Zero-Day Razer Bug Lets Non-Admin Windows Users Gain SYSTEM Privileges
A security researcher has found that Razer peripherals suffer from a nasty flaw that allows any user to plug in the vendor’s gaming gear and easily escalate their privileges to the SYSTEM layer.
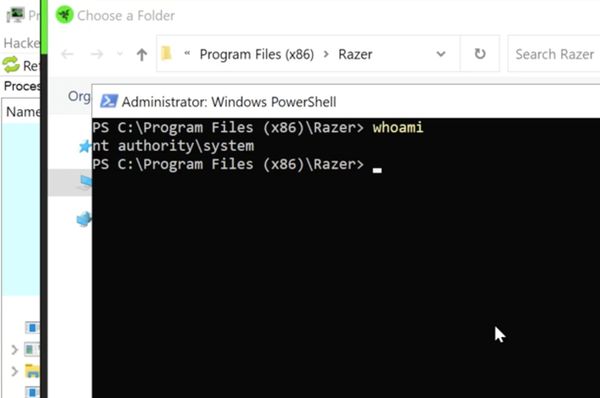
The researcher, jonhat, Tweeted that by simply plugging in a Razer mouse (or the dongle of a wireless peripheral), Windows automatically downloads and executes RazerInstaller as SYSTEM.
Need local admin and have physical access?
— jonhat (@j0nh4t) August 21, 2021
- Plug a Razer mouse (or the dongle)
- Windows Update will download and execute RazerInstaller as SYSTEM
- Abuse elevated Explorer to open Powershell with Shift+Right click
Tried contacting @Razer, but no answers. So here's a freebie pic.twitter.com/xDkl87RCmz
As avid Windows users will know, this can happen even if the current user doesn’t have administrator rights on the computer.
The installation wizard allows users to specify the folder where they wish to install the driver. To escalate their privileges, the user simply has to Shift - right click on the dialog box and choose “Open PowerShell window here.” From here on, the user can run anything as admin (not just Razer software), including malware.
The researcher released a proof-of of-concept video showing how the flaw can be easily exploited using the steps described above.
Furthermore, an attacker can gain persistence using the controllable path method to save a malicious service binary on the local host, jonhat tweeted.
He claims Razer failed to respond to his discovery so he decided to released it publicly. Shortly thereafter, Razer contacted the researcher with the promise of a fix and a bug-bounty reward - despite jonhat publicly disclosing the issue.
Some researchers, like Will Dormann at CERT, believe there are many similar products out there that suffer from the same flaw, considering that many vendors automatically load software when their products are plugged in.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








