Netflix Suspended Account Scam Active in 23 Countries – How to Stay Safe

A phishing campaign deployed on a global scale is trying to trick people into believing they haven't paid their Netflix subscription. Don't fall for it – it's a scam. Criminals are trying to steal your Netflix credentials and credit card information at the same time.
Netflix is by far the largest streaming platform on the planet, making it ideal to use in attacks. Phishing schemes aimed at consumers are not usually targeted, with criminals spraying the market at random, hoping to catch at least a few victims.
However, when it's a service as large as Netflix, the chances of getting to a consumer with a streaming subscription are much more substantial.
Attackers have two ways to persuade people to open the link and become victims: the carrot and the stick. The first method is to promise people a prize or something to gain. The second is to create a sense of urgency that requires immediate action. Losing access to Netflix because of a missed payment might fit the definition of an emergency for a lot of people.
You failed your Netflix payment, give us the username and password
Leaving aside the fact that Netflix doesn't contact its customers via SMS, if there's one thing that companies won't do is tell their customers to give them a link and ask them to authenticate.
Even if a real company is advising people to access the account in a real message, it's much better for online safety to manually input the address in a browser instead of following links contained in the message.
There's a good chance users will quickly recognize that something is wrong with the SMS message, but not everyone will be careful. And the fear of losing the account can be greater than the required reasoning.
These SMS scare campaigns targeting Netflix customers have become ubiquitous and never stop, but they vary in size and scope. One very large such campaign started in September and is still active in many regions, not to mention that it spans 23 countries. Some of the most affected countries include Germany and Spain, but the United States is on that list, along with France, Greece, Portugal, Australia, and many others.
Netflix scam – what to look for?
Even though the campaign is spread across so many countries, the SMS messages are very similar to one another. In most cases, only the language sets them apart.
Here are some examples:
"NETFLIX : There was an issue processing your payment. To keek your services active, please sign in and confirm your details at : https://account-details[.]com"
"There was a failure in your recent payment, affecting your ongoing services. Check the details at 78hex4w[.]vitilme[.]info"
“NETFLIX: Su ultimo pago ha sido rechazado, su cuenta sera suspendida el 01/11/2024. Renueva tu pago en : https://renueva-netflix[.]info”
“NETFLlX : Letzte Warnung vor der Sperrung Ihres Kontos. Bitte aktuaIisieren Sie Ihre ZahIungsinformationen hier : https://homepage-nflix[.]com.”
In some instances, the links look like official ones, using the Netflix name to give it more credence. You may also notice some messages have grammatical errors, but that shouldn't be taken as the only way to see that something is wrong. Spotting these problems is helpful, but some messages are written perfectly.
Netflix scammers – what do they want?
The answer is simple, at least for this particular campaign. They want the customers' login credentials, personal information, and credit card details. The phishing websites are built specifically for this purpose.
A big security problem is that Netflix doesn't have 2FA (two-factor authentication) and only relies on usernames and passwords. This means that Netflix customers are very exposed to account takeover attacks via credential stuffing.
Here's what to expect if you open one of these links by mistake:
Funnily enough, they first want to see if you're a robot. This is likely done to give potential victims a false sense of security and to reinforce the impression that they are visiting an official website.
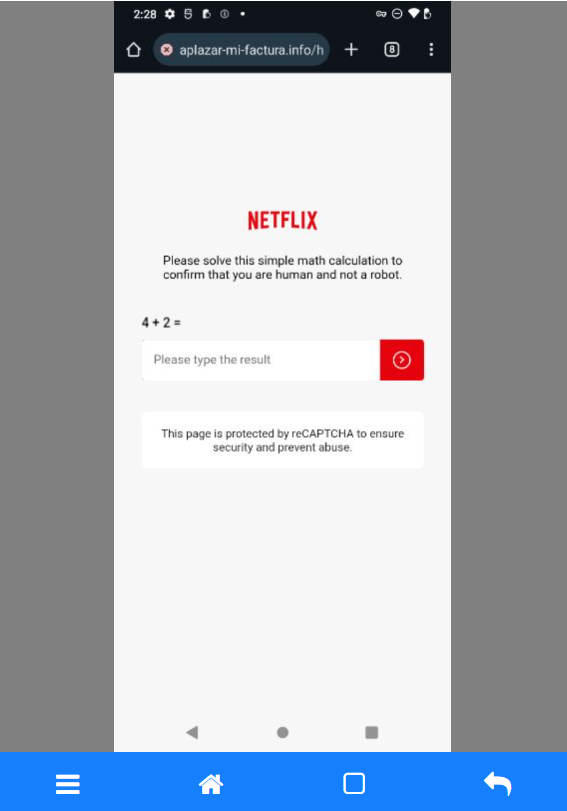
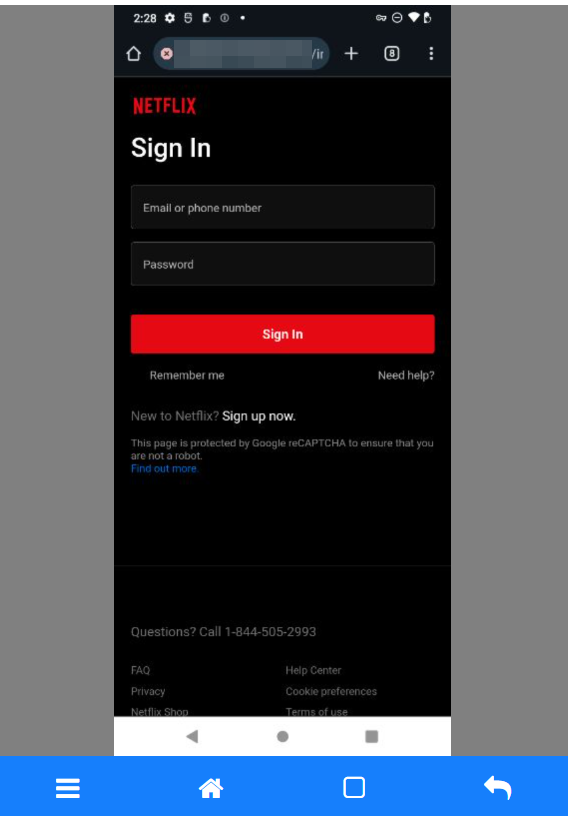
The next step is to collect credentials from Netflix customers. As soon as the user inputs those credentials, the attackers have them.
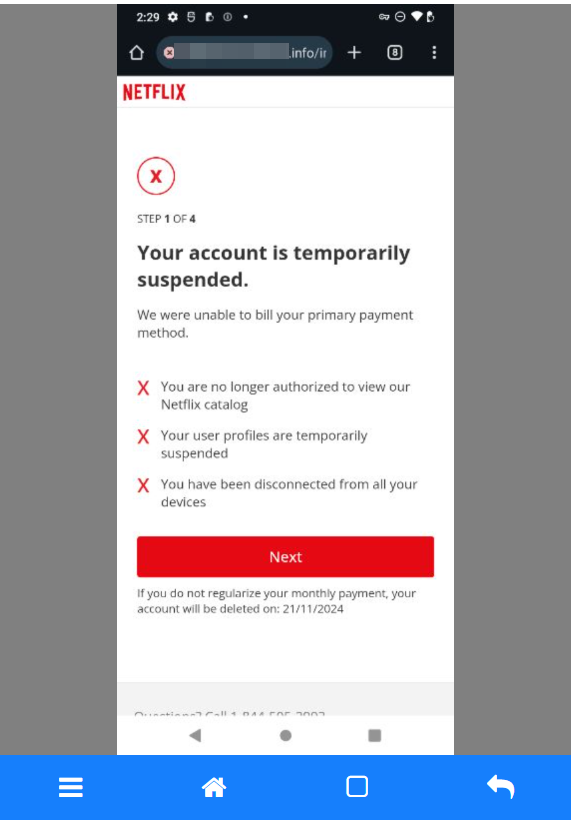
Of course, the reason for the warning SMS is confirmed in the next step. No one wants to find out that the Netflix account has been suspended or that you have been disconnected from all devices.
Let the private and financial data gathering begin. Following the same theme, the attackers will ask for personal details before requesting the credit card information.
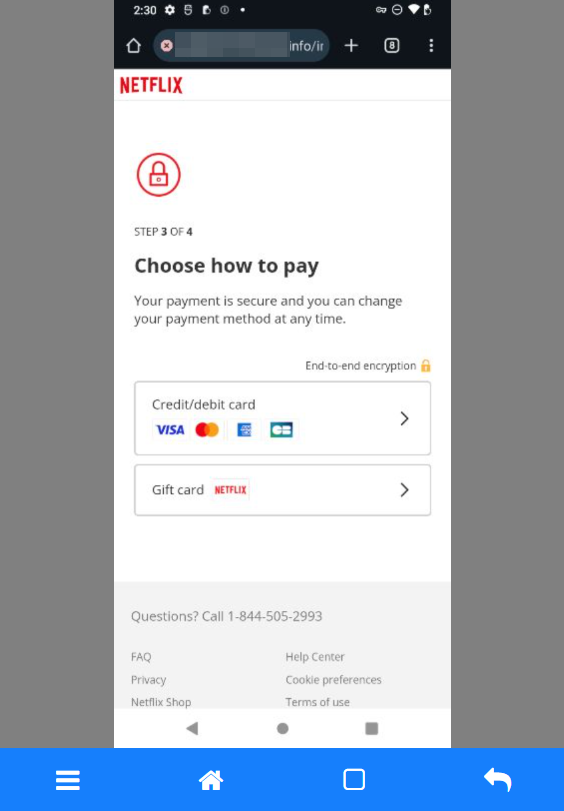
There's even the option to pay via a Gift Card instead of a credit card, which is just as good. Netflix does offer the option to purchase gift cards, but it's worth noting that they're not available in every region.
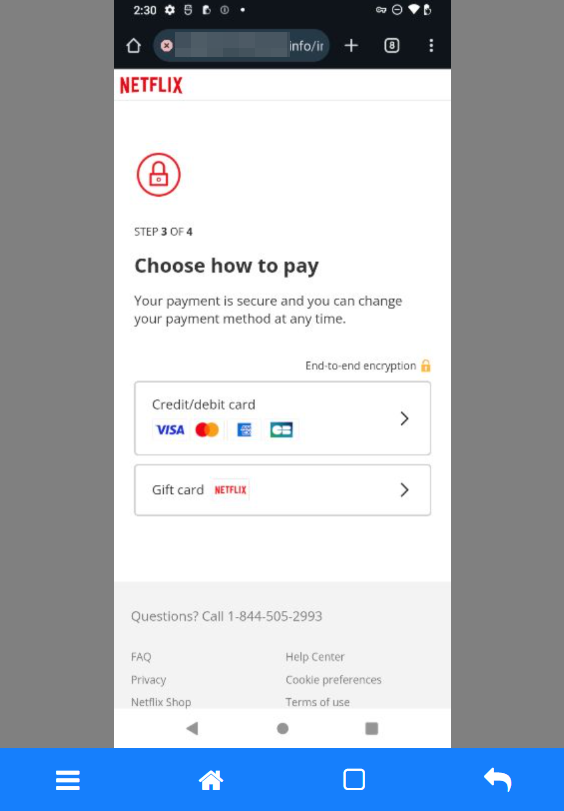
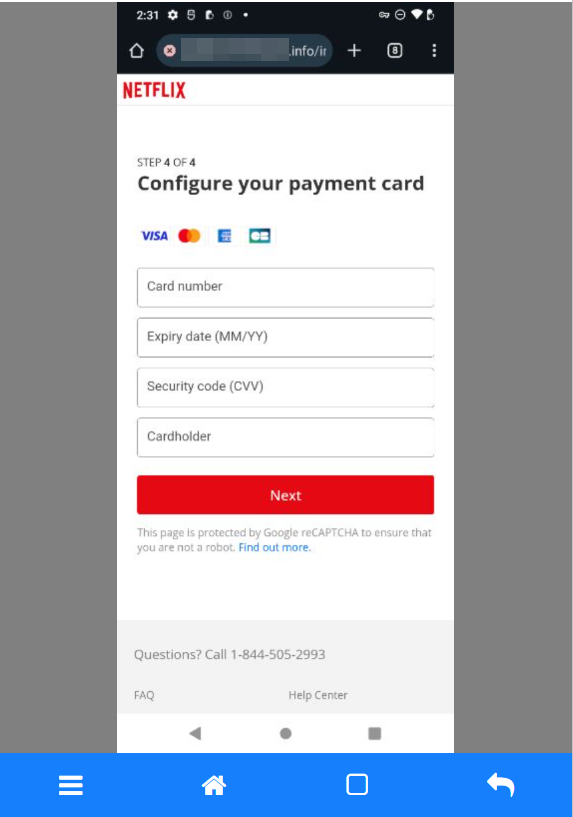
The attack has been completed, and the criminals now have access to all of the victim's information.
What's happening with the stolen data?
Netflix credentials and payment information will likely end up on the dark web, where they will be sold in bundles or as a single item.
Here's an example of a dark web store selling Netflix accounts, either stolen outright or purchased with stolen credit cards. The same will happen with the credit card information.

How to stay safe
· It's a good rule of thumb to never open links received from unknown sources, whether they are from an SMS or email.
· Always use a security solution on your devices. Never rely solely on the protection offered by the operating system. Security solutions such as Bitdefender Mobile Security offer a wide array of services besides scanning apps and downloaded files. One relevant feature is the option to scan incoming messages and warn users when they are targeted by scams.
· Keep in mind that Netflix doesn't send SMS messages.
· Companies don't send messages with ultimatums or accompanied by a sense of urgency.
· Don't follow links in messages. If you are unsure about a message, either SMS, email or otherwise, you can always manually input the address in a browser and check your account.
· You're still safe if you accessed the link but didn't input any information. But if you offered the attackers Netflix credentials and personal information, change the password as soon as possible and cancel the compromised card.

tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








