Bitdefender Threat Debrief | April 2025

In this month’s Threat Debrief: A rebrand of a rebrand as the Hunters International ransomware group recharts its course. We provide context detailing the group’s origins and factors motivating their actions in light of the recent development. Plus, we discuss a partnership between a Top 10 ransomware group and a secondary, supporting player in the ransomware landscape, and we're covering a new LockBit variant.
Ransomware is a moving target, constantly changing its tactics, and this monthly Bitdefender Threat Debrief helps you stay ahead of the curve. We combine our threat intelligence and insights on adversary behavior with supplementary data from openly available sources (OSINT) – from news reports and other research sources – with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It’s important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
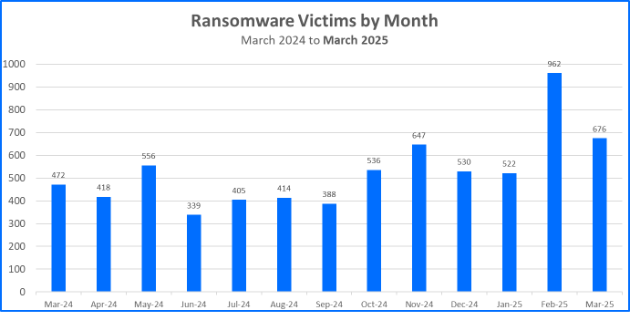
For this month's report, we analyzed data from March 1 to March 31 and recorded a total of 676 victims claimed.
Featured Story: A Hunters International Rebrand Stirs Suspicion
Hunters International is a RaaS (Ransomware as a Service) group that emerged in October of 2023. They originally started as a group that only performed data exfiltration. Hunters International added ransomware to their operations later.
Our findings indicated that Hunters International acquired tools from the Hive ransomware group and activities linked to Hunters International began nearly nine months after law enforcement seized Hive’s infrastructure in early 2023. Hive stopped their operations and Hunters International purchased their code and remaining infrastructure. Hunters International would modify Hive’s source code, notably improving the encryption process and simplifying the parameters and exclusions defined in command line arguments.
Recently, a research firm uncovered a divide within the group and a rebranding of Hunters International. The ransomware operator announced its closure in November of 2024 due to what they called risky and unpromising ransomware operations. Hunters International made multiple references to law enforcement operations designed to disrupt ransomware activities, including those executed in Moscow, that would supposedly reduce their odds of survival. And, the World Leaks group emerged shortly thereafter. They are most likely a rebrand of Hunters International and not a group that is operating independently of Hunters International or without their influence.
Hunters International remains active in March of 2025. We suspect that they will prioritize data exfiltration over the use of encryption. Over the past year, they claimed as many as 41 victim organizations, peaking during the month of April 2024. In the months that followed November 2024 (the so-called end of the group’s operations), Hunters International continued claiming a small number of victims. They claimed 9 victims during the months of December, January, and February. And this past March, Hunters International claimed 6 victims.
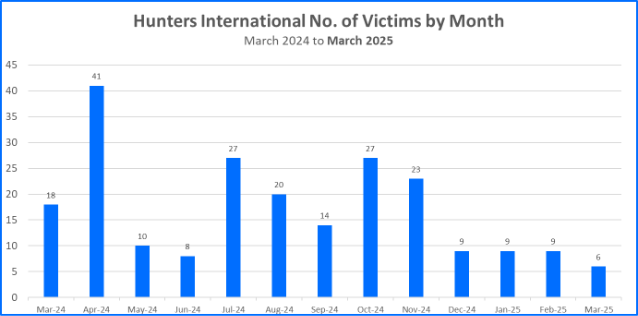
Lapses in ransomware activity may be attributed to planning amongst operators, restaffing, or matters like developing proof of concepts. Rebranding is another possibility, as groups typically try to accomplish the following:
- Reorganize after staff loss, internal conflicts, or looming investigations
- Rebuild a reputation to broaden the ransomware group’s appeal to emerging groups and potential affiliates
- Modify the MO and move to a new target or victim demographic
- Implement new capabilities, e.g. deploying ransomware from a new family
- Buy time to correct operational and/or tactical weaknesses
For a comprehensive understanding of the current ransomware playbook, including how these attacks are executed and how to defend against them, please read our Ransomware whitepaper.
Notable Ransomware News
Now, let’s explore other notable ransomware news and findings since our last Threat Debrief release.
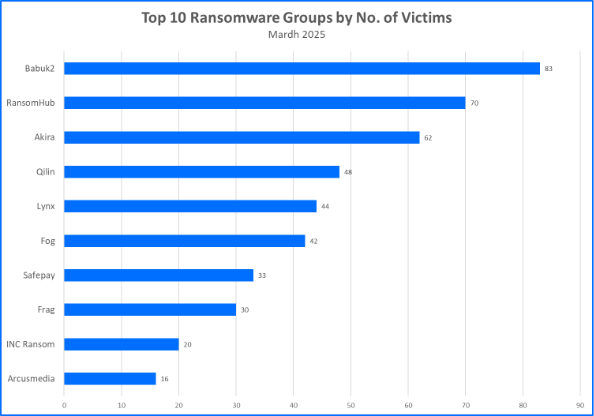
- Babuk2 places in the top rank in March.
Babuk2, also known by the alias Bjorka, claimed a total of 83 victims. The threat actor is known for leaking victim data rather than deploying ransomware. Babuk2 also has a history of engaging in revictimization, taking credit for victims claimed by other ransomware groups such as RansomHub, LockBit3, and FunkSec. Babuk2 initially expressed an interest in establishing an affiliate relationship with FunkSec. In January of 2025, a FunkSec Forum user named Bjorka shared a photo of a FunkSec tattoo in the hopes of receiving $1000 from the FunkSec admin.
- Mora_001 strikes with a LockBit variant.
Mora_001 is a threat actor that has leveraged SuperBlack in campaigns to exploit Fortinet vulnerabilities. The LockBit variant features code that’s similar to LockBit 3.0; however, the SuperBlack ransomware note and executable used to exfiltrate data are unique.
Mora_001 has exploited the authentication CVE-2024-55591 and CVE-2025-24472. Mora_001’s exploitation of CVE-2024-55591 in campaigns dates to late January. The vulnerability affects FortiOS version 7.0.0 through 7.0.16. It also affects FortiProxy version 7.0.0 through 7.0.19 and 7.2.0 through 7.2.12. A threat actor exploits this vulnerability by sending crafted responses to Node.js, allowing them to gain elevated privileges and execute unauthorized commands. Threat actors also exploit CVE-2025-24472 to gain elevated privileges by sending CSF proxy requests. The vulnerability affects FortiOS 7.0.0 through 7.0.16. It also affects FortiProxy 7.2.0 through 7.2.12 and 7.0.0 through 7.0.19. Organizations using products affected by these vulnerabilities are advised to review vendor notices and update to the patched versions of the software.
- LockBit developer Rostislav Panev is extradited to the U.S.
Panev is the seventh member of LockBit to be taken into custody. He has multiple allegations associated with his role in organizing and overseeing LockBit RaaS operations from 2019 to early 2024. Investigations are ongoing and the US Department of State’s Transnational Organized Crime (TOC) Rewards Program offers a monetary reward of up to $10 million for information that leads to the arrest or conviction of LockBit members.
- RansomHub moves its infrastructure to DragonForce.
RansomHub is a group that has dominated the Top 10 Groups, claiming more than 850 victims in the past year. It recently announced a collaboration with DragonForce. It is not known when RansomHub’s infrastructure will be back up on their own site. While this collaboration may appear unusual, it’s a potential indicator of oncoming changes to RansomHub’s TTPs and OPSEC objectives. DragonForce claimed 121 victims in the past 12 months.
- RansomHub implements a backdoor with improved capabilities.
RansomHub is using a custom tool named Betrugger; it’s a backdoor equipped with functionalities that include not only keylogging and network scanning but also privilege escalation and exfiltration capabilities. RansomHub is known for using EDRKillShifter to disable defenses; the EDR killer was shared amongst affiliates and identified in attacks executed by Play, BianLian, and Medusa.
- Everest ransomware is taken offline.
Everest is a ransomware group that emerged in 2020. Everest has accumulated more than 200 victims since that time across the healthcare, finance, and manufacturing sectors. The group is known for leaking customer data, company records, banking information, and personally identifiable information. Everest’s data leak site was defaced with the message: Don't do crime CRIME IS BAD xoxo from Prague. Researchers believe that a flaw impacting WordPress, the service used to host Everest’s data leak site, allowed a threat actor to access the infrastructure. At the time of this release, the onion site remains offline.
- Several new ransomware groups enter the ecosystem.
Newcomers to the ransomware ecosystem, discovered in recent campaigns, include VanHelsing, Arkana, Secp0, CrazyHunter, Weyhro, NightSpire, and Frag. The groups Frag and NightSpire claimed the greatest number of attacks across new groups in March. Frag claimed 30 victims and NightSpire claimed 14 victims.
Top 10 Ransomware Families March 2025
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
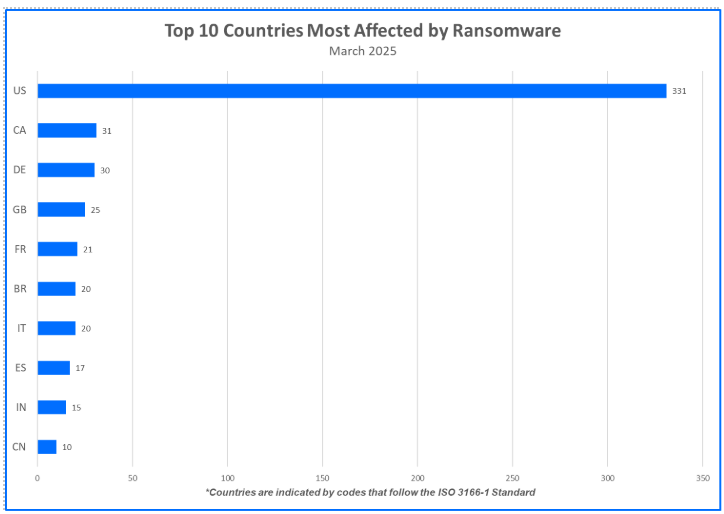
Top 10 Countries Targeted by Ransomware March 2025
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
About Bitdefender
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu for their help putting this report together.
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks








