Bitdefender Threat Debrief | December 2024

As organizations face increasing ransomware activity in the final months of 2024, the importance of maintaining robust cybersecurity strategies has never been clearer. Understanding how threat actors evolve their tactics is crucial to protecting critical data and systems. In this month’s Threat Debrief, we examined ransomware group activity from November 1 to November 30, uncovering 647 claimed victims across their leak sites.
Now, let’s explore some notable news and events since our last issue:
- Arrest Made in Connection to Cyberattacks on U.S. Critical Infrastructure:
Mikhail Pavlovich Matveev, a ransomware developer linked to operations associated with LockBit and Babuk, has been arrested by Russian authorities. Mateev had been the subject of an intensive search lasting nearly two years. The FBI previously announced a substantial bounty of $10 million for his capture, citing charges of computer intrusion and conspiracy. With the cybercriminal now facing imprisonment in Russia, some speculate whether his sentence will be comparable to or harsher than those of REvIl group members sentenced earlier this year, who received prison terms ranging from four to six years. - INTERPOL Operation Seizes Over $400 Million:
INTERPOL has conducted several significant operations to combat cybercrime in 2024, including Operation HAECHI V. This operation successfully identified thousands of cybercriminals, including individuals from China and North Korea involved in phishing scams and business email compromise schemes. Financial fraud cases were also uncovered, including stablecoin fraud. This scheme assigns a fixed value to a virtual currency to entice victims into setting up accounts via phishing links, allowing attackers to access their funds. - Ymir Ransomware Employs Unique Execution Tactics:
Ymir ransomware exhibits an unusual approach to execution compared to other ransomware families. It exploits memory management functions such asmalloc,memmove, andmemcmpto execute its code, thereby reducing the likelihood of detection by traditional antivirus and endpoint detection and response (EDR) solutions, which often rely on identifying disk-based signatures and processes. Ymir is typically deployed after RustyStealer compromises systems, stealing credentials and enabling further attacks. The ransomware uses the ChaCha20 encryption algorithm and appends the extension.6C5oy2dVr6to affected files. - Akira Executes Record Number of Attacks in November:
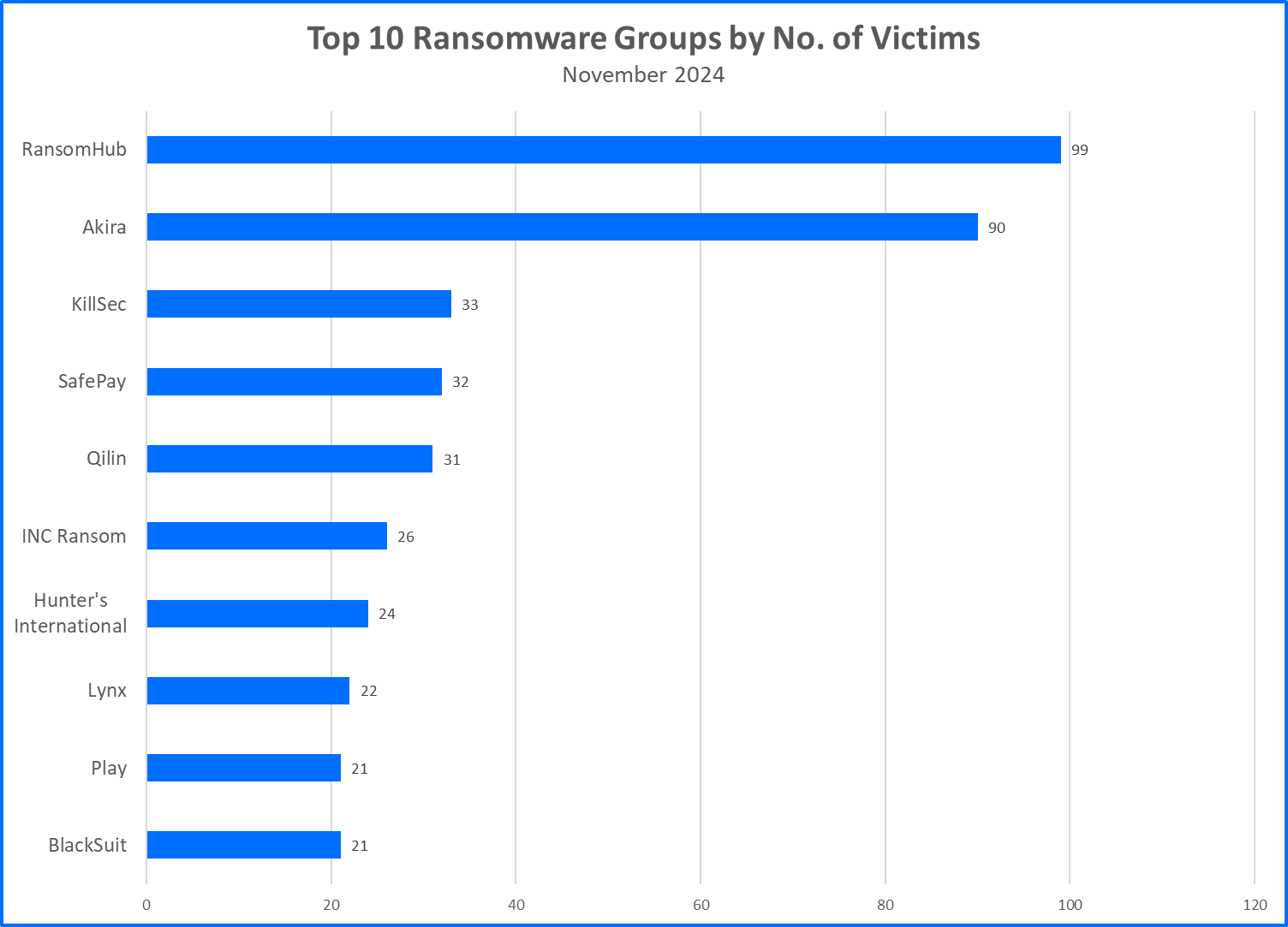
Akira ransomware experienced a dramatic increase in activity last month, with Bitdefender documenting 90 victims in November alone—far surpassing its previous monthly high of 30 attacks in July. Active since March 2023, Akira is a rapidly evolving threat group with the potential for significant growth in the coming year. - CyberVolk adopts the RaaS model:
CyberVolk, a Russian-aligned hacktivist group, has expanded its operations by adopting the Ransomware-as-a-Service (RaaS) model. In addition to ransomware, the group has launched DDoS attacks against targeted organizations. Despite its geopolitical ties to Russian interests, some reports suggest CyberVolk's activities may also involve actors in India. - KillSec and SafePay Climb Into Top 10 Ransomware Groups:
KillSec and SafePay are two ransomware groups gaining prominence. KillSec, a Russian hacktivist group that launched a RaaS program this past summer, also markets services such as penetration testing and OSINT collection. Meanwhile, SafePay, which uses ransomware with similarities to LockBit, leverages a LockBit builder for its operations. The group employs additional techniques such as using WinRAR and FileZilla for data exfiltration and “living off the land” tactics, including launchingSystemSettingsAdminFlowsto disable defenses. - BianLian Pivots from Encryption:
Active since 2022, BianLian has shifted its focus from encrypting victim files to exfiltrating data. Recent attacks no longer involve appending the.bianlianextension to compromised files. Instead, BianLian employs PowerShell scripts and Rclone to steal data. A recent advisory by CISA highlights the group’s updated tactics. - Helldown ransomware variant targets Linux systems:
Helldown, a ransomware group active since August 2024, has developed a new Linux variant. The group exploits vulnerabilities in Zyxel VPN and firewall products, including CVE-2024-42057, which allows for command injection attacks. Helldown’s operations also include credential theft. Users of Zyxel products are strongly advised to apply the latest patches and enforce robust password policies, including regular password updates.
Top 10 Ransomware Families
Bitdefender’s Threat Debrief analyzes data from ransomware leak sites, where attacker groups publicize their claimed number of compromised companies. This approach provides valuable insights into the overall activity of the RaaS market. However, there’s a trade-off; while it reflects attackers’ self-proclaimed success, the information comes directly from criminals and might be unreliable. Additionally, this method only captures the number of claimed victims, not the actual financial impact of these attacks.
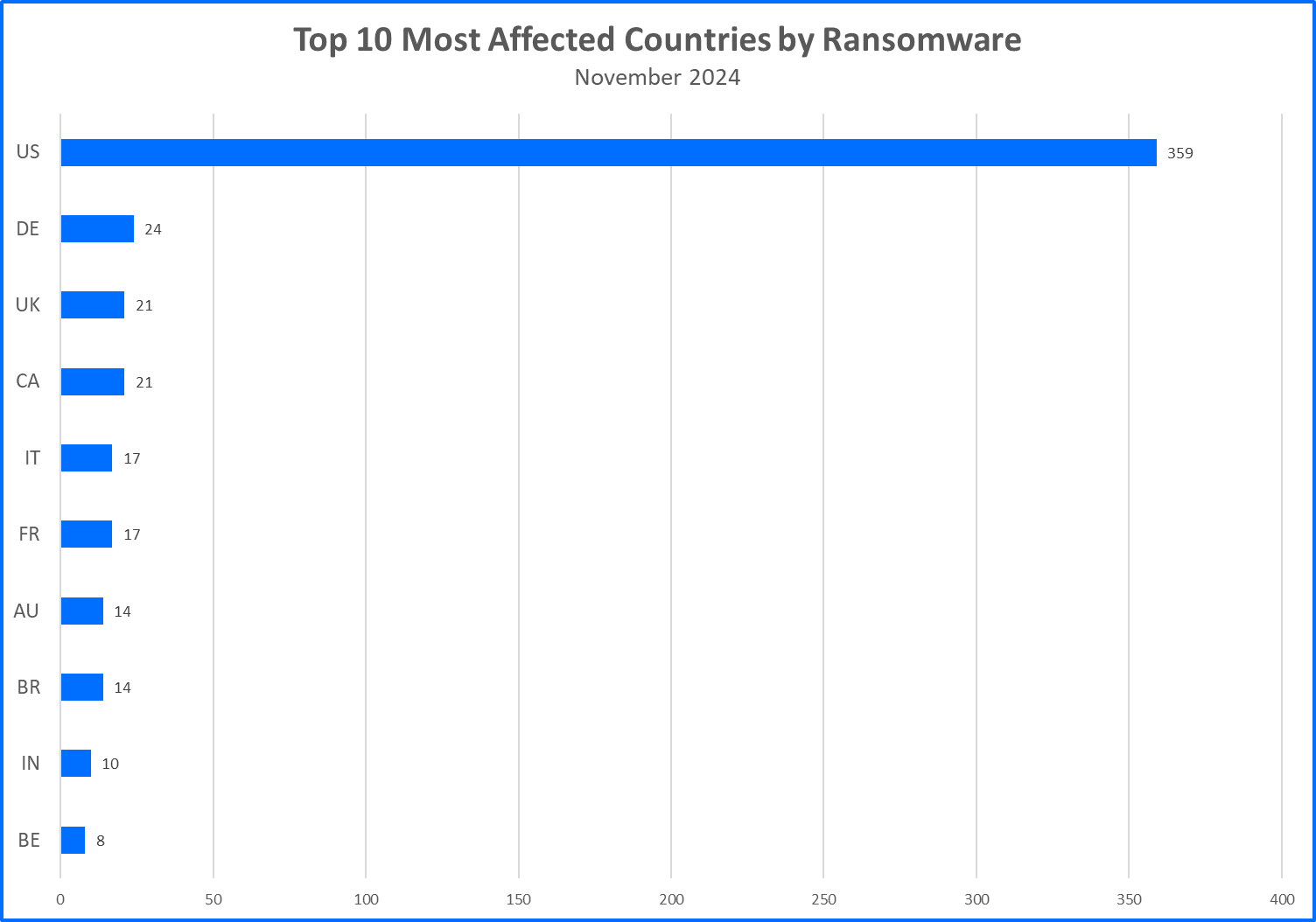
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help with putting this report together.
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









