A Comprehensive Look at the Evolution of the Cybercriminal Underground

The early days of hacker groups and lone wolf threat actors look much different compared to today. Gone are the days of the bragging rights hacks that were (relatively) harmless. Now threat actors work as part of well-oiled organizations, racking up millions per year by outright compromising organizations or lending their services to other, less-skilled adversaries.
Part of effective cybersecurity requires an understanding of how these cybercriminal organizations work. By delving into their evolution, tactics, and structure, security teams stay a step ahead in protecting their organizations. Let's uncover the origins and operations of these modern-day cybercriminal syndicates.
How the Cybercriminal Underground Evolved
In the early days, hackers were limited by what they could physically do to computers, often spreading viruses via floppy disks. This era marked the start of Bitdefender's journey. Initially operating under a different name, the company developed an internal antivirus solution to protect their clients and themselves. The effectiveness of this antivirus led to high demand, ultimately establishing Bitdefender as the renowned cybersecurity company it is today.
As time passed and the world became more connected, threat actors created malicious software – Trojans, viruses, worms, and more while antivirus publishers continued to update and develop their solution to identify, detect, and protect against these latest threats. On the enterprise side, we still saw companies being targeted simply for bragging rights or just to see if a hacker had the skills to successfully compromise a company.
In the early 2000s, cybercriminals started to have loftier goals, conscripting devices to their botnets and launching more significant attacks using more sophisticated methods like APT and DDoS attacks. In the 2010s, we saw nation-state hacking groups and more organization hacking groups emerge, with ransomware becoming a major enterprise threat.
These days, cybercrime is driven by profit, and we’ve seen a major transformation in the dynamics of hacker groups. They’re well organized, are much larger, have a hierarchy that lets them work efficiently, and have become their own industry.
This has been driven by a few major advances such as:
- A wider, digital attack surface: Gone are the days of the cat and mouse virus/antivirus dynamic. Hacker groups now have multiple avenues of compromising a company. They can attack employees via social engineering or phishing, find their way in by targeting a weaker third-party vendor, or find their way in via leaked credentials.
- The emergence of dark web marketplaces: The evolution of dark web marketplaces commoditized cyberattacks, putting a literal price on leaked data, and further incentivizing attacks that lead to data breaches.
- Data breaches beget more data breaches: Leaked data can be bought or stolen and then reused to attack other organizations who have lax security or whose employees reuse passwords.
- Private communication platforms: Cybercriminals are benefiting from anonymity like never before. The explosion of encrypted communication platforms like WhatsApp, Signal, and Telegram have facilitated more efficient activity because the content of the communication is encrypted, making it easier for groups to discuss attacks, compromises, and plans.
- Cryptocurrency: Cryptocurrency has made it much easier to cover one’s tracks, engage in ransomware attacks, and participate in the dark web. Cryptocurrency and cryptocurrency exchanges have also been found to be used for money laundering purposes.
- Higher and higher payouts: Cybercrime is now a $1.5T/year industry and every successive attack further incentivizes profit-driven threat actors. This is most apparent when we look at ransomware - payments have skyrocketed as has the rate of payments.
The Cybercriminal Underground Today
Cybercriminal organizations look much like legitinate organizations these days and that’s largely because the scope of their work has expanded dramatically. The largest cybercriminal groups lend out their services to other organizations, nation-states, and other adversaries.
Just like with modern businesses, cybercrime organizations vary widely in scale.
- Independent: These can be single individuals or small groups who engage in low level and/or unsophisticated attacks. Because law enforcement is unlikely to look for and catch this smaller actor, they can easily get away with a few attacks a year and make a substantial amount of money.
- Small to medium: These are the most common groups in the cybercrime market and look to sell their services to other threat actors. Larger groups are more organized, but they generally employ staff either on a full-time or part-time basis to handle support tickets, customers, and carry out service orders.
- Large/enterprise: Just like with modern businesses, cybercrime organizations come in much larger sizes. This is where famous groups like Conti, REvil, GozNym Gang and MageCart land, with the former making a net profit of $54M in 2021. These groups have over 50 “employees,” departmentalized, are salaried, and are even subject to performance reviews.
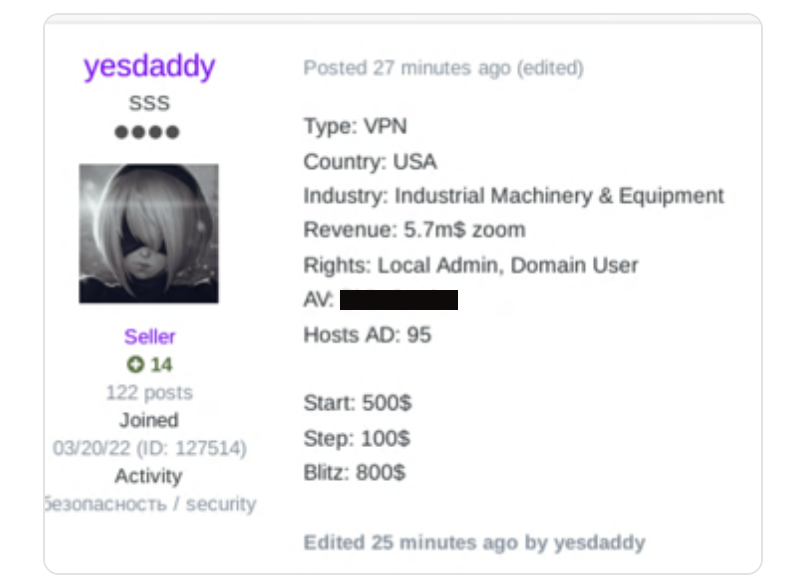
Example of an ad that promotes access to compromised organizations.
Hacker groups often make their money via the following:
- Selling exploit kits of known vulnerabilities.
- Selling stolen data - either as a data dump or as an individual asset (which can be used for identity theft or spearphishing attacks).
- Selling malware, ransomware, or other malicious content.
- Selling access to compromised organizations.
- Selling access to stolen data.
- Selling their services as a hacker group.
This last example is one of the more recent developments and how many major ransomware groups now operate.
-png-1.png)
Underground marketplaces tend to look and operate much like typical e-commerce sites.
In addition to ransomware operations, the cybercriminal underground has diversified its tactics and services. Here are some of the key components driving their activities today:
Money Mules
Money mules are individuals who transfer or move illegally acquired money on behalf of others, often as part of larger money laundering schemes. These individuals, who may or may not be aware of their involvement in criminal activity, are typically recruited through job advertisements, social media, or personal relationships. Once recruited, they receive stolen or illicitly obtained funds into their bank accounts, withdraw the cash, and then wire the money to another account, usually abroad, or convert it into cryptocurrency. By using money mules, criminals can obscure the money trail, making it harder for law enforcement agencies to trace the origin of the illicit funds and identify the main perpetrators. This practice not only facilitates various forms of financial crime but also exposes the money mules themselves to significant legal risks, including potential charges of money laundering and fraud.
SPAM and Phishing Services
Spam and phishing services for hire represent a significant and growing threat in the cybercrime landscape. These illicit services, often advertised on dark web forums and through underground networks, offer criminals the tools and infrastructure needed to conduct mass email spam campaigns and sophisticated phishing attacks. Clients of these services can purchase bulk email lists, access compromised servers for sending spam, and utilize phishing kits that create deceptive websites mimicking legitimate ones to steal sensitive information such as login credentials and financial details. The operators behind these services employ advanced techniques to bypass spam filters and avoid detection, enabling widespread dissemination of malicious content. By outsourcing their operations, cybercriminals can efficiently target vast numbers of potential victims, leading to significant financial losses and personal data breaches for individuals and organizations.
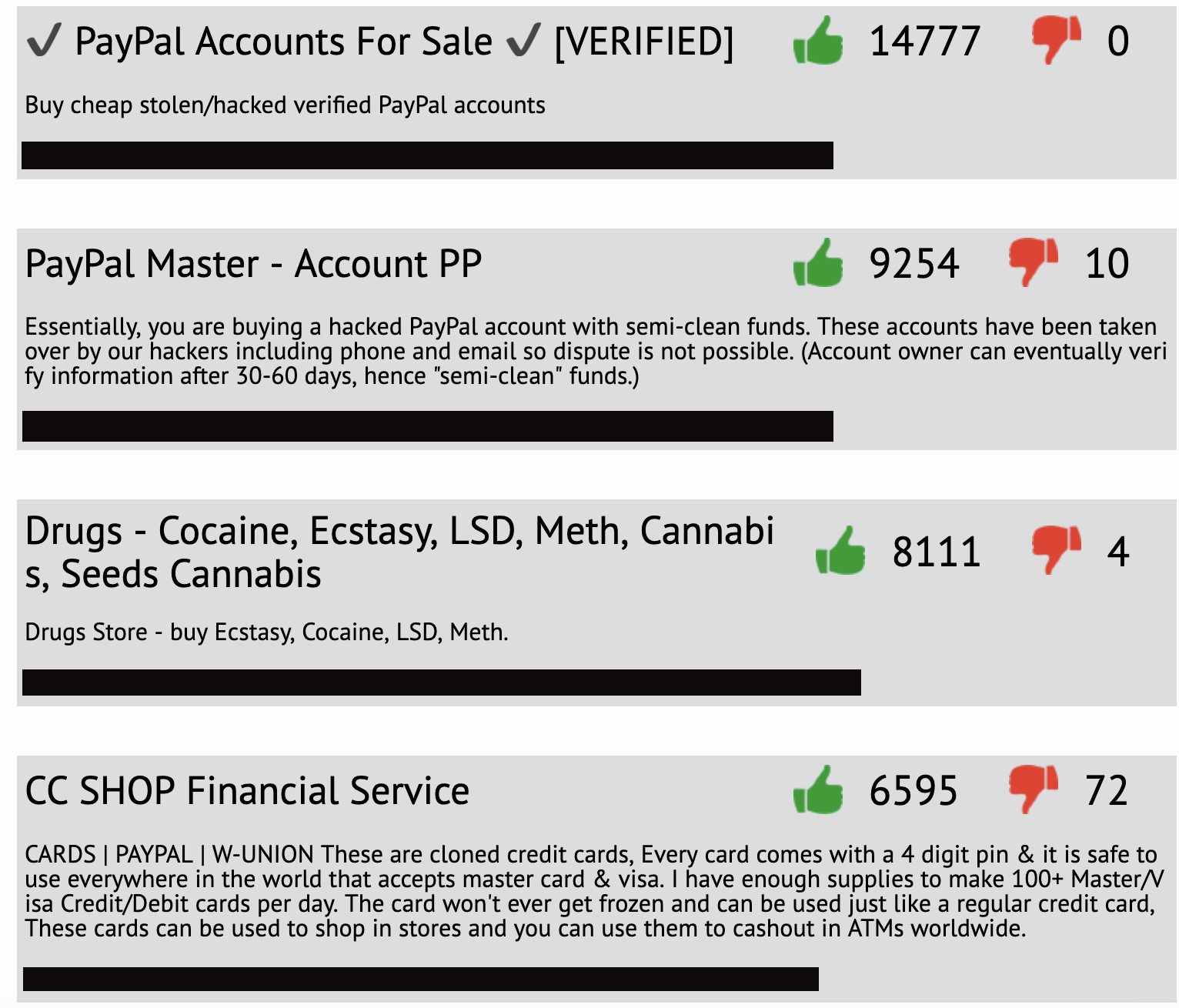
Visitors can access a variety of tools and services that come with a rating system.
Proxies for Hire
Proxies for hire, especially those used for malicious purposes, are a prevalent tool in the cybercriminal arsenal. These proxies often utilize networks of infected machines, including personal computers and Internet of Things (IoT) devices, to mask the true origin of malicious traffic. Cybercriminals leverage these compromised devices to launch a variety of attacks, such as distributed denial-of-service (DDoS) attacks, data breaches, and fraudulent activities, making it challenging for security systems to trace the malicious actions back to their source. By routing their activities through a network of unwitting proxies, attackers can evade detection, enhance their anonymity, and bypass geo-restrictions. The proliferation of IoT devices, many of which have weak security protocols, has significantly expanded the pool of potential proxies, further complicating efforts to combat this malicious practice.
Cryptocurrency Exchangers
Cryptocurrency exchangers that are not compliant with Know Your Customer (KYC) regulations play a significant role in the underground economy, providing a haven for illicit activities. These non-KYC compliant platforms allow users to buy, sell, and exchange digital currencies without verifying their identities, making them attractive to criminals who seek to launder money, evade taxes, or finance illegal operations. The anonymity these exchangers offer facilitates transactions involving stolen funds, ransomware payments, and illicit trade on dark web marketplaces. By circumventing regulatory oversight, these platforms undermine efforts to ensure transparency and accountability in the financial system, posing substantial risks to global financial integrity and security.
Non-KYC Compliant Hosting Services
Non-KYC compliant hosting services are a critical component in the infrastructure of cybercriminal operations, providing a cloak of anonymity for illicit online activities. These hosting providers do not require customers to verify their identities, making them ideal for hosting illegal websites, command and control servers for malware, phishing sites, and dark web marketplaces. The lack of KYC compliance allows cybercriminals to operate with minimal risk of detection, facilitating the distribution of malware, the sale of stolen data, and the orchestration of cyberattacks. By offering untraceable hosting solutions, these services undermine global cybersecurity efforts, enabling a wide range of digital crimes while evading law enforcement and regulatory scrutiny.
Escrow Services
Escrow services on the darknet play a crucial role in facilitating trust and ensuring transaction security among participants in illegal online marketplaces. These services act as intermediaries, holding funds from buyers until the agreed-upon goods or services, often illegal items such as drugs, weapons, or stolen data, are delivered and verified. By mitigating the risk of fraud, escrow services encourage more transactions and maintain the flow of commerce in these underground markets. Despite their intended purpose of ensuring fair dealings, these services inherently support and perpetuate illicit activities, making it difficult for law enforcement to track and intervene in the financial transactions associated with dark web trades. The anonymity and security offered by these escrow services contribute to the resilience and persistence of darknet marketplaces.
Advanced Persistent Threat (APT) Groups
Advanced Persistent Threat (APT) groups and state-sponsored hacking entities often mask their sophisticated cyber espionage campaigns as ransomware attacks or other forms of cyber fraud to obfuscate their true intentions and avoid detection. By mimicking the tactics, techniques, and procedures of common cybercriminals, these advanced actors can infiltrate target networks, exfiltrate sensitive data, and conduct surveillance while misleading defenders into thinking they are dealing with financially motivated cybercrime. This deceptive approach not only complicates attribution but also allows these groups to gather intelligence, disrupt operations, or manipulate data without arousing immediate suspicion. The use of such masquerading tactics underscores the complexity and evolving nature of cyber threats, highlighting the need for robust and nuanced cybersecurity measures to discern and counter these covert operations effectively.
-png-4.png)
Example of a rig exploit kit for sale.
Recent Advancements in the Cybercriminal Underground
In our research, we’ve discovered a few alarming patterns among these groups that suggest even more organized coordination and an eager willingness to adapt to new recent developments and a shifting landscape. Here’s what we’ve found:
An emergence of scamming farms: Due to the massive profits these organizations can make, they’ve resorted to kidnapping and trafficking people in countries like Thailand, forcing them to work in scamming factories and profiting from them.
Engaging in information sharing to avoid detection: Much in the same way the cybersecurity openly shares information to elevate security everywhere, cybercrime groups are also releasing educational information and notices about law enforcement tactics to prevent others from being caught.
Utilizing AI to elevate low-level scammers: Many ransomware groups live and die by their developer resources and decent programmers can utilize AI to improve efficiencies and become more productive. This can level up both low-sophistication and medium-sophistication scammers to an advanced state, making the entire cybercriminal landscape even more threatening. At the very least, this will facilitate even more scam attempts, further flooding organizations with attacks that may inevitably get through.
Staying Vigilant and Protected
There’s no single solution that will protect organizations from these well-organized organizations. Instead, by understanding how they work, what motivates them, and how they’re actively attacking organizations, you can make more informed decisions as you develop a comprehensive cyber resiliency strategy.
Remember that, for the most part, these threat actors are still looking to take advantage of low hanging fruit and organizations with poor security postures. If you do your due diligence to effectively secure your data, manage your assets, and minimize how much of a risk your employees are, you may be able to avoid being targeted.
Still interested in learning more? Don't miss this upcoming LinkedIn live event.
tags
Author

Josue Ledesma is a writer, filmmaker, and content marketer living in New York City. He covers cyber security, tech and finance, consumer privacy, and B2B digital marketing.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










