Nine of the Most Deceiving Malware Threats of 2014
2014`s cybersecurity events ” high-level security breaches, large scale vulnerabilities and endless privacy debates – have reshaped the world`s perception of digital safety. No one feels truly safe anymore.
Behind every cyber tragedy lies a malicious piece of code designed to cause as much damage as possible – to steal identities, corporate secrets or simply to prove a point. In hopes of a safer 2015, we`re showing you cybercrime`s leading actors and how much cyber-chaos they created this year. Check out the infographic version here.
1. DYRE as “The Banker”
Banking Trojan targeting world banks to steal sensitive user credentials and financial data. Spreads through spam and phishing campaigns. A malicious email, sent to bank employees, contains ZIP, PPT or PDF attachments or malicious short links that lead to compromised servers that hose malicious files. The files drop Dyreza on the target machine, which connects to a list of domains to install the malicious executable.
Performs man-in-the-middle attacks to intercept unencrypted traffic and capture login information. The data is sent to servers controlled by hackers. The known victims’ list includes several Switzerland banks and SalesForce.com.
SAFETY TIP. Don`t click links in e-mails from unknown e-mail addresses. Most online scams spread through this method.
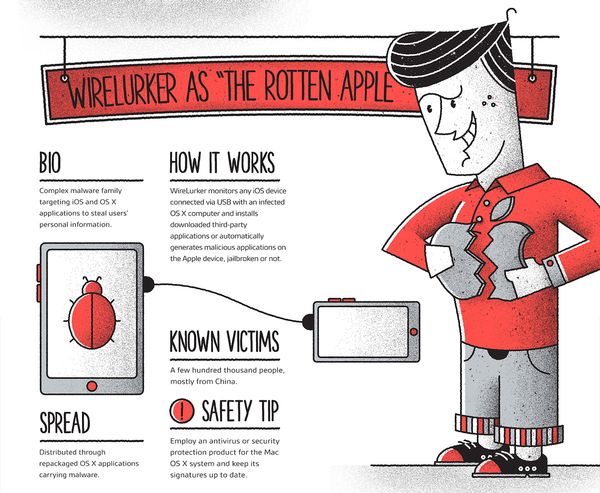
3. WIRELURKER as “The Rotten Apple”
Complex malware family targeting iOS and OS X applications to steal users` personal information. Distributed through repackaged OS X applications carrying malware. WireLurker monitors any iOS device connected via USB with an infected OS X computer and installs downloaded third-party applications or automatically generates malicious applications on the Apple device, jailbroken or not. Infected victims are mostly based in China.
SAFETY TIP. Employ an antivirus or security protection product for the Mac OS X system and keep its signatures up to date.
4. KOLER as “The Policeman”
Android Trojan extorting mobile device users for money to unlock their data. Posing as a valid video player offering premium access to pornography, it downloads automatically during a browsing session. After the drive-by Trojan infects a machine, it prevents the user from accessing mobile home screens and displays a bogus message purporting to be from the national police service. It claims the user has been monitored accessing child abuse websites and demands payment to escape prosecution. It was directed mainly towards European users.
SAFETY TIP. Installing a mobile security solution will help protect mobile devices from hacking, malware, viruses and unauthorized access.
5. CRYPTOLOCKER as “The Thief”
Prolific Ransomware Trojan using encryption to lock computer files and demanding the user to pay a ransom to decrypt them. Comes bundled with spam messages carrying a malicious attachment. If users open the attachment, the malicious .exe file is downloaded and executed. When CryptoLocker gains access to a computer, it connects to randomly generated domains to download a 2048-bit RSA public key used to encrypt computer files. The RSA public key can only be decrypted with its corresponding private key, which is hidden to make decryption almost impossible.
Cryptolocker is known to have infected more than 500,000 users, mostly from the US, UK and Canada.
SAFETY TIP. Ensure your operating system and security software are regularly updated.
6. PUSHDO as “Friend of Zeus”
Multi-purpose Trojan Pushdo uses private and public keys to protect communication between the bots and the command and control (C&C) center. The Pushdo Trojan has been used to distribute secondary malware strains such as ZeuS and SpyEye and spam.
Once machines are infected with Pushdo, the botnet is used to deliver malicious emails with links to websites that foist on users banking Trojans, such as Zeus, Torpig and Bugat. Sometimes, the messages are made to look like credit card statements or they contain an attachment disguised as an order confirmation. It has compromised more than 180,000 unique IP addresses from India, Indonesia, Turkey, UK, France and the US.
SAFETY TIP. Enterprises also need to maintain patch levels and run strong antimalware on all systems.
8. KELIHOS as “The Spy”
Trojan capable of mining sensitive browser data, internet traffic, Bitcoin wallets and sending spam emails. Spreads through spam messages, sent to those who dislike economic and political measures taken against Russia, claiming to offer an app that attacks governmental agencies responsible for economic sanctions against Russia.
After clicking the malicious links or attachments, victims download an executable file that installs the Trojan. The Trojan then communicates with the (C&C) center by exchanging encrypted messages via HTTP to retrieve further instructions.Victims are known to come from the Ukraine, Russia, Taiwan, Japan and India.
SAFETY TIP. Don`t install apps from suspicious third parties.
9. GAMEOVER ZEUS as “The Father”
GameOver Zeus is a peer-to-peer variant of the Zeus family of bank credential-stealing malware, typically spreading through phishing emails posing as invoices.
Once infected users visit their banking website through a compromised computer, Gameover Zeus intercepts their online session using the man-in-the-browser (MITB) technique. It can bypass two-factor authentication and display fraudulent banking security messages to obtain information for transaction authorization. As soon as the attackers get these details, they can modify the users` banking transactions and steal their money. GameOver Zeus has infected an estimated 500,000 to 1 million PCs from US, India, Singapore, Japan, Germany, Ukraine, Belarus and elsewhere.
INTERESTING FACT! It was used as a distribution platform for CryptoLocker.
SAFETY TIP. Banks and other reputable institutions do not request financial information via email, so don`t reply to unrequested emails.
Looking at the anatomy of the modern security threat, we can safely say that:
Companies have become the focus of targeted attacks. Attacks against infrastructures have become increasingly sophisticated. Attackers want to take advantage of the reputation and availability of the wide attack surface area to launch ever-larger cybercrime campaigns and exfiltrate valuable data. Also, though the June takedown of the Zeus botnet temporarily stopped the spread of Cryptolocker, ransomware as a whole continues to evolve and is moving to new platforms and OS systems. Not surprisingly, financial data remains among the most valuable and targeted information, and the methods to capture it have become more elaborate.
What should we expect from 2015?
Mobile payment technologies will bring new security challenges. The introduction of Apple Pay and similar technologies (NFC) will develop new techniques to intercept financial data.
Botnet anonymization will further help cybercriminals make huge profits. Using Tor anonymization and multi-tier proxies to communicate and to command an entire network of “zombies” is a new trend that raises serious concerns about how large infrastructures could be dismantled.
Vulnerabilities in open source software and intentional backdoors in technology products will continue to be exploited by malicious actors.
Mobile spear-phishing attacks targeting employees move mainstream. The widespread use of personal smart devices connecting to enterprise networks will continue to be exploited to access enterprise systems.
Cybercrime, operating like a legitimate, sophisticated business network, will continue to profit from selling crimeware kits on specialized forums and black markets.
tags
Author
Alexandra started writing about IT at the dawn of the decade - when an iPad was an eye-injury patch, we were minus Google+ and we all had Jobs.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks










