Don't let hackers ruin your roast! Security flaws found in AGA cooker app

Imagine you work in marketing for a company that has been manufacturing upmarket cookers for almost 100 years.
How do you make your product capture people’s attention and attract new customers?
Simple – you rejuvenate your traditional product with state-of-the-art touch control panels and give owners a smartphone app that allows them to control their AGA cooker remotely.
https://www.youtube.com/watch?v=JDmgLwX587I
You’ve probably guessed where we’re heading…
Security researchers at Pen Test Partners discovered it was easy for a malicious hacker to send commands to owners’ AGA cookers, without authorisation.
AGA’s Total Control mobile app makes no attempt to encrypt its communications, send messages over plaintext HTTP – making it trivial for an attacker to intercept and modify commands.
The app sends its commands to a website which – oddly – send an SMS message to control your AGA cooker. Quite why the AGA cooker doesn’t connect to your home Wi-Fi network seems rather odd, but hey ho… clearly whoever developed the service decided requiring customers to spend money on an additional mobile phone contract specifically for their oven made more sense.
What it does, perhaps, tell me however is that whoever developed these remote controlled AGA cookers wasn’t fully entrenched in how modern technology is integrated with the internet these days.
And that feeling is underlined when one examines the AGA Total Control website – delivered again over HTTP rather than HTTPS, opening opportunities for a malicious hacker to steal information in transit.
Pen Test Partners discovered that when you attempt to create an account on the AGA site it asks you for your AGA cooker’s mobile phone number. Fair enough – but if you enter a phone number that has already been registered, it informs you of the fact.
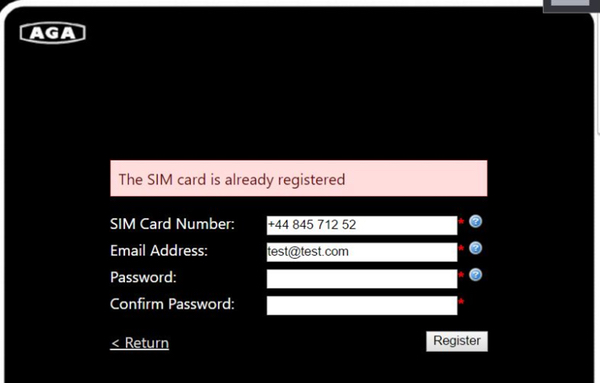
Why is that a problem? Well, it’s now child’s play for a malicious attacker to enumerate a list of all the valid AGA cooker phone numbers. And that means that they could also turn other people’s AGA cookers off by simply sending a text message – potentially ruining your Sunday dinner.
To be fair, it’s not the most serious security hole ever found in a device which has attempted to drag itself into the 21st century by adding high-tech features, but it does show yet again that manufacturers are racing to add bells-and-whistles to their products without taking online safety seriously.
AGA cookers may not be that critical, but imagine if the same weak infrastructure was being used by medical devices, or other control systems…
What’s more, in its blog post, Pen Test Partners share a sorry tale of just how difficult it was to report to AGA details of the vulnerabilities that had been uncovered.
For weeks the researchers attempted via various routes to get a response from AGA, only to have messages and calls unanswered, promises of return calls broken, and even being blocked by AGA’s official Twitter account at one point!
There’s no excuse these days for any firm with an online presence not to have some mechanism for escalating security concerns to the right people inside the company so they can be responded to appropriately and promptly.
Anything less just looks half-baked.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








