Bitdefender Threat Debrief | November 2024

Ransomware attacks continue to inflict significant harm on organizations, leading to financial and operational disruptions that are often both severe and avoidable. Accessing up-to-date data on top ransomware threats is essential for identifying trends in victim profiles, attack tactics, and other elements that shape the threat landscape. From October 1 to November 1, our analysis of ransomware group websites revealed a total of 593 claimed victims.
Now, let’s explore notable news and findings since our last Threat Debrief release.
- REvil Criminals Receive Prison Sentences: A Russian court issued the final ruling on the four REvil members found guilty of malware distribution and money laundering. The threat actors face sentences that range from four and a half to six years, with the REvil leader, Daniil Puzyrevsky, serving the longest sentence. The investigations preceding the REvil member arrests and the efforts undertaken by the prosecution are significant milestones amidst crackdowns on Russian cybercrime. However, there’s uncertainty about the state of REvil’s operations and whether the group, anticipating law enforcement interference, decided to reorganize or rebrand.
- RansomHub Claims More Victims Than LockBit: RansomHub has accumulated more than 450 victims since the first reports of RansomHub incidents back in February of 2024. The group has maintained a steady number of monthly attacks. In comparison, LockBit’s victim count has declined over time. The expected drop can be attributed to law enforcement’s successful seizure of a LockBit domain earlier this year.
- Jump Pices Operation Supported By Play: Jump Pices, an advanced persistent threat (APT) has been associated with the ransomware group Play. Jumpy Pices is a state-sponsored North Korean threat group. According to recent reports, they successfully launched a series of attacks by accessing compromised user accounts, perfuming additional credential harvesting processes, and then deploying Play ransomware and exploitation framework tools. Whether an affiliate type of relationship has been established to allow Jump Pices to use Play remains unknown.
- Black Basta Devises Attacks Over Microsoft Teams: Black Basta has engaged in social engineering tactics where they masquerade as “Help Desk” in their emails and messages to victims over Microsoft Teams. Once the threat group offers support to resolve spam issues and convinces end-users to click a link, AnyDesk is downloaded. The use of QuickAssist to execute payloads with anti-spam software names, including the names AntispamAccount and Antispam Update was also reported. And Black Basta uses Cobalt Strike to establish lateral movement.
- New Operators in the Double Extortion World: Emerging ransomware groups, including InterLOck, HellCat, and KillSec have recently claimed victims. While their victim numbers are lower in comparison to groups with an established history, these variants demonstrate an important lesson. Most groups that are capable of performing essential reconnaissance, infiltrating victim networks, executing ransomware, and managing a data leak site are dangerous enough and have the potential to become even greater threats over time.
- PaidMemes Rolls Out BabyLockerKZ: BabyLockerKZ is a ransomware variant derived from MedusaLocker. BabyLockerKZ has been tied to attacks against small and medium businesses, notably in South America. The MedusaLocker variant is associated with PaidMemes, who acts as an Access Broker; the unique run key also sports the same name. The first incidents connected to PaidMemes indicate that the group has been active since 2022; they would start a pattern of attacks that leveraged BabyLockerKZ nearly a year later in late 2023.
- Threat Researchers Unveil Cicada3301’s Affiliate Platform: Researchers from Group-IB identified communications from the ransomware group Cicada3301 on the Russian Anonymous Markekerplace forum. The researchers corresponded with the threat actor and infiltrated the environment, accessing key information, including Cicada3301’s affiliate panel and ransomware customization options. Multiple organizations have been hit by the Cicada3301 ransomware since the first few incidents were reported this past summer. They continue to be a group to monitor as they implement interesting tactics to grow their operations.
- Qilin Variant Has Stealthier Capabilities: B, a Qilin ransomware variant, has been linked to attacks against healthcare organizations. The variant’s defense evasion methods and encryption options, including AES-256-CTR, distinguish Qilin.B from its former iteration. The ransomware strain employs multiple payloads and shares some similarities with the Embargo ransomware. One such similarity is Qilin.B’s use of MS4Killer to disrupt EDR activities; this is a utility written in the Rust language and it is launched following the execution of the loader named MDeployer.
- Crypt Ghouls Deploys Prominent Ransomware: Crypt Ghouls is a ransomware group that has previously abused common tools to deliver payloads and modify victim infrastructure such as PowerShell and malicious RMMs. However, recent reports indicate that the threat actor executes ransomware such as LockBit 3.o and Babuk. Crypt Ghouls has developed a history of campaigns against Russian organizations. Regardless of whether Crypt Ghouls has active connections with a LockBit affiliate or is crafting a ransomware payload-based on leaked LockBit code, LockBit has not fallen out of use.
- NotLockBit Targets Not-Windows Systems: NotLockBit has executed attacks against systems with macOS. Features of the ransomware include system discovery and reconnaissance capabilities and asymmetric encryption. Once executed, a LockBit 2.0 desktop theme is also loaded on infected devices. While it was once presumed that NotLockBit used code from a LockBit builder, that claim is now understood as false. Attacks by NotLockBit began in spring of 2022. With reports of a significant threat actor hitting macOS systems, more developments in macOS attacks are likely to take shape.
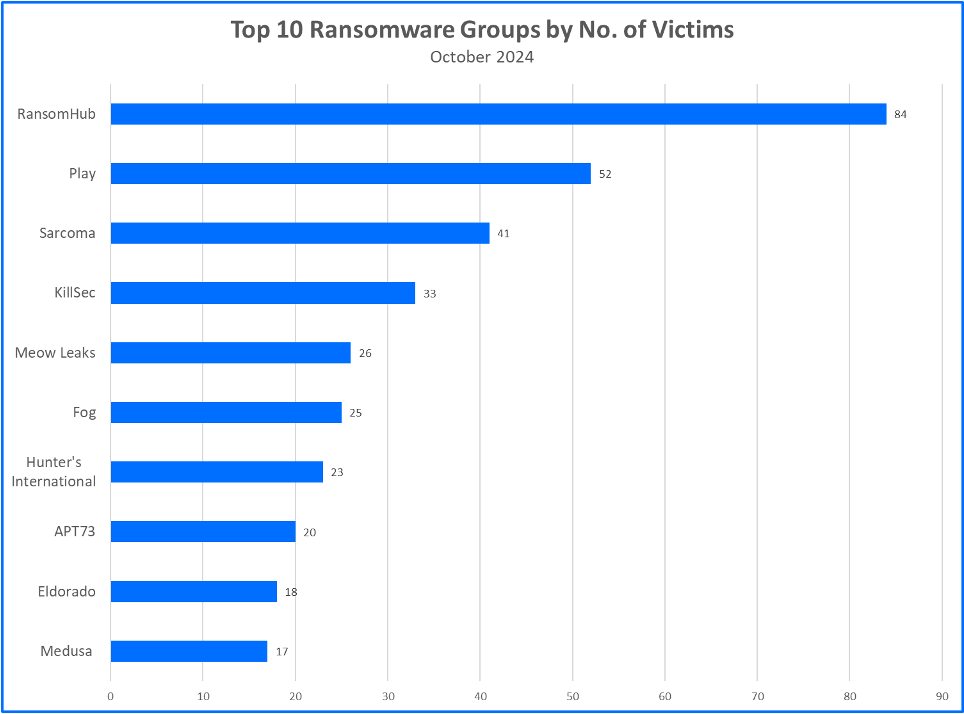
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where attacker groups publicize their claimed number of compromised companies. This approach provides valuable insights into the overall activity of the RaaS market. However, there's a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and might be unreliable. Additionally, this method only captures the number of claimed victims, not the actual financial impact of these attacks.
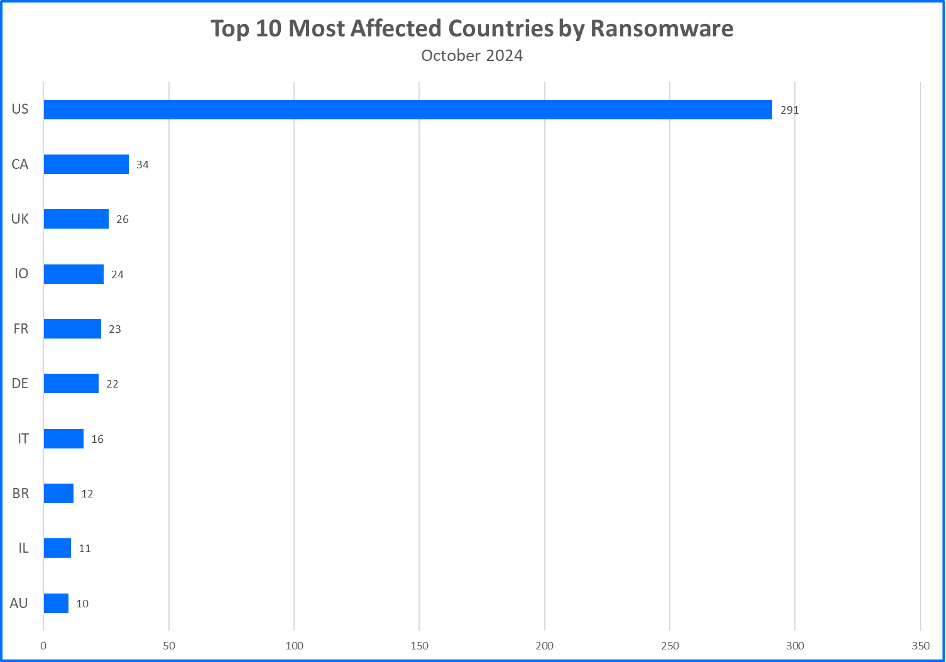
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help with putting this report together.
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks








.jpg)