Hackers could install malware on your Amazon Echo to secretly 'wiretap' you

Security researchers have discovered that the Amazon Echo is vulnerable to attacks that could allow a hacker to install malware capable of secretly spying on the device’s microphone to hear what is being said in its vicinity.
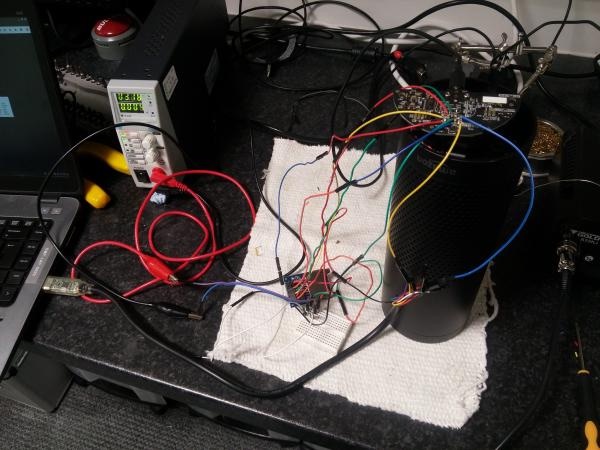
In a technical blog post, researchers at MWR have described how they were able to exploit hardware design choices in the 2015 and 2016 editions of Amazon’s Echo home assistant to turn it into a covert listening device.
Conveniently for any attacker attempting to spy on a target without their permission, the attack does not affect the Amazon Echo’s overall functionality – meaning that to the victim the device will appear to be working sas normal.
Less conveniently for any wannabe snoop, the attack requires physical access to the device: the rubber base of the Amazon Echo must be removed tio expose debug pads, allowing the device to be booted from an external SD card.
If an attacker manages to gain access to an Amazon Echo of interest they can directly boot into the device’s firmware from an external SD card, gain remote root shell access and install malware that remotely snoops on the ‘always listening’ microphones.
Your first defence, of course, is that this attack is only possible through physical access to the device. An Amazon Echo in your home is less likely to be targeted by a hacker than an Amazon Echo in a public area or shared space.
With some hotels equipping all their hotel rooms with their very own Amazon Echo, it’s clear that the privacy concerns are not merely theoretical.
And even home owners may be at risk too, as it’s conceivable that a jealous partner might implant malware on your Amazon Echo to keep tabs on you after you have kicked them out of your life. It would also perhaps to be wise to consider that there is also a risk if you purchase a second-hand Amazon Echo.
There is some good news for concerned Amazon Echo users. According to the researchers, the vulnerability has been confirmed on the 2015 and 2016 edition of the Amazon Echo, but is not present on the 2017 edition. A change implemented by Amazon in the latest edition of its Echo device has effectively prevented external booting.
According to researchers, you can easily verify if your Amazon Echo device is protected against the vulnerability by examining the device’s model number and copyright message (if you’re lucky you’ll see a device model number ending in 02).
Furthermore, the Amazon Echo does come with a physical “mute” button that disables the microphone, and cannot be subverted by changes to the software. However, one has to wonder how frequently the typical Amazon Echo user makes use of such functionality.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








