IoT Attack Surface: Where are the Weak Links?

IoT households are generally deemed more exposed to digital threats due to the large number of internet-connected devices, but some devices are more prone to attacks than others.
Internet devices used as entry points in cyber attacks
It’s no longer a secret that threat actors exploit anything they can to breach networks and accomplish their malicious goals, and internet-connected devices are their primary target.
An unsecured printer, for instance, could let a threat actor access its printing queue and steal potentially sensitive information.
However, IoT households generally have more than just a printer connected to the internet, thus offering cybercriminals a broader range of devices they could try to exploit.
Most vulnerable devices in 2024
Consumers usually expect the most commonly used devices to be the most vulnerable. For instance, a laptop or a smartphone is considered more prone to cyberattacks than a smart plug, mainly because they involve frequent human interactions.
Both smartphones and laptops are considered active devices, rather than passive ones, such as smart plugs, which you typically configure once and forget about.
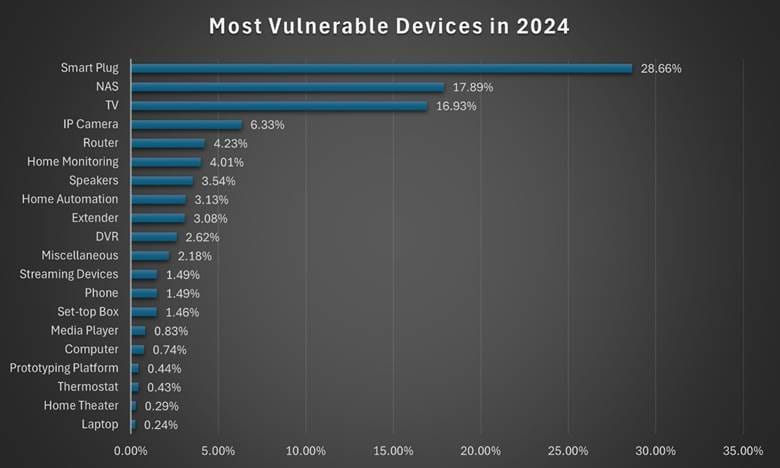
A glance at our analysis of the most vulnerable device types in 2024 reveals a reality that will surprise many.
The most vulnerable internet-connected devices in 2024 are as follows:
|
Smart Plug |
28.66% |
|
NAS |
17.89% |
|
TV |
16.93% |
|
IP Camera |
6.33% |
|
Router |
4.23% |
|
Home
Monitoring |
4.01% |
|
Speakers |
3.54% |
|
Home
Automation |
3.13% |
|
Extender |
3.08% |
|
DVR |
2.62% |
|
Miscellaneous |
2.18% |
|
Streaming
Devices |
1.49% |
|
Phone |
1.49% |
|
Set-top Box |
1.46% |
|
Media Player |
0.83% |
|
Computer |
0.74% |
|
Prototyping
Platform |
0.44% |
|
Thermostat |
0.43% |
|
Home Theater |
0.29% |
|
Laptop |
0.24% |
Unpublished internal data on IoT vulnerabilities
Our internal research from 2024 uncovers a striking distribution of vulnerabilities spanning devices, from everyday gadgets like smart plugs and TVs to more specific equipment like Network-Attached Storage (NAS) devices and home automation hubs.
Although the results may seem surprising, our dataset aims to shine a light on what threat actors mainly focus on and where consumers may underestimate the risks.
Smart plugs (28.66%)
Leading the list with a significant 28.66%, smart plugs stand out as the most frequently compromised devices in our data sample. Often found at low prices and produced by a plethora of both well-reputed and no-name manufacturers, smart plugs are inconsistent regarding security standards.
Consumers typically configure these devices through a mobile companion app. However, inadequate encryption, default credentials, and missing or infrequent firmware updates expose them to cyber attacks.
Last but not least, smart plugs communicate with other connected home systems, including automation routines, hubs, and voice assistants, so threat actors use them as pivot points to move laterally in a home network.
Network-Attached Storage (NAS) devices (17.89%)
NAS devices are the second most vulnerable type of devices, at 17.89%. These network storage devices are essentially mini servers often used to centralize backups, documents, and photos.
Compromising them grants threat actors access to personal data, financial records, or even troves of sensitive information.
NAS devices are generally kept online 24/7 for remote access and convenience, so it makes sense that threat actors with a foothold in them could wreak havoc on a home network. Dedicated firewalls and multi-factor authentication can help mitigate these risks.
Smart TVs (16.93%)
Internet-connected TVs (smart TVs) closely follow NAS devices, with 16.93%. The booming interest for internet-connected televisions, ranging from high-end 4K or 8K models to budget-friendly streaming sets, has led to an increase in proprietary operating systems.
Many users either ignore or don’t know how to install manufacturer-issued firmware updates for their TV, exposing their devices to cyber threats. Compromised TVs can leak personal data, such as viewing stats, streaming services login credentials, or even voice recordings if the TV boasts voice-assistant features.
However, the real danger is that threat actors can use the TV as a pivot to more critical systems if they breach the network.
IP cameras (6.33%)
Although 6.33% may seem lower relative to the top three categories of vulnerable devices, IP cameras still pose significant risks due to the sensitive nature of video streams.
Hacked cameras can give threat actors real-time surveillance from inside or around your home. Considering that older models of IP cameras lack encryption and come with either easy-to-guess or publicly available default passwords that owners never change, they can quickly become a liability.
Routers (4.23%)
Despite their seemingly modest 4.23%, routers are arguably the most critical gateway to your home network. Considering that they act as liaisons between the internet and every device in your home, from computers and phones to IoT gadgets like baby monitors and doorbells, their significance is not to be underestimated.
Outdated firmware, a lack of robust admin passwords, and insecure default configurations can all lead to devastating attacks.
Routers are typically deemed long-haul devices -- consumers seldomly replace or update them unless they have to.
Their relatively stagnant nature makes them attractive long-term targets for criminals who weaponize them to drop malicious payloads, move laterally on compromised networks, or conduct extensive reconnaissance.
Home monitoring systems (4.01%)
Often found as a combination of cameras, motion detectors and miscellaneous sensors, home monitoring systems (4.01%) are another valuable target for threat actors.
Like their simpler counterparts (i.e., IP cameras), home monitoring systems usually collect real-time data about the whereabouts of a household’s inhabitants.
An infiltrated perpetrator could track homeowner behavior or even disable alarms. Setting strong, unique passwords and regularly checking for and installing firmware updates are essential for mitigating risks associated with these devices.
Smart speakers (3.54%) and home automation hubs (3.13%)
Smart speakers (3.54%) are increasingly popular, mainly thanks to their assistant features. They can typically interact with a broad range of frequently used online services and apps, and many can even control IoT devices in your household.
However, their convenience makes them attractive to attackers, who may weaponize them to record private conversations, trigger actions on connected devices, or cause further damage to your network.
Home automation hubs (3.13%), used to orchestrate various IoT devices in your household, are another potential target, as a vulnerability could let attackers control or monitor all connected systems.
Wi-Fi extenders (3.08%) and DVRs (2.62%)
Although they help broaden network coverage, Wi-Fi extenders (3.08%) can also inadvertently extend the potential attack surface, especially if they lack proper security protocols (e.g., WPA3).
Digital Video Recorders (DVRs), although more old-school, still account for a significant 2.62% of the vulnerable device list because they connect to security cameras or streaming devices and handle recorded data.
Both Wi-Fi extenders and DVRs can be used as entry points into the rest of the network.
Miscellaneous and lower-percentage devices
The remaining categories consist of lower-percentage devices, including:
- Miscellaneous - 2.18%
- Streaming devices - 1.49%
- Phones - 1.49%
- Set-top boxes - 1.46%
- Media players - 0.83%
- Computers - 0.74%
- Prototyping platforms - 0.44%
- Thermostats - 0.43%
- Home theaters - 0.29%
- Laptops - 0.24%
Although these categories collectively represent a smaller share of vulnerabilities in our dataset, it doesn’t mean they are secure or less prone to attack.
Instead, it shows that consumers update and secure their phones, laptops, computers, and other devices on the list more frequently and efficiently or that the software ecosystems on these devices enforce more robust security controls.
While devices like prototyping platforms, home theaters and thermostats account for an almost insignificant share, a breach impacting them can still compromise personal data or let criminals control IoT home ecosystems.
Conclusion
Our internal research highlights that any internet-connected device could be a weak link. The prevalence of smart plugs, NAS devices and smart TVs at the top of our list suggests that attackers tend to gravitate toward high-volume or high-value targets.
However, maintaining strong and unique passwords, regularly updating firmware, installing security patches, segmenting the home network, using dedicated security software and staying informed can help homeowners mitigate these risks.
Frequently Asked Questions about IoT attack surface
· What is an IoT (Internet of Things) attack?
An IoT (Internet of Things) attack is a type of cyberattack in which a threat actor gains access to an IoT component and can put the whole network at risk.
· What is the attack surface of an IoT?
The attack surface of an IoT is the number of all possible access points and attack vectors that perpetrators can exploit to breach a network and compromise its integrity.
· What are the attacks to IoT?
Some of the most common examples of IoT attacks include dropping malicious payloads, credential theft, device takeover, man-in-the-middle (MiTM) attacks, and distributed denial-of-service (DDoS) attacks.
tags
Author

Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks