No More Ransom – Six Years of Innovating to Fight Ransomware Together

When talking about cybercrime, you can’t avoid the topic of ransomware. It is one of the few cybersecurity challenges discussed not only in the cybersecurity and tech communities, but also regularly appears in mainstream media headlines, board meetings, and even emergency support calls from family, friends, and neighbors.
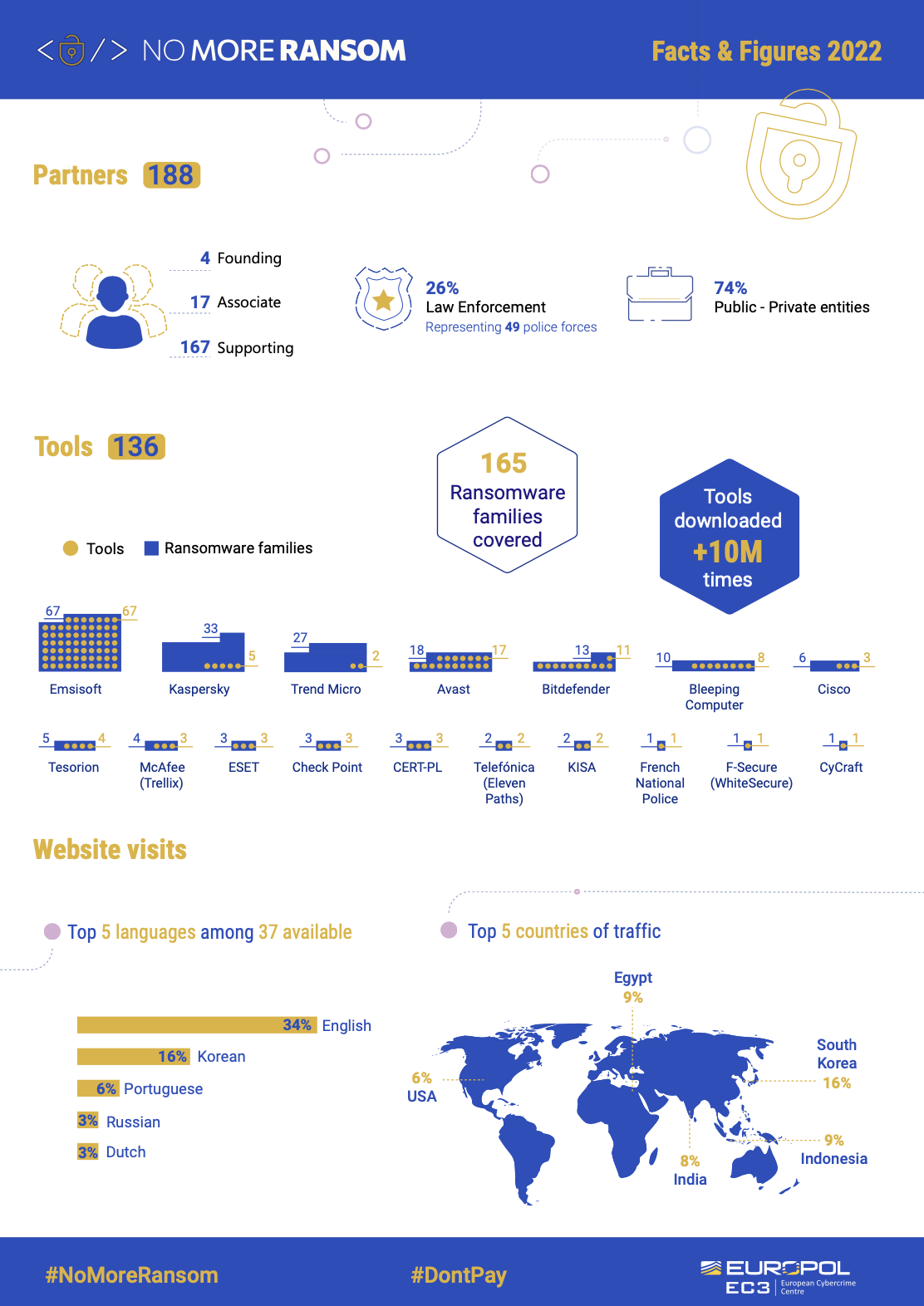
What can you do if your computer has been infected with ransomware, you’ve lost access to all your files, and you can’t restore your data from backups? One of the last remaining options is to head over to https://www.nomoreransom.org for helpful advice and tools to recover your files without paying the ransom. You upload a few samples of encrypted files and provide details from the ransom demand. Crypto Sheriff identifies the ransomware family and provides a link to a decryption tool if available. In total, decryption tools for 165 different ransomware families are available, which covers a wide range of possible malicious actors.
The No More Ransom initiative is one of the best examples of how private and public sectors can partner together for the betterment of everyone from individuals to large corporations. In total, 188 partners, including 49 police force units from around the world and many endpoint security vendors, have joined forces in this coordinated effort to help victims of ransomware attacks retrieve their encrypted data without having to pay the criminals. Bitdefender is proud to play a part in this ongoing initiative.
Recovering data and disrupting the cybercrime ecosystem
Ransomware is not a new threat – in fact, it has existed for over 30 years. As we celebrate the 6th anniversary of the No More Ransom project, it’s a good time to re-evaluate if it’s still relevant. After all, it started an entire year before WannaCry (still leading our charts) and the IT landscape has evolved dramatically since then.
The No More Ransom initiative is more relevant today than it was in 2016. The initial goal of the project was restoring access to encrypted data, but today it serves an even more important purpose – the disruption of the cybercrime ecosystem.
Modern ransomware is very different now than it was in 2016. The biggest change came with the introduction of the profit-sharing business model, referred to as Ransomware-as-a-Service (RaaS) in 2018. This “business model” is often explained as a simple renting of ransomware infrastructure, but that’s not an accurate description.
The world’s largest taxi company doesn’t own any cars (Uber). The world’s largest accommodation company doesn’t own any property (AirBnB). And some of the largest ransomware groups are not actually deploying their own ransomware. Instead, they work with independent contractors (affiliates), and share the profit after a ransom is paid. Often overlooked, but an important factor, is the revenue sharing ratio between the ransomware group and affiliates. While the RaaS group gets the most media attention, the independent affiliate keeps most of the profits (75-90%). In the last few years, the power has shifted from those who control the ransomware code to those who control access to networks and actively exploit them.
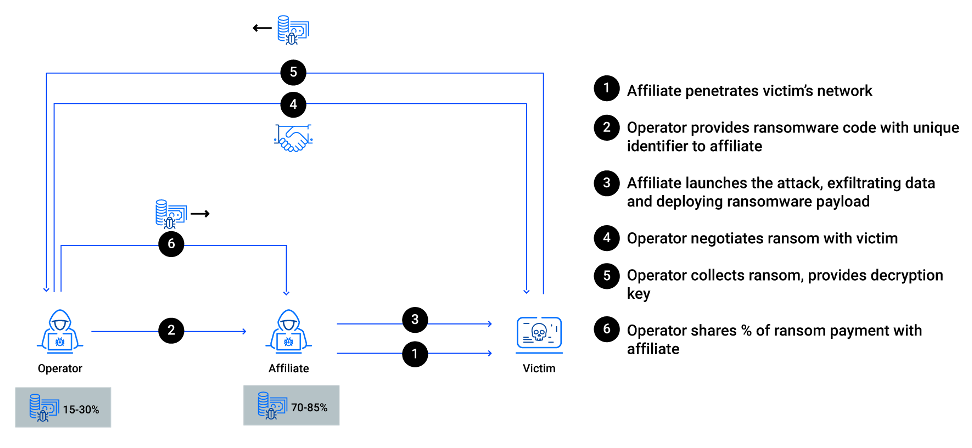
The most typical ransomware attack scenario involving a RaaS group. Percentages refer to the share of ransom payment for different personas.
Pay special attention to the flow of money in this model. While an affiliate is responsible for most of the work initially, it’s the ransomware group (also known as the operator or administrator) that negotiates with the victim and collects the ransom.
Ransomware decryptors disrupt the ransomware kill chain after affiliates are done with their job, but before an operator can collect the payment (between steps 3 and 5 in the diagram). An affiliate successfully infiltrated a network and prepared for weeks or months to launch an attack. Then, when the big day comes – no ransom is paid because data was recovered using a free-to-use decryptor.
To develop a decryptor, a vulnerability needs to be identified in the ransomware code, or a private key needs to be leaked from the RaaS group. An affiliate is going to blame the ransomware operator – after all, he/she has finished the job and expects a payment. How did the private key get out? How much potential revenue was lost? This can bring uncertainty to the trust relationship between these criminal partners (that’s a good thing!)

An internal investigation by the ransomware group GandCrab. Keeping threat actors uncertain about the source of the leak is an important disruption technique. Source: darknet forum
The initially requested ransom amount and what is finally paid are two very different things, as the payout can fluctuate. The actual amount can be higher (the ransom will usually double if you don't pay in a certain timeframe) or lower (if the victim refuses to pay or can recover the data from backups) than initially demanded. When the ransomware kill chain is interrupted by decryptors, affiliates blame ransomware operators, and demand to be compensated for their work. How do you calculate the cost of a lost opportunity, and who should pay for the work done, even if the ransom isn’t paid? Affiliates overestimate the potential loss, while ransomware operators tend to underestimate it. And the larger the sum, the bigger the dispute between affiliates and operators.
Bitdefender decryptors have saved victims nearly $1B USD in ransom payments
As Bitdefender is one of the top 5 contributors of decryptors to the No More Ransom project, we researched the actual amount these decryptors have saved for victims to date – so you can see just how helpful decryptors can be.
In September 2021, we released a free universal decryptor for REvil (a.k.a. Sodinokibi) in collaboration with a trusted law enforcement partner. This decryptor has helped more than 1,500 companies in 83 countries so far. As part of this operation, since victims submit the unique ransom notes as part of the recovery process, we can accurately calculate the total amount of ransom that was requested (and denied). Using this methodology, we can accurately attribute around $600M USD that was saved by just the REvil decryptor alone.
In our telemetry, REvil represents less than 1% of total downloads of decryptors. For the remaining decryptors (such as DarkSide or GandCrab), we used average ransom demands and telemetry data to estimate the total ransom payments. We estimate that all other decryptors combined saved an additional $350M USD.
While the requested amount multiplies in time (it usually doubles if you don't pay in a certain timeframe) and the amount saved could be a lot higher, our calculations are based strictly on the initial request. Even keeping our estimates conservative, the total amount of ransom payments that were prevented by our decryptors is around $950M USD.
If you want to learn more about what it takes to bring down a group like REvil, watch Fighting REvil: Insights from the Frontline with members of our elite Bitdefender DRACO threat intelligence team.
Ransomware best practices
Lowering ransomware risk is possible. Minimize your attack surface, implement automated prevention controls to prevent many types of security incidents and, for the few incidents that get through your defenses, rely on security operations, enhanced with strong detection and response tools.
Beyond this, the most important step is to understand how modern ransomware works. Watch our video about the Top 10 myths and misconceptions about ransomware, then read our ransomware technical whitepaper to learn about effective ransomware protection.
If you have fallen victim to ransomware, we recommend not paying the ransom as it helps fund future cybercriminal activities. Contact your police unit, and try to upload a few encrypted files to normoreransom.org to see if a decryptor is available. If you are a law enforcement agency in need of technical expertise in ransomware cases, please contact us at [email protected]. If you or your company have been affected by a ransomware attack, reach out to us at [email protected].
As cybercriminals are adopting profit-sharing models, they are becoming more specialized and better at coordinating their attacks. Disruption is one of the most effective methods to combat this trend and close collaboration between private and public sectors is critical to making today’s digital world more secure.
Learn more about Bitdefender’s Anti-ransomware solution.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











