US Offers $10 Million Bounty for Chinese Hacker Responsible for 2020 Firewall Hacks

The US Department of State’s Rewards for Justice (RFJ) program is offering up to $10 million for information pinpointing a Chinese national for his role in the April 2020 compromise of tens of thousands of firewalls worldwide.
In 2020, a Ragnarok ransomware campaign exploited a zero-day SQL injection vulnerability in Sophos XG firewalls.
The US State Department is now shedding more light on the events and, importantly, who was involved.
A state-sponsored action
In 2020, Guan Tianfeng and other employees of the Chinese cybersecurity company Sichuan Silence developed and tested intrusion techniques before deploying malicious software that allowed them to exploit a zero-day vulnerability in certain firewall sold by UK-based cybersecurity firm Sophos Ltd, according to an indictment unsealed this week by the US Department of Justice.
Sichuan Silence is a Chengdu-based cybersecurity government contractor whose clients are mainly state actors, including intelligence services. The firm is known to offer “services” like computer network exploitation, email monitoring, brute-force password cracking, and public sentiment suppression, as well as equipment designed to probe and exploit target network routers.
Guan had discovered a zero-day exploit, which his employer used to deploy malware to 81,000 firewalls owned by thousands of businesses worldwide.
“More than 23,000 of the compromised firewalls were in the United States,” according to the DOJ. “Of these firewalls, 36 were protecting U.S. critical infrastructure companies’ systems.”
The intent was to steal data and credentials (usernames and passwords) in a sustained effort to compromise target entities.
Guan also devised a mechanism to infect victims’ systems with ransomware if they tried to remedy the compromise. The ransomware would be automatically deployed, encrypting data on the victim’s end, rendering it unusable and putting adversaries in a position to demand a ransom in exchange for the decryption key.
Lives at risk
The potential impact of the ransomware attack could have resulted in serious injury or the loss of human life, the DOJ notes.
“One victim was a U.S. energy company that was actively involved in drilling operations at the time of the compromise,” according to the press release. “If this compromise had not been detected, and the ransomware attack not been thwarted, it could have caused oil rigs to malfunction potentially causing a significant loss in human life.”
The Department of the Treasury’s Office of Foreign Assets Control (OFAC) is sanctioning Sichuan Silence and Guan Tianfeng, both based in People’s Republic of China, for their roles in the April 2020 compromise of tens of thousands of firewalls worldwide.
Reward up to $10 million for information on Guan
The US State Department is offering a reward of up to $10 million for information leading to the identification or location of the Chinese hacker.
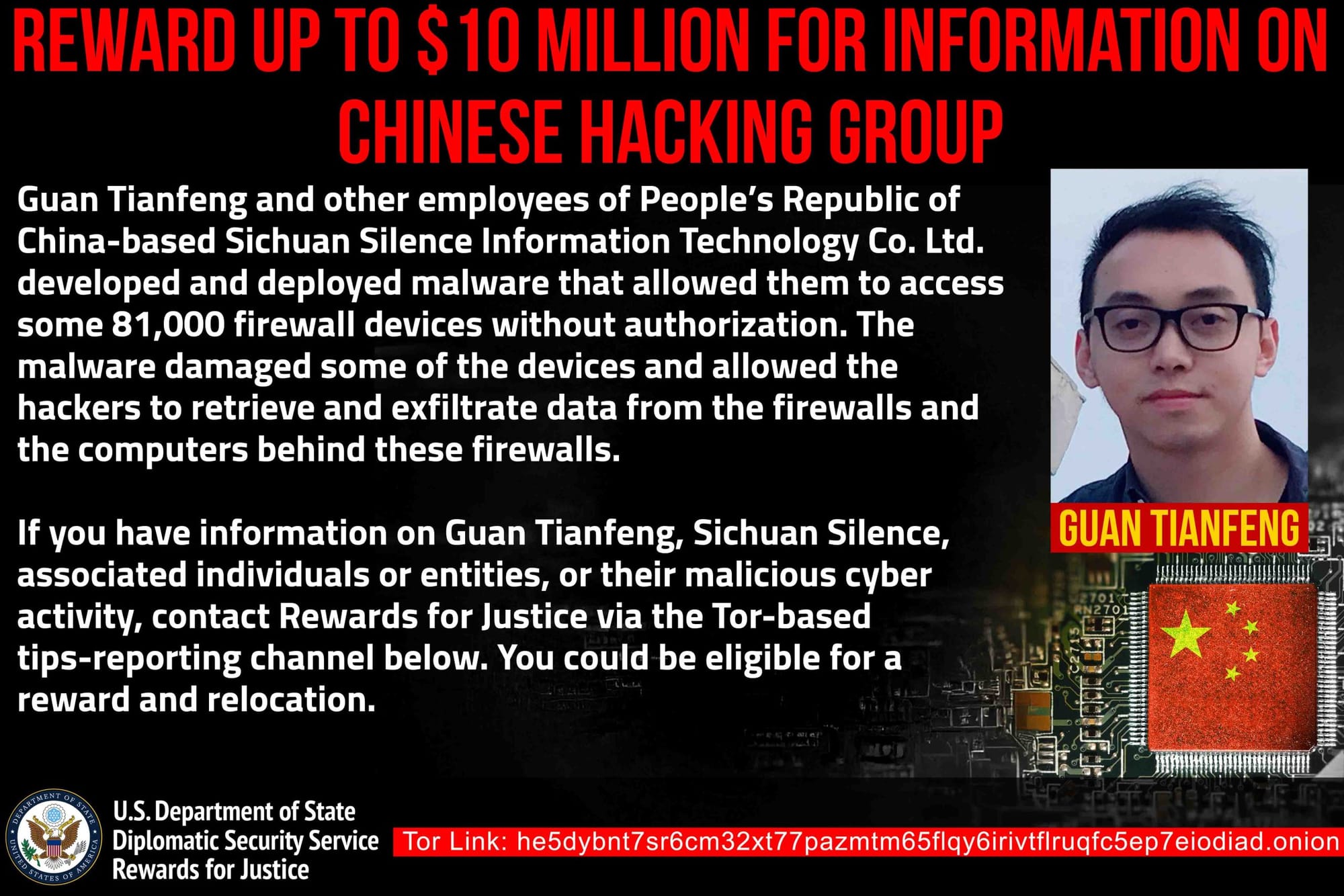
Anyone with information on Guan, his employers, associated individuals or entities, is encouraged to contact Rewards for Justice via its Tor-based tips-reporting channel.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








