. They use known exploits to subvert the hosting account and store malware, phishing pages or even information they steal via keyloggers or browser injectors.
As shown in the above chart, the .com remains the most frequently abused top level domain in malicious spam campaigns. It’s no surprise that the .com TLD is the top choice for scammers. According to VeriSign, the .com and .net TLDs experienced aggregate growth, reaching a combined total of 113.8 million domain names in the fourth quarter of 2011.
Apart from the perennial .com, .info, .ru, and .net domains, users have seen these past few months more .eu, .us, or .org URLs in messages spammed into their inboxes.
Scammers use TLDs with good reputations to give targeted victims a false sense of familiarity. The number of malicious .eu domains, for instance, has nearly tripled in recent months, exactly because crooks wanted to take advantage of the fact that for most people don’t associate .eu domains with malicious attacks and security problems.
The lifespan of these domains is usually short. Attackers need to move fast from one domain to another to evade security software blacklists or reputation-based mechanisms.
Lately, scammers have managed to hide paid domains and use them longer before they get blocked, blacklisted or receive the bad-reputation badge when they began using URL shortening servers. This apparently was behind the 15 percent drop in the number of new TLDs used in cyber-crime operations.
This article is based on the statistics provided courtesy of Adrian Miron, Bitdefender Lead Antispam Researcher.
tags
Author
A blend of product manager and journalist with a pinch of e-threat analysis, Loredana writes mostly about malware and spam. She believes that most errors happen between the keyboard and the chair.
View all postsRight now Top posts
Torrents with Pirated TV Shows Used to Push Lumma Stealer Malware
November 14, 2024
What Key Cyberthreats Do Small Businesses Face?
September 06, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









