How to Make the Most Out of Your Security Solutions

While digital transformation and the e-commerce bubble in late '90s have reshaped the way companies do business, increasingly sophisticated cyber-attacks call for immediate and sometimes overly complex defenses. Security tool vendors have been more than willing to provide an ever expanding array of tools and technologies, many with dubious value.
At their finest hour, CISOs face vulnerable endpoints, mobile workforce, a diverse infrastructure and human error. At their darkest, they face business meltdown and career termination. This constant pressure forces many to reassess their cybersecurity spending, their strategy and how they address the increasing security skills gap. Meanwhile, large-scale, highly sophisticated attacks are already crippling high-profile infrastructures worldwide and exposing customer data for hackers to leverage into ransom or sell to third parties.
Executive sleeping positions... pic.twitter.com/gKQ8VOBuZo
— Matt Eastwood (@matteastwood) December 15, 2018
Email and browsers are among the most vulnerable endpoint applications hackers target. Financial services, healthcare and technology have traditionally been the most targeted industries, and they’re not so strong on security. A report by Generali Global Assistance (GGA) and Identity Theft Resource Center (ITRC), found that “financial services firms fall victim to cybersecurity attacks 300 times more frequently than businesses in other industries.”
According to the Bitdefender Global Mid-Year Threat Landscape Report, companies struggled with much more sophisticated vulnerabilities throughout 2018. New ransomware families and variants keep popping up, with medium and large businesses among the preferred targets. It only takes one missed sample – or a stolen domain account - and the entire organization gets held for ransom.
And it’s not just the “bad guys” that put pressure on the IT security team. SOC teams either crash under alert fatigue as they are monitoring EDR software or struggle to monitor several technologies reporting in their own pane of glass. A Ponemon Institute survey ran in 2018 shows that organizations have an average of seven different software agents installed on their endpoints to enable IT management and security, making endpoint management noisy and time-consuming.
Which brings us to the real problem.
When budgeting for security tools, most CISOs would only take into account the predictable part of the spectrum: purchase price, some level of support and renewal costs. But the total cost of ownership of an EPP solution goes well beyond that. It also includes the entire lifecycle of a solution, such as those associated with operations and retirement, emergency intervention, triaging threats and temporary loss of business when computers get rebuilt.
Endpoint security has grown into a major business concern but an ongoing roadblock is that managers don’t always understand the total cost of ownership (TCO). They often end up making the wrong decisions under imminent budget constraints, but which later fail to address the growing cybersecurity talent gap, reduce costs or offer proactive protection.
Total Cost – First Year Analysis
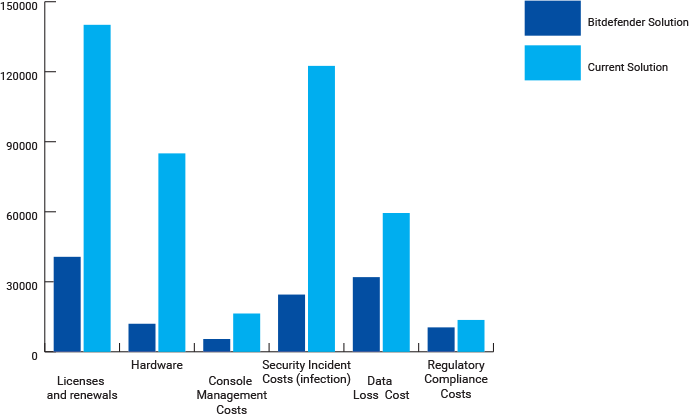
Total Cost – Three Year Analysis
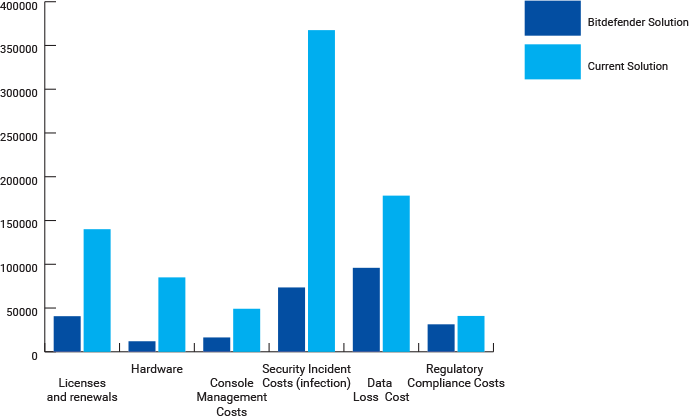
When a company is at risk, it needs the right talent and protection that can overcome even the newest cyber threats. The demand for security professionals is now higher than ever, and it will surely increase across all sectors in coming years. By 2021 the labor market will count 3.5 million vacant positions, likely to be filled by junior analysts instead of senior security experts. The resulting lack of proper knowledge and experience to effectively contain and control cyber threats will leave businesses more vulnerable to targeted attacks.
In 2018, the Ponemon Institute found that the average total cost of a data breach is $3.86 million, and financial institutions face the highest recovery cost, at about $.35 million per breach. $125 is the disinfection cost for a single PC, says the same research.
According to CISOs in the financial sector, the best approach to defending against advanced attacks in their organization is next-generation security (endpoint detection and response capabilities) (67.8%), security audits (46.6%), traditional security (antimalware and endpoint protection solutions) (41.5%), layered security (24.6%), log monitoring (22.9%) and cybersecurity trainings (22%).
A US-based university that has recently switched to Bitdefender’s technology has reduced their overall cost by 48%. If an organization has poor detection rates and lacks web security, they will have a higher infection rate. The likelihood of malicious attacks and data breaches is reduced with integrated capabilities and a superior detection rate. Compared to hardware solutions, switching to a SaaS platform can help companies save time and money without paying an arm and a leg to procure, update and manage.
Deploying a large number of traditional agents to protect an elaborate IT system is no silver bullet against malicious intruders and the current polymorphic malware landscape. Businesses need more than simple first-line security at the device level which, in any case, can lead to system overload and operational burden or failure to detect sophisticated attacks. Sometimes extensive investments in hardware and time-consuming manual labor don’t bring the desired results, so companies have to reorganize to find a cost-effective integrated solution for threat detection and response.
tags
Author

From a young age, Luana knew she wanted to become a writer. After having addressed topics such as NFC, startups, and tech innovation, she has now shifted focus to internet security, with a keen interest in smart homes and IoT threats. Luana is a supporter of women in tech and has a passion for entrepreneurship, technology, and startup culture.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











