Hive ransomware has extorted $100 million in 18 months, FBI warns

$100 million in just the last 18 months.
That's the amount of money that the Hive ransomware is thought to have extorted from over 1300 companies around the world, according to a joint warning issued by the FBI, the Cybersecurity and Infrastructure Security Agency (CISA), and Department of Health and Human Services (HHS).
First seen in mid 2021, Hive is a ransomware-as-a-service (RaaS) operation, which different cybercriminals have used in attacks launched against healthcare institutions, non-profit organisations, energy providers, and retailers, amongst other sectors.
And it is this targeting of critical infrastructure and hospitals which led the HHS earlier this year to describe Hive as an "exceptionally aggressive" threat to the health sector.
Attackers deploying the Hive ransomware have often gained initial access to victims' networks via the use of phishing emails with malicious attachments, stolen single-factor RDP logins, virtual private networks and other remote network connection protocols.
According to the FBI warning, attackers have also sometimes managed to bypass multi-factor authentication and gained access to FortiOS servers by exploiting a known vulnerability.
Like many other ransomware attacks, Hive has adopted a "double extortion" model where data is exfiltrated from a victim's network before it is encrypted. The stolen data is leaked on a dedicated website on the dark web if the ransom is not paid.
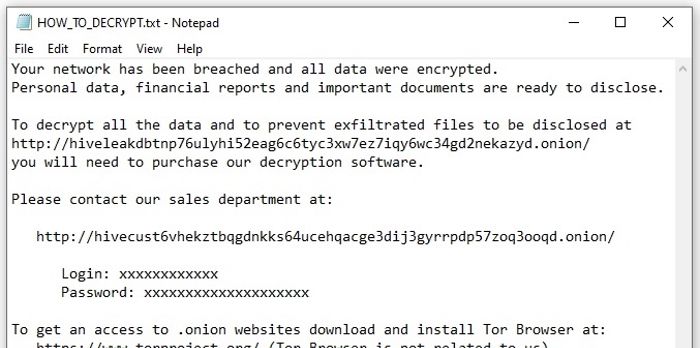
Some victims of Hive have even reported receiving phone calls from cybercriminals pressuring them to pay up and engage in negotiations.
Hive victims are told in a ransom note left after data has been encrypted not to report the attack to the police or FBI, or to bring in specialist recovery companies to try to decrypt data or manage negotiations with the gang.
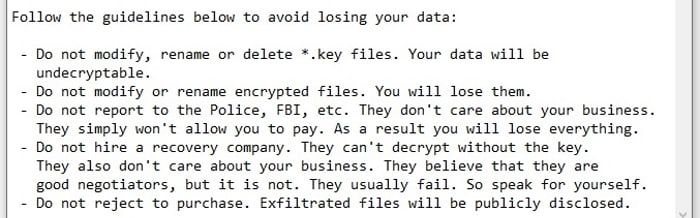
The FBI continues to urge organisations to report ransomware attacks as it helps investigators gather information about the perpetrators and might one day lead to those responsible being brought to justice.
As usual, the FBI does not recommend that ransoms are paid by victims. However, in its advisory it notes that "Hive actors have been known to reinfect — with either Hive ransomware or another ransomware variant — the networks of victim organizations who have restored their network without making a ransom payment."
The FBI urges companies to report ransomware incidents to the local field office to help investigators with critical information to track the attackers, "hold them accountable under US law, and prevent future attacks."
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








