Flaw found in stalkerware apps, exposing millions of people. Here's how to find out if your phone is being spied upon

A serious security vulnerability has been found in popular stalkerware apps, exposing the sensitive personal information and communications of millions of people.
Stalkerware is a type of spyware, frequently used to spy on every message sent or received by a romantic partner, learn who they are speaking to on their phone, learn their location, or view the photos they have taken.
Although stalkerware is frequently marketed as a way to track your children's or employees' behaviour online, or to keep your family safe, the reality is that it is often jealous partners or those with unhealthy interest in an individual who end up purchasing such apps and installing them on their target's devices.
It has frequently been the case that victims of domestic abuse are the targets of stalkerware, which often attempts to hide its presence on a compromised smartphone.
So it's very understandable that interest would be piqued when a security researcher unearthed a security vulnerability present in the Cocospy and Spyic phone-monitoring apps.
As TechCrunch reports, the flaw has leaked the email addresses of people who signed-up for Cocospy or Spyic, with the intention of planting the app on another person's device covertly.
According to the anonymous researcher, Cocospy is one of the largest known stalkerware operations in the world, with almost 1.8 million registered users. Spyic, which shares its IT infrastructure with Cocospy, has 875,000 registered users.
Both apps have been linked to a Chinese mobile app developer, who has so far remained silent about the security hole and at the time of writing have not resolved the issue.
It's hard to feel too much sympathy for the purchasers of stalkerware who have had their details leaked in this way. Most of our attention should probably be directed towards those innocent individuals who do not know that their devices are being spied upon.
And it's with them in mind that it's refreshing to share with them a simple way to tell if Cocospy or Spyic have been installed on their Android devices.
As TechCrunch describes, entering the Android phone app, typing ✱✱001✱✱ on the keypad, and then presssing the "call" button will make the stalkerware apps appear on-screen if they are installed.
This functionality was built into the stalkerware to allow the person who planted the apps to regain access on their victim's devices - but can also be used by the victim to determine if the spyware has been installed.
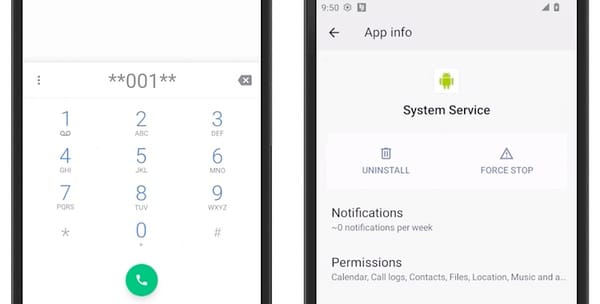
Both Cocospy and Spyic disguise themselves as a generic-looking app called “System Service.”
If you are concerned about stalkerware, be sure to read the EFF guide to surveillance self-defence.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








