How to Protect Against "WannaCry" Ransomware
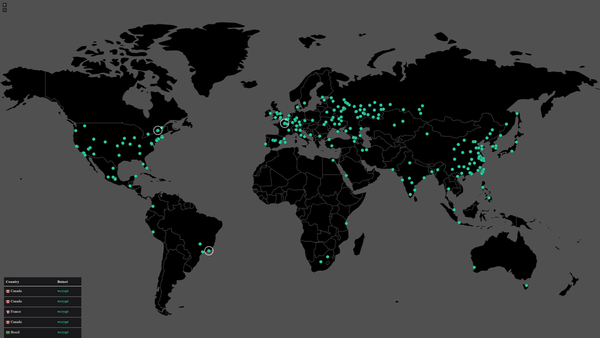
A ransomware attack hitting more than 200,000 endpoints across 150 countries over the past weekend is expected to return with double the force on Monday, experts say. Here”s everything you need to know about the WannaCry ransomware and – more importantly – how to protect against it.
Rundown
- Ransomware is a type of malware that encrypts user data and demands a ransom, usually in the form of electronic currency, to decrypt the files
- WannaCry – also dubbed Wanna Decrypter 2.0, WCry, WanaCrypt and WanaCrypt0r – exploits a Windows Server Message Block (SMB) flaw that Microsoft patched almost two months ago (MS17-010 security bulletin)
- The flaw was originally discovered by the US National Security Agency
- The hackers stole this vulnerability from the NSA and released it in the wild for others to use and deploy their ransomware attacks
- Microsoft issued two consecutive patches for the malware, one in March, and another one on Friday
- As many as 200,000 computers got infected in 3 days after users failed to install the critical patches
- The malware spreads across networks with the help of a bundled worm, making it the world”s most dangerous piece of ransomware written to date; it is also the first of its kind – i.e. it leverages a wormable exploit to spread automatically
- The ransom is $300 worth of bitcoins for decrypting and restoring access to your files (ransomware attackers prefer the electronic currency as it is untraceable)
- The malware threatens to delete your files within seven days if no payment is made
- It hit several organizations across the globe, including FedEx, Telefónica, and the UK”s National Health Service (NHS)
- So far few payments have been made to the hackers, but a BBC analysis has revealed that the authors have likely amassed around $38,000 in payments
- A security researcher who wished to remain anonymous became an “accidental hero” after halting the spread of the malware by registering a domain name to track it
- The researcher warned that Monday would most likely bring a new wave of attacks, this time priced higher than $300
- Microsoft responded to news of the attack saying this should act as a wake-up call for governments storing important data on vulnerable systems, leaving the door open to hackers
- The technology giant said the attack was like allowing someone to break into the US Military and “steal Tomahawks”
- Europol chief Rob Wainwright said the attack had been reported in 150 countries, calling it “unprecedented in scale”
- Wainwright has said the Europol is working with the FBI to find those responsible but that people should brace themselves for another potential attack on Monday
How to patch Windows XP, Windows 8 and Windows Server 2003
Following Friday”s attack, Microsoft issued the following statement.
We know some of our customers are running versions of Windows that no longer receive mainstream support. That means those customers will not have received the Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download here.
How to patch Windows 10
Simply apply your latest system updates. Go to Settings -> Update & Security -> Windows Update -> Check for updates and install the latest updates for your Windows 10 machine.
Because WannaCry exploits a remote code execution (RCE) flaw, hackers can take control of machines without having the user click on a malicious file, as it is usually the case. This means the only way to prevent the attack is to have your system up to date, or to use an anti-malware solution.
Bitdefender customers are not affected by this new family of ransomware. Bitdefender customers (regular and business users alike) are pro-actively protected against WannaCry through machine learning and memory introspection. Learn more here.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








