SEC Twitter hack blamed on SIM swap attack

The US Securities & Exchange Comission (SEC) has confirmed that hackers managed to seize control of a phone number associated with its Twitter account, and used it to post an unauthorised message.
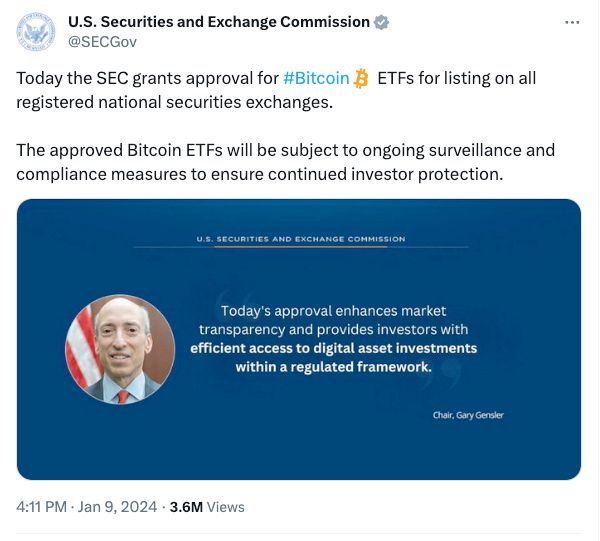
The unauthorised announcement to the SEC's 660,000 Twitter followers earlier this month claimed that a much-anticipated approval of Bitcoin ETFs had been granted, and caused a temporary leap in the value of the cryptocurrency.
When the truth emerged, the price of Bitcoin fell back, meaning that some investors would have made losses - while others, presumably, profited from the fake news.
The SEC announced that it had genuinely Bitcoin ETFs the following day.
So, how did the hackers hijack the SEC's Twitter account?
Here is what the SEC says happened:
Six months prior to the hack, the SEC disabled two-factor authentication (2FA) on its Twitter account.
At a later date, hackers managed to seize control of the cell phone number associated with the SEC's Twitter account through a "SIM swap" attack. This is where a scammer succeeds in tricking staff of a cellphone provider into giving them control of someone else’s phone number. Sometimes this is done by a fraudster reciting personal information about their target to the telecoms company, tricking them into believing they are someone they’re not.
Unfortunately for the SEC, Twitter makes it possible to reset an account password just by knowing and having access to its associated mobile phone number.
With the hacker now in control of the account, they were free to reset the account's password, and post the unauthorised message.
So, why did the SEC disable 2FA on its Twitter account in the first place? The SEC hasn't said, but Twitter warned in February 2023 that accounts risked being locked out of their accounts if they did not disable SMS text message 2FA.
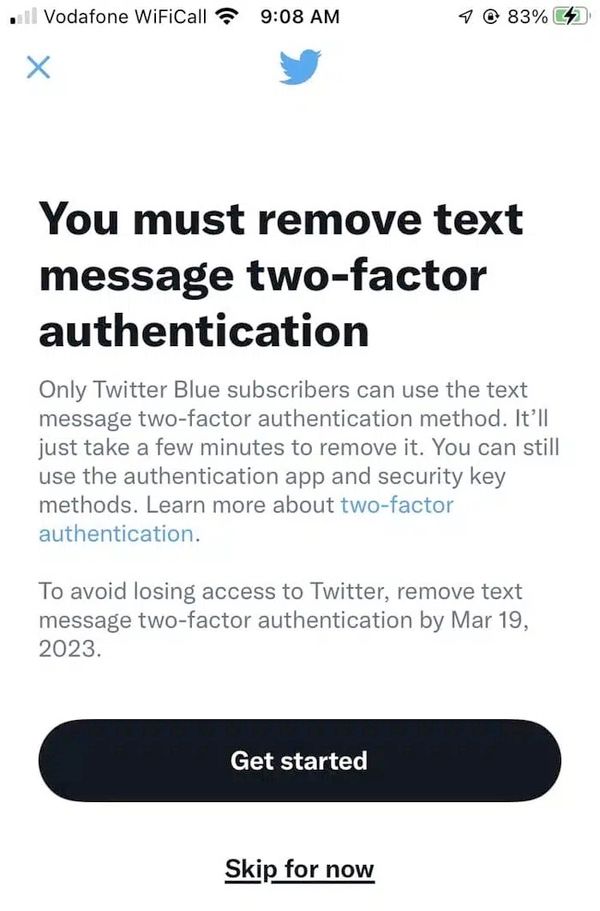
The reason? Twitter wanted its users to pay up for a Twitter Blue subscription, and - in what I considered a dangerous move - Twitter presented SMS-based 2FA as a premium feature. (The reality is that for years SMS text messages has been considered a less secure way of implementing 2FA than alternatives, and so offering it as a premium feature sent a very poor message in my opinion).
Sure enough, in March 2023 Twitter removed SMS-based 2FA from all accounts other than those which had paid for a Twitter Blue subscription. Anyone who still had SMS-based 2FA enabled, and was unwilling to reach into their wallet to pay Twitter was locked out of their accounts.
The SEC says that it used to have 2FA enabled on its account, but asked Twitter support to disable it after it found it was unable to access its account in July 2023. Unfortunately, the SEC did not re-enable the security feature afterwards (although since the unauthorised tweet it has enabled 2FA - hopefully not in its SMS-based form - on all its accounts).
All in all, it's a right mess. And particularly embarrassing for the SEC.
Not only is the SEC in the habit of rapping the knuckles of companies who have not taken appropriate steps to secure themselves against hackers, but its own chairman was tweeting about the importance of multi-factor authentication at a time when the SEC's own account was not protected by it.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








