Spammed Malware Campaign Targets Citi Group Customers
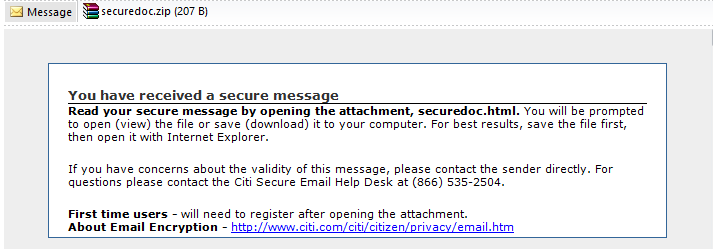
Clients of Citi Group, the third largest bank holding company in the US, are targeted by scammers who collect passwords and open backdoors for unauthorized remote attackers or download malware on the compromised systems.
This attack seems part of a greater campaign conducted by the group behind other two malicious spam messages that in January had Better Business Bureau and DocuSign clients open malicious attachment sworn to be legitimate, confidential and time sensitive.
Now it’s time Citi clients keep an eye open for e-mails that read “You have received a secure message” inviting them to read the message by opening the attachments securedoc.html.
The emails include a link and an attachment. While the link is harmless, taking receivers to the legitimate Citi page, the attachment is a password stealer that opens a backdoor for remote attackers. Some instances appear to also download components of the BlackHole or ZeuS exploit kits.
Untrained eyes could fall for this trick, since these e-mails are written in good English, with decent grammar and harmless-looking attachments.
Of the countless ways of infecting a computer, spam delivering malware continues to pay off despite restless efforts of media and the security community. Infecting PCs via spam proves an efficient dissemination method, since users are still caught off-guard by malicious links or attachments such as this message addressed to Citi Group clients.
All product and company names mentioned herein are for identification purposes only and are the property of, and may be trademarks of, their respective owners.
tags
Author
A blend of product manager and journalist with a pinch of e-threat analysis, Loredana writes mostly about malware and spam. She believes that most errors happen between the keyboard and the chair.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









