Stop shifting the blame onto third parties. That breach is still your firm’s responsibility

If it’s data that your customers gave you that’s breached, it’s your responsibility.
It doesn’t matter if your company hired a third-party to process the data on your behalf, or the data was stored on a web server managed by a third-party company you hired to handle it. It’s your responsibility.
So, stop trying to shift the blame.
Yes, there’s no doubt that the third-party may have let the side down. Maybe they didn’t have decent security in place, maybe they dropped the ball when it came to building the website securely or keeping up-to-date with patches.
But it was your company’s decision to hire them.
You trusted them with, for instance, your customers’ personal information. Your customers trusted you to treat their data with the utmost care, and were probably never consciously aware that you would be sharing it with a third party in the first place.
I’m sorry to be so “tough love” about this, but these thoughts were high on my mind when I read about a recent security breach which has impacted some 43,000 people.
ABTA, the UK’s Association or British Travel Agents, issued a statement last week revealing that a data breach had compromised the information of approximately 43,000 holidaymakers.
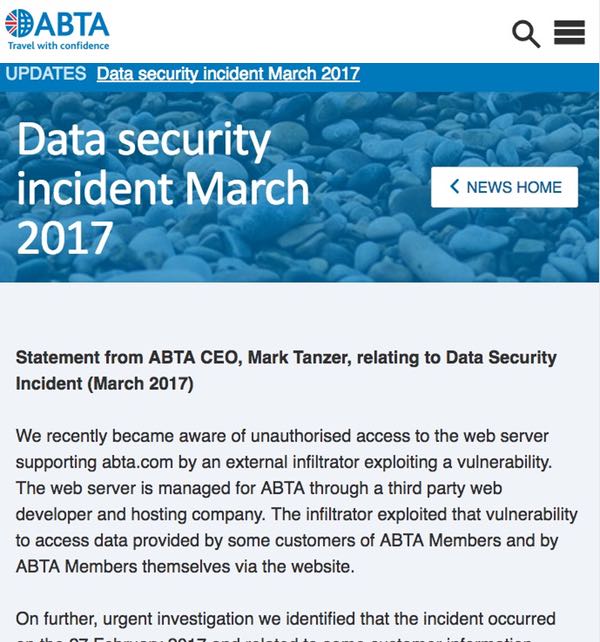
According to ABTA, the breach occurred on 27 February 2017, and saw hackers exploit a vulnerability on abta.com, “which is managed for ABTA through a third-party web developer and hosting company.”
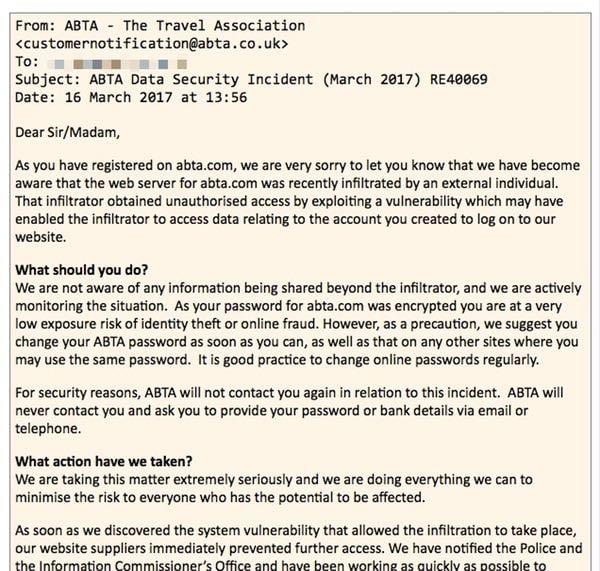
Most of the affected 43,000 holidaymakers find themselves in unpleasantly hot water because they had registered accounts on the abta.com website or filled in online forms to submit a complaint about an ABTA member.
As a consequence, thousands of people have had their email addresses, encrypted passwords (ABTA doesn’t tell us if the passwords were encrypted and hashed, the hashing algorithm that was used, or whether the hashes were salted - all of which would be useful to know) and contact details fall into the hands of hackers.
Furthermore, around 1000 files containing individuals’ personal identity information uploaded in support of complaints about travel agents were exposed.
In its advisory, and in its notification email to users, ABTA underlines that the affected web server was under the management of an unnamed “third party web developer and hosting company”.
That may be accurate but legally it’s not a way of wriggling out of the blame.
As an article in Security Week points out - in the eyes of the UK’s Information Commisioner’s Office (ICO), the data controller (ABTA) retains responsibility regardless of the contracted third-party data processor (the web-hosting company).
It should go without saying that if you are an ABTA member, or might have shared personal information with the ABTA website, that you should change your password – and ensure that you are not using the same password anywhere else on the net.
There is little you can do to prevent firms being more careful about who they entrust with your personal information, but you can – at least – attempt to lessen the impact when future breaches occur.
tags
Author

Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










