Hackers exploit little-known WordPress MU-plugins feature to hide malware

A new security issue is putting WordPress-powered websites at risk. Hackers are abusing the “Must-Use” plugins (MU-plugins) feature to hide malicious code and maintain long-term access on hacked websites.
In earlier 2025, security researchers at Sucuri noticed cybercriminals using the tactic, and they say that it has been increasingly used the technique in the months since.
In WordPress, MU-plugins are plugins that are automatically enabled on a WordPress-powered site and - as the description suggests - must be used, and therefore can not be deactivated through the WordPress admin interface.
These "must-use plugins" are located in a specific directory called, imaginatively enough, mu-plugins within the wp-content folder. Unlike regular WordPress plugins, they may not be listed alongside regular plugins unless the "must use" filter is selected.
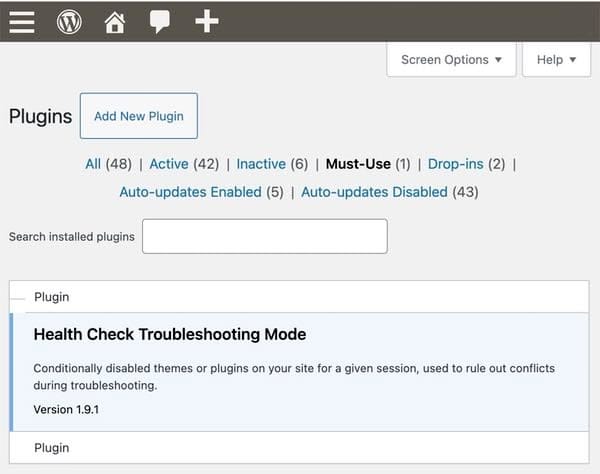
What makes a plugin "must-use"? Well, any plugin that is essential for the site's functionality and should not be turned off. This may include security enhancements, performance optimisation, or multi-site management features that a site's developers or administrators have deemed critical to remain active.
So there is a good legitimate reason for a WordPress site to have "must-use" plugins, although many WordPress users may be largely oblivious to their existence.
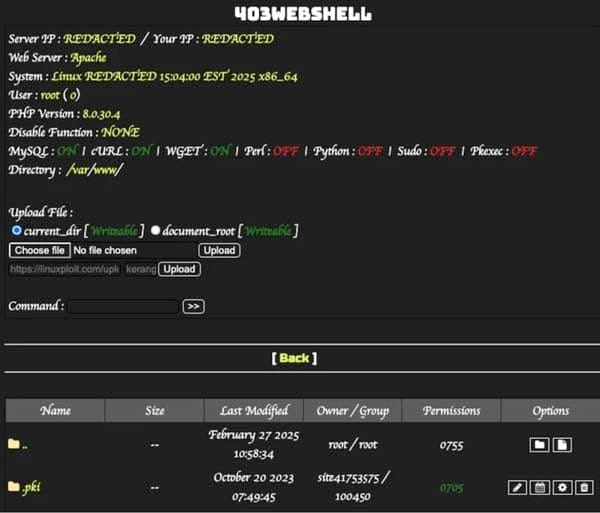
According to researchers, an attack typically begins when hackers compromise a website (often via an out-of-date WordPress plugin, or weak password). Once an attacker has gained access, they will plant a malicious PHP file into the mu-plugins folder, effectively giving it a persistent foothold on the website.
Sucuri's team say they have seen three malicious MU-plugins being deployed in in-the-wild attacks:
- redirect.php – Sends website visitors to a bogus browser update page that downloads malware.
- index.php – A backdoor which grants attackers remote access to the compromised server.
- custom-js-loader.php – Replaces website content with spam links or explicit images.
These hidden mu-plugins run the hackers' code on every page of the website, and can reinfect an entire site if great care is not taken to remove an infection.
In an attempt to avoid detection too soon, the redirect plugin code avoids activating if it is viewed by one of the website's own logged-in administrators or a search engine bot.
Of course, nobody wants a hacker having a backdoor to their website - granting an unauthorised party admin-level control. A malicious attacker with such power can steal data, create new admin accounts, or use your website to spread malware.
Furthermore, you may find any traffic coming to your site is redirected by the malicious mu-plugins planted by the cybercriminals elsewhere on the internet, doing harm to your business and your brand.
And it's bad news for your website's visitors too. Anyone visiting an infected site is putting their computer at risk of potential malware infection.
The best advice is to harden your WordPress site, by ensuring that you use strong, unique passwords and have enabled two-factor authentication.
Furthermore, monitor your site for unusual behaviour, and ensure that are keeping WordPress and any legitimate plugins and themes your website uses properly updated.
Finally, if you suspect your WordPress-powered website could be hosting malicious MU-plugins, look in the wp-content/mu-plugins folder. If you don't use MU-plugins it should be empty.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks